Products You May Like
A nation-state activity group originating from China has been linked to cyber attacks on dozens of organizations in Taiwan as part of a suspected espionage campaign.
The Microsoft Threat Intelligence team is tracking the activity under the name Flax Typhoon, which is also known as Ethereal Panda.
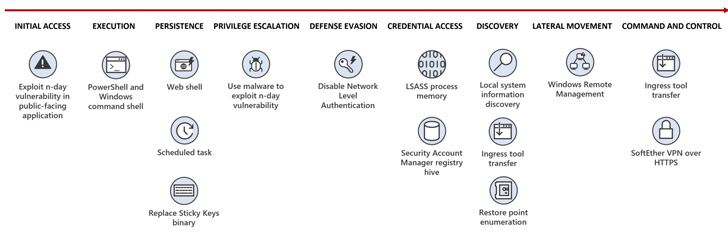
“Flax Typhoon gains and maintains long-term access to Taiwanese organizations’ networks with minimal use of malware, relying on tools built into the operating system, along with some normally benign software to quietly remain in these networks,” the company said.
It further said it hasn’t observed the group weaponize the access to conduct data-collection and exfiltration. A majority of the targets include government agencies, educational institutions, critical manufacturing, and information technology organizations in Taiwan.
A smaller number of victims have also been detected in Southeast Asia, North America, and Africa. The group is suspected to have been active since mid-2021.

“Ethereal Panda operations primarily focus on entities in the academic, technology, and telecommunications sectors in Taiwan,” CrowdStrike notes in its description of the hacker crew. “Ethereal Panda relies heavily on SoftEther VPN executables to maintain access to victim networks, but has also been observed deploying the GodZilla web shell.”
The primary focus of the actor revolves around persistence, lateral movement, and credential access, with the actor employing living-off-the-land (LotL) methods and hands-on keyboard activity to realize its goals.
The modus operandi is in line with threat actors’ practice of continually updating their approaches to evade detection, banking on available tools in the target environment to avoid unnecessary download and creation of custom components.
Initial access is facilitated by means of exploiting known vulnerabilities in public-facing servers and deploying web shells like China Chopper, followed by establishing persistent access over Remote Desktop Protocol (RDP), deploy a VPN bridge to connect to a remote server, and harvest credentials using Mimikatz.

A noteworthy aspect of the attacks is the modification of the Sticky Keys behavior to launch Task Manager, enabling Flax Typhoon to conduct post-exploitation on the compromised system.
“In cases where Flax Typhoon needs to move laterally to access other systems on the compromised network, the actor uses LOLBins, including Windows Remote Management (WinRM) and WMIC,” the Windows maker said.
 |
| Source: CrowdStrike |
CrowdStrike, which highlighted in February 2023 a case study involving an Ethereal Panda intrusion, said the actor likely abused an Apache Tomcat instance to breach an unnamed organization in order to enumerate various resources within the host and dump credentials using both ProcDump and Mimikatz.
The development comes three months after Microsoft exposed another China-linked actor named Volt Typhoon (aka Bronze Silhouette or Vanguard Panda), which has been observed exclusively relying on LotL techniques to fly under the radar and exfiltrate data.
While crossover of tactics and infrastructure among threat actors operating out of China isn’t unusual, the findings paint the picture of a constantly evolving threat landscape, with adversaries shifting their tradecraft to become more selective in their follow-on operations.
(The story was updated after publication to include additional information shared by CrowdStrike.)