Products You May Like
Wing Security recently announced that basic third-party risk assessment is now available as a free product. But it raises the questions of how SaaS is connected to third-party risk management (TPRM) and what companies should do to ensure a proper SaaS-TPRM process is in place. In this article we will share 5 tips to manage the third-party risks associated with SaaS, but first…
What exactly is Third-Party Risk Management in SaaS?
SaaS is rapidly growing, offering businesses convenience, swift implementations, and valuable opportunities. However, this growth introduces a security challenge where risks arise from the interconnected nature of SaaS supply chains. It is clear that before onboarding a new contractor or vendor, we need due diligence, security checks, and referrals. However, we now understand that in the SaaS domain, applications are, in fact, the go-to vendor of choice.
Let’s explain: Any employee can very easily connect SaaS vendors to company data, granting them permissions and access. This easy onboarding is important for efficiency, scalability, and getting work done. But it also introduces plenty of security issues because most SaaS applications, unlike traditional vendors, often bypass or skip security or IT approval.
Third-party SaaS security solutions play a pivotal role in safeguarding an organization’s SaaS supply chain, and evaluating SaaS vendors becomes a crucial element of comprehensive vendor risk management. While some of the responsibility for security falls on the SaaS vendor, organizations must stay vigilant in managing third-party risks, irrespective of their size, to uphold a secure and robust business environment and to ensure they comply with industry standards.
In simple terms, Third-Party Risk Management in the context of SaaS is the process of evaluating and managing the potential risks posed by third-party vendors and service providers in the SaaS domain. TPRM helps security and IT teams identify and understand various types of risks coming through third-party services that relate to cybersecurity, including data privacy vulnerabilities, compliance gaps, operational issues, financial challenges, and reputational concerns.
Five TPRM tips to ensure SaaS Security
1. Identification and Categorization:
Identifying and categorizing third-party connections is a critical step for organizations to understand the potential threats these connections pose to security and compliance. A lack of systematic data collection and analysis on access levels and vendor security can leave security and IT teams in the dark, hindering their ability to assess and safely use specific third-party applications appropriately.
However, with SaaS Security Posture Management (SSPM) technology, organizations can overcome this challenge by easily discovering all their third-party SaaS applications. SSPM solutions provide contextual information on the level of access these applications have to organizational assets and details about the vendor’s security level based on continuous analysis.
 |
| Wing Security’s TPRM solution for SaaS applications |
2. Due Diligence and Assessment:
Conducting due diligence before onboarding applications is an essential step in ensuring that risky applications are not being introduced into an organization’s SaaS Stack. This maximizes the need to assess third-party security controls, policies, and procedures, ensuring they meet the required standards ahead of onboarding them.
To tackle this problem, organizations should look for a solution that can provide the necessary security and compliance information about relevant SaaS vendors/applications. Information such as security compliances, privacy compliances, vendor size, location, historic threat intelligence alerts regarding breaches or security incidents that the vendor had experienced, etc. This information is a major part of the due diligence process of third-party vendors.
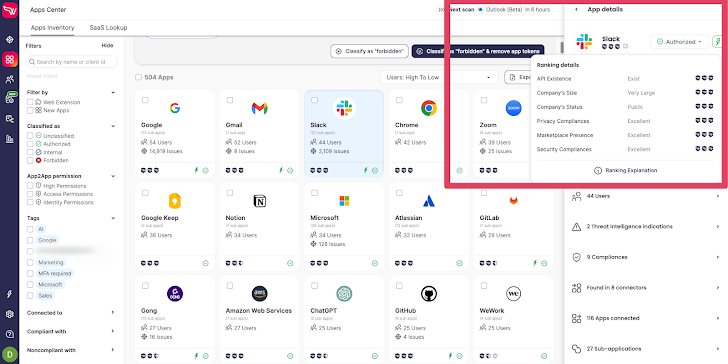 |
| Wing Security’s free discovery solution for SaaS applications |
3. Ongoing Monitoring:
Continuous monitoring is a key aspect of effective TPRM. Third-party risk Management does not stop only at the stage of prevention but also stresses the importance of regularly assessing third-party performance and security practices to ensure ongoing compliance and security with established standards. This proactive approach helps organizations stay ahead of evolving risks.
An effective way to deal with this is to have a security solution that is able to continuously monitor for updates in the vendors’ information including changes in security and privacy compliances, threat intelligence alerts, and its risk posture.
4. Incident Response:
In the event of a security incident that pertains to a third-party connection, organizations should ensure that a robust incident response plan is in place. It starts by having the ability to receive timely threat intelligence alerts when breaches or security incidents occur, enabling them to respond promptly and effectively.
5. Documentation and Reporting:
Maintaining detailed records of the TPRM process is essential for demonstrating compliance with security standards. Generating comprehensive reports is important because it provides transparency and facilitates smooth audits of the organization’s risk management efforts.
Organizations should opt for a solution that can manage the inventory of the entire organizational SaaS applications to date, view all the relevant information that supports the TRPM process, and export the relevant reports for audit purposes.
Consequences of inadequate TPRM practices:
Failing to implement proper Third-Party Risk Management practices can have severe consequences for organizations. Cybersecurity breaches resulting from vulnerabilities introduced by third-party vendors can lead to the exposure of sensitive data, financial theft, and reputational damage. Non-compliance with data privacy regulations can attract hefty fines and legal liabilities.
What is to gain from TPRM?
Effective TPRM practices offer numerous benefits. It empowers security teams to identify and address potential risks, leading to improved security and compliance. Strengthened vendor relationships enhance trust and collaboration, while the ability to demonstrate proper due diligence helps navigate regulatory requirements more effectively.
Ultimately, Third-Party Risk Management is a crucial process that involves identifying and mitigating potential vulnerabilities introduced by third-party vendors. TPRM plays a vital role in strengthening an organization’s overall security posture by ensuring adherence to regulatory compliance and best security practices throughout the entire SaaS supply chain.
This proactive approach is essential for securing organizations against SaaS threats, as it involves evaluating the cybersecurity practices of third-party vendors to identify potential vulnerabilities and risks in the supply chain. These assessments facilitate informed decision-making and risk mitigation and ensure alignment with the organization’s security standards, ultimately fortifying the overall security defenses.
That said, today, vendor risk assessments are critical but not enough. It’s essential to have both the capabilities to assess and mitigate risk. By starting with thorough third-party risk assessments, companies can gain the necessary insights to take the next steps in proactively addressing risks and ensuring a secure and well-protected SaaS supply chain.
