Products You May Like
Misconfigurations in smart contracts are being exploited by scammers to create malicious cryptocurrency tokens with the goal of stealing funds from unsuspecting users.
The instances of token fraud in the wild include hiding 99% fee functions and concealing backdoor routines, researchers from Check Point said in a report shared with The Hacker News.
Smart contracts are programs stored on the blockchain that are automatically executed when predetermined conditions are met according to the terms of a contract or an agreement. They allow trusted transactions and agreements to be carried out between anonymous parties without the need for a central authority.
By examining the Solidity source code used for implementing smart contracts, the Israeli cybersecurity company found instances of hidden and hardcoded fees that can’t be changed, while allowing malicious actors to exert control over “who is allowed to sell.”
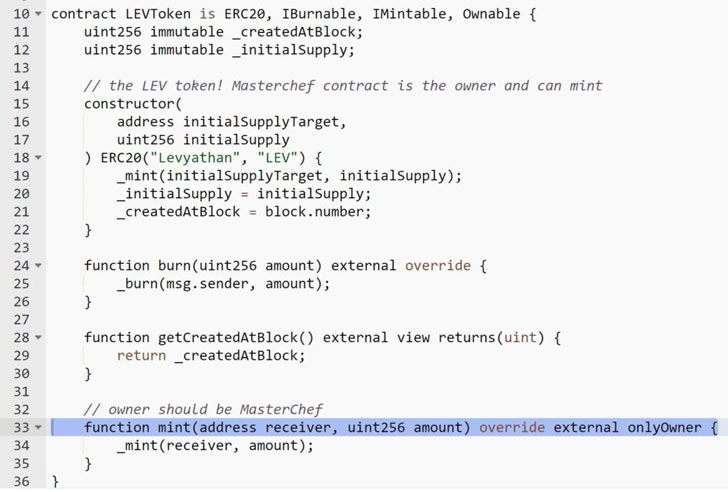
In another instance, a legitimate contract called Levyathan was hacked after its developers inadvertently uploaded the wallet’s private key to their GitHub repository, enabling the exploiter to mint an infinite number of tokens and steal funds from the contract in July 2021.
A rug pull is a type of scam that happens when the creators cash out out the investors’ money and abandon the project after a huge amount is allocated to what appears to be a legitimate crypto project.
Lastly, poor access controls put in place by the maintainers of the Zenon Network allowed an attacker to abuse the unprotected burn function within the smart contract to ramp up the price of the coin and drain funds to the tune of $814,570 in November 2021.
The findings come as cyberattack campaigns have been observed leveraging phishing schemes built on lures surrounding soon-to-be-released (albeit fake) crypto tokens to ultimately trick victims into paying for it with their own cryptocurrency.
“On top of that, to engage other victims and perpetuate the scam, the website offered a referral program for friends and family,” Akamai researcher Or Katz said. “In doing this, the threat actors created a new trustworthy channel through which current victims referred [to] other potential targets.”
“The implication is that crypto users will continue to fall into these traps, and will lose their money,” Oded Vanunu, head of products vulnerabilities research at Check Point, said. “To avoid scam coins, I recommend crypto users to diversify their wallets, ignore ads, and test their transactions.”