Products You May Like
Microsoft is warning of an increase in adversary-in-the-middle (AiTM) phishing techniques, which are being propagated as part of the phishing-as-a-service (PhaaS) cybercrime model.
In addition to an uptick in AiTM-capable PhaaS platforms, the tech giant noted that existing phishing services like PerSwaysion are incorporating AiTM capabilities.
“This development in the PhaaS ecosystem enables attackers to conduct high-volume phishing campaigns that attempt to circumvent MFA protections at scale,” the Microsoft Threat Intelligence team said in a series of posts on X (formerly Twitter).

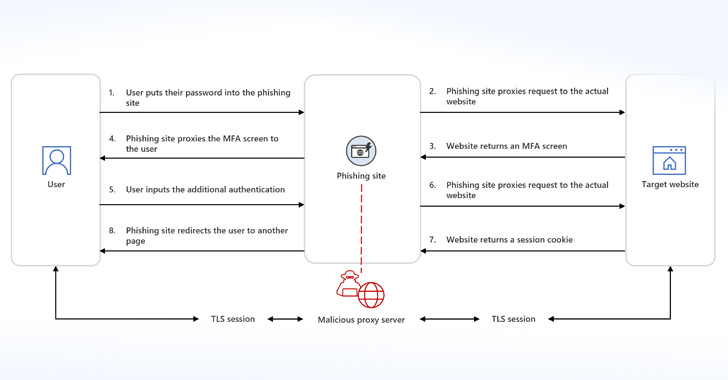
Phishing kits with AiTM capabilities work in two ways, one of which concerns the use of reverse proxy servers (i.e., the phishing page) to relay traffic to and from the client and legitimate website and stealthily capture user credentials, two-factor authentication codes, and session cookies.
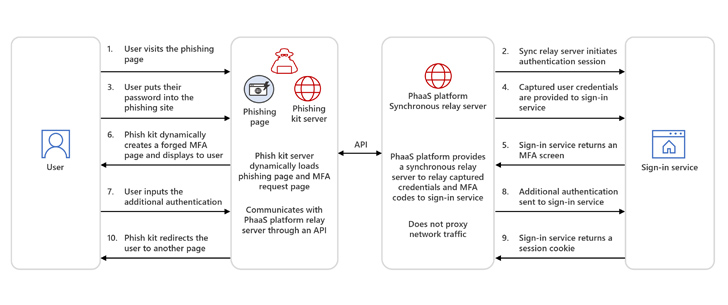
A second method involves synchronous relay servers.
“In AiTM through synchronous relay servers the target is presented with a copy or mimic of a sign-in page, like traditional phishing attacks,” Microsoft said. “Storm-1295, the actor group behind the Greatness PhaaS platform, offers synchronous relay services to other attackers.”
Greatness was first documented by Cisco Talos in May 2023 as a service that lets cybercriminals target business users of the Microsoft 365 cloud service using convincing decoy and login pages. It’s said to have been active since at least mid-2022.

The ultimate goal of such attacks is to siphon session cookies, enabling threat actors to access privileged systems without reauthentication.
“Circumventing MFA is the objective that motivated attackers to develop AiTM session cookie theft techniques,” the tech giant noted. “Unlike traditional phishing attacks, incident response procedures for AiTM require revocation of stolen session cookies.”