Products You May Like
The North Korean threat actor known as ScarCruft has been observed using an information-stealing malware with previous undocumented wiretapping features as well as a backdoor developed using Golang that exploits the Ably real-time messaging service.
“The threat actor sent their commands through the Golang backdoor that is using the Ably service,” the AhnLab Security Emergency response Center (ASEC) said in a technical report. “The API key value required for command communication was saved in a GitHub repository.”
ScarCruft is a state-sponsored outfit with links to North Korea’s Ministry of State Security (MSS). It’s known to be active since at least 2012.
Attack chains mounted by the group entail the use of spear-phishing lures to deliver RokRAT, although it has leveraged a wide range of other custom tools to harvest sensitive information.
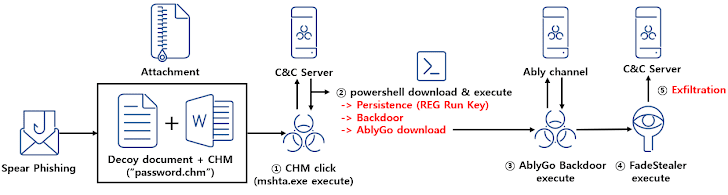
In the latest intrusion detected by ASEC, the email comes bearing a Microsoft Compiled HTML Help (.CHM) file — a tactic first reported in March 2023 — that, when clicked, contacts a remote server to download a PowerShell malware known as Chinotto.
Chinotto, in addition to being responsible for setting up persistence, retrieving additional payloads, including a backdoor codenamed AblyGo (aka SidLevel by Kaspersky) that abuses the Ably for command-and-control.
It doesn’t end there, for AblyGo is used as a conduit to ultimately execute an information stealer malware dubbed FadeStealer that comes with various features to take screenshots, gather data from removable media and smartphones, log keystrokes, and record microphone.
“The RedEyes group carries out attacks against specific individuals such as North Korean defectors, human rights activists, and university professors,” ASEC said. “Their primary focus is on information theft.”
“Unauthorized eavesdropping on individuals in South Korea is considered a violation of privacy and is strictly regulated under relevant laws. Despite this, the threat actor monitored everything victims did on their PC and even conducted wiretapping.”
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
CHM files have also been employed by other North Korea-affiliated groups such as Kimsuky, what with SentinelOne disclosing a recent campaign leveraging the file format to deliver a reconnaissance tool called RandomQuery.
In a new set of attacks spotted by ASEC, the CHM files are configured to drop a BAT file, which is then used to download next-stage malware and exfiltrate user information from the compromised host.
Spear-phishing, which has been Kimsuky’s preferred initial access technique for over a decade, is typically preceded by broad research and meticulous preparation, according to an advisory from U.S. and South Korean intelligence agencies.
The findings also follow the Lazarus Group‘s active exploitation of security flaws in software such as INISAFE CrossWeb EX, MagicLine4NX, TCO!Stream, and VestCert that are widely used in South Korea to breach companies and deploy malware.