Products You May Like
A newly discovered botnet capable of staging distributed denial-of-service (DDoS) attacks targeted unpatched Ribbon Communications (formerly Edgewater Networks) EdgeMarc appliances belonging to telecom service provider AT&T by exploiting a four-year-old flaw in the network appliances.
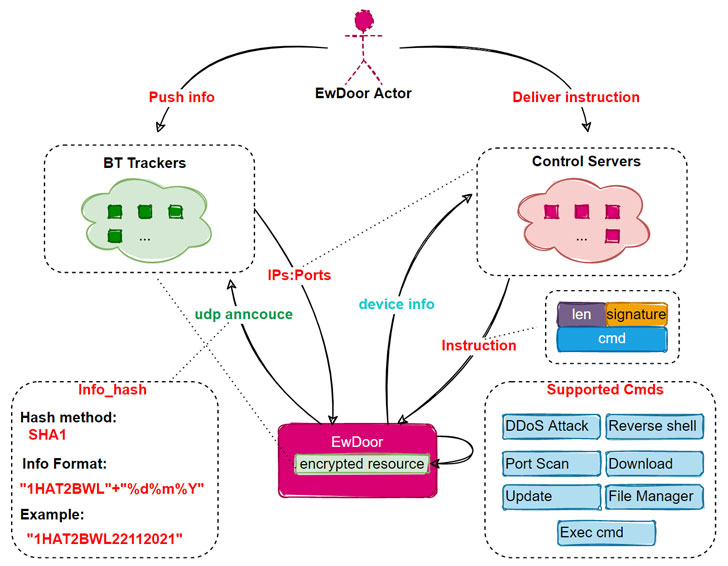
Chinese tech giant Qihoo 360’s Netlab network security division, which detected the botnet first on October 27, 2021, called it EwDoor, noting it observed 5,700 compromised IP addresses located in the U.S. during a brief three-hour window.
“So far, the EwDoor in our view has undergone three versions of updates, and its main functions can be summarized into two main categories of DDoS attacks and backdoor,” the researchers noted. “Based on the attacked devices are telephone communication related, we presume that its main purpose is DDoS attacks, and gathering of sensitive information, such as call logs.”
Propagating through a flaw in EdgeMarc devices, EwDoor supports a variety of features, including the ability to self-update, download files, obtain a reverse shell on the compromised machine, and execute arbitrary payloads. The vulnerability in question is CVE-2017-6079 (CVSS score: 9.8), a command injection flaw affecting the session border controllers that could be weaponized to execute malicious commands.
EwDoor, besides gathering information about the infected system, also establishes communications with a remote command-and-control (C2) server, either directly or indirectly using BitTorrent Trackers to fetch the C2 server IP address, to await further commands issued by the attackers.
We have reached out to AT&T for comment, and we will update the story when we hear back. Additional indicators of compromise associated with the campaign can be accessed here.