Products You May Like
A group of academics from the University of Oxford and Armasuisse S+T has disclosed details of a new attack technique against the popular Combined Charging System (CCS) that could potentially disrupt the ability to charge electric vehicles at scale.
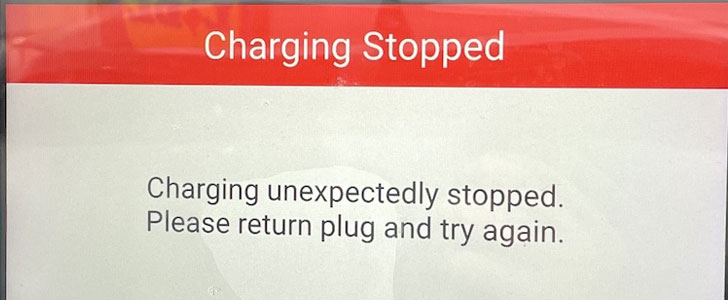
Dubbed “Brokenwire,” the method interferes with the control communications that transpire between the vehicle and charger to wirelessly abort the charging sessions from a distance of as far as 47m (151ft).
“While it may only be an inconvenience for individuals, interrupting the charging process of critical vehicles, such as electric ambulances, can have life-threatening consequences,” the researchers explained.
“Brokenwire has immediate implications for many of the 12 million battery EVs estimated to be on the roads worldwide — and profound effects on the new wave of electrification for vehicle fleets, both for private enterprise and for crucial public services.”
Additional details of the attack’s modus operandi have been kept under wraps so as to prevent active exploitation in the wild while concerned stakeholders work towards arriving at appropriate countermeasures.
Combined Charging System refers to a type of connector used for rapid-charging electric vehicles. Brokenwire takes aim at this technology by transmitting a malicious electromagnetic signal, causing the charging process to be unexpectedly stopped.
The researchers pointed out that the attack can be mounted with an assorted mix of off-the-shelf radio components such as software-defined radio, power amplifiers, and a dipole antenna, not to mention be executed in person from a nearby location or by deploying a device at a target site and control it remotely.
“The use of PLC [power-line communications] for charging communication is a serious design flaw that leaves millions of vehicles, some of which belong to critical infrastructure, vulnerable,” the researchers said.