Products You May Like
Security researchers have disclosed a security vulnerability in the VirusTotal platform that could have been potentially weaponized to achieve remote code execution (RCE).
The flaw, now patched, made it possible to “execute commands remotely within VirusTotal platform and gain access to its various scans capabilities,” Cysource researchers Shai Alfasi and Marlon Fabiano da Silva said in a report exclusively shared with The Hacker News.
VirusTotal, part of Google’s Chronicle security subsidiary, is a malware-scanning service that analyzes suspicious files and URLs and checks for viruses using more than 70 third-party antivirus products.
The attack method involved the upload of a DjVu file through the platform’s web user interface, using it to trigger an exploit for a high-severity remote code execution flaw in ExifTool, an open-source utility used to read and edit EXIF metadata information in image and PDF files.
Tracked as CVE-2021-22204 (CVSS score: 7.8), the high-severity vulnerability in question is a case of arbitrary code execution that arises from ExifTool’s mishandling of DjVu files. The issue was patched by its maintainers in a security update released on April 13, 2021.
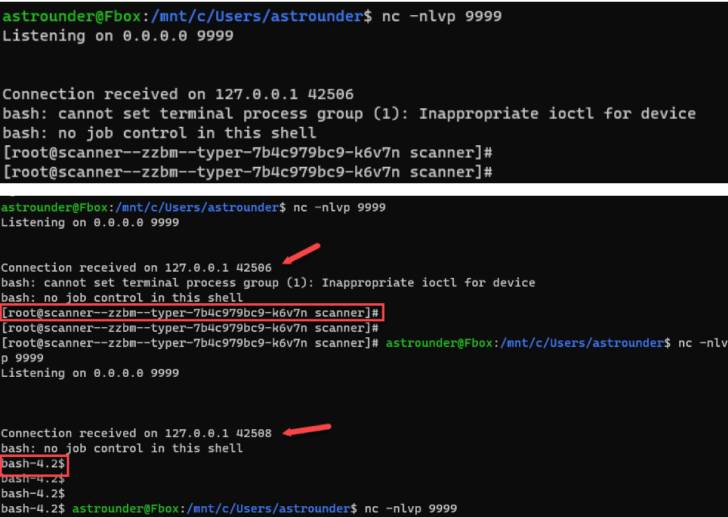
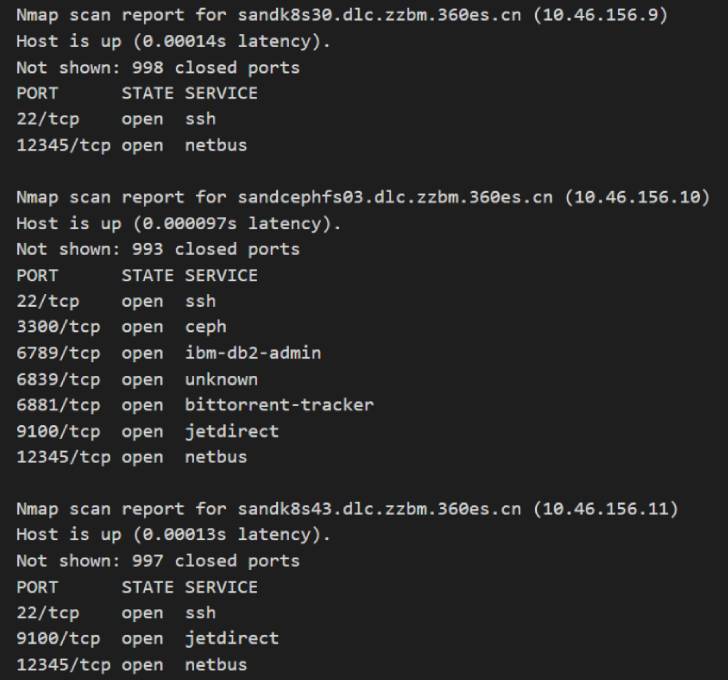
A consequence of such an exploitation, the researchers noted, was that it granted access to not only a Google-controlled environment, but also to more than 50 internal hosts with high-level privileges.
“The interesting part is every time we uploaded a file with a new hash containing a new payload, VirusTotal forwarded the payload to other hosts,” the researchers said. “So, not just we had an RCE, but also it was forwarded by Google’s servers to Google’s internal network, its customers, and partners.”
Cysource said it responsibly reported the bug through Google Vulnerability Reward Programs (VRP) on April 30, 2021, following which the security weakness was immediately rectified.
This is not the first time the ExifTool flaw emerged as a conduit to achieve remote code execution. Last year, GitLab fixed a critical flaw (CVE-2021-22205, CVSS score: 10.0) related to an improper validation of user-provided images, leading to arbitrary code execution.