Products You May Like
Multiple campaigns that distributed trojanized and typosquatted packages on the NPM open source repository have been identified as the work of a single threat actor dubbed LofyGang.
Checkmarx said it discovered 199 rogue packages totaling thousands of installations, with the group operating for over a year with the goal of stealing credit card data as well as user accounts associated with Discord Nitro, gaming, and streaming services.
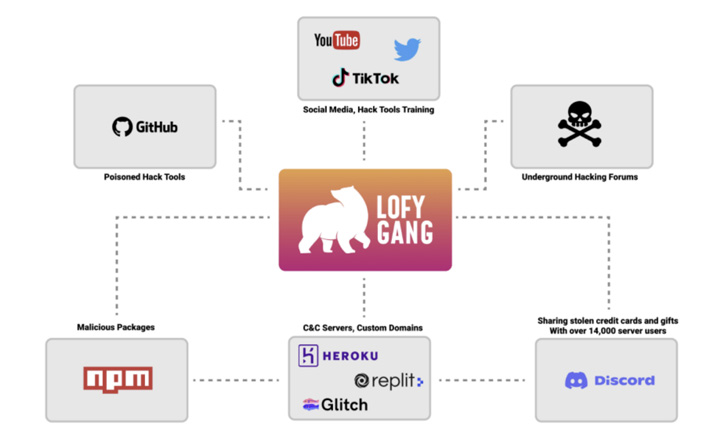
“LofyGang operators are seen promoting their hacking tools in hacking forums, while some of the tools are shipped with a hidden backdoor,” the software security company said in a report shared with The Hacker News prior to its publication.
Various pieces of the attack puzzle have already been reported by JFrog, Sonatype, and Kaspersky (which called it LofyLife), but the latest analysis pulls the various operations together under one organizational umbrella that Checkmarx is referring to as LofyGang.
Believed to be an organized crime group of Brazilian origin, the attackers have a track record of using sock puppet accounts to advertise their tools and services on GitHub, YouTube, and leaking thousands of Disney+ and Minecraft accounts on underground hacking forums.
It’s also known to employ a Discord server created nearly a year ago on October 31, 2021, to provide technical support and communicate with their members. One of its main offerings is a service that sells fake Instagram followers.
“Discord, Repl.it, glitch, GitHub, and Heroku are just a few services LofyGang is using as [command-and-control] servers for their operation,” the researchers noted.
What’s more, the fraudulent packages traced back to the group have been found to embed password stealers and Discord-specific malware, some of which are designed to steal credit cards.
To conceal the scale of the supply chain attack, the packages are intentionally published through different user accounts so that other weaponized libraries remain unaffected on the repositories even if one of them is spotted and removed by the maintainers.
Furthermore, the adversary has been found using a sneaky technique wherein the top-level package is kept free of malware but have it depend on another package that introduces the malicious capabilities.
That’s not all. Even the hacking tools shared by LofyGang on GitHub depend on malicious packages, effectively acting as a conduit to deploy persistent backdoors on the operator’s machines.
The findings are yet another indication that malicious actors are increasingly setting their sights on the open source ecosystem as a stepping point to widen the scope and effectiveness of their attacks aimed at downstream customers.
“Communities are being formed around utilizing open-source software for malicious purposes,” the researchers concluded. “We believe this is the start of a trend that will increase in the coming months.”