Products You May Like
The China-linked nation-state hacking group referred to as Mustang Panda is using lures related to the ongoing Russo-Ukrainian War to attack entities in Europe and the Asia Pacific.
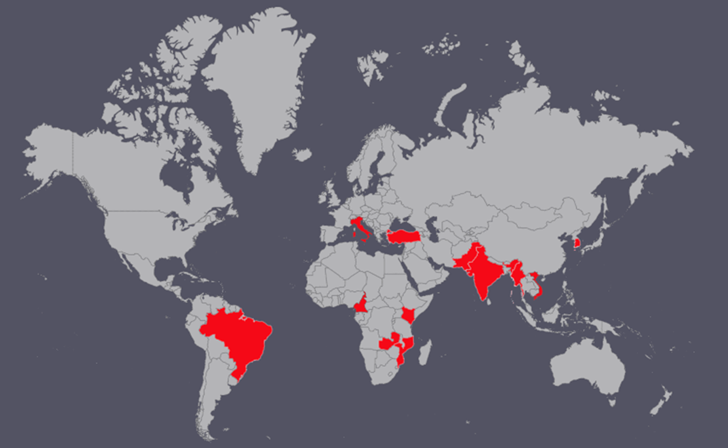
That’s according to the BlackBerry Research and Intelligence Team, which analyzed a RAR archive file titled “Political Guidance for the new EU approach towards Russia.rar.” Some of the targeted countries include Vietnam, India, Pakistan, Kenya, Turkey, Italy, and Brazil.
Mustang Panda is a prolific cyber-espionage group from China that’s also tracked under the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.
It’s believed to be active since at least July 2018, per Secureworks’ threat profile, although indications are that the threat actor has been targeting entities worldwide as early as 2012.
Mustang Panda is known to heavily rely on sending weaponized attachments via phishing emails to achieve initial infection, with the intrusions eventually leading to the deployment of the PlugX remote access trojan.
However, recent spear-phishing attacks undertaken by the group targeting government, education, and research sectors in the Asia Pacific region have involved custom malware like PUBLOAD, TONEINS, and TONESHELL, suggesting an expansion to its malware arsenal.
The latest findings from BlackBerry show that the core infection process has remained more or less the same, even as Mustang Panda continues to utilize geopolitical events to their advantage, echoing prior reports from Google and Proofpoint.
Contained within the decoy archive is a shortcut to a Microsoft Word file, which leverages DLL side-loading – a technique that was also employed in attacks aimed at Myanmar earlier this year – to kick off the execution of PlugX in memory, before displaying the document’s contents.
“Their attack chain remains consistent with the continued use of archive files, shortcut files, malicious loaders, and the use of the PlugX malware, although their delivery setup is usually customized per region/country to lure victims into executing their payloads in the hope of establishing persistence with the intent of espionage,” BlackBerry’s Dmitry Bestuzhev told The Hacker News.