Products You May Like
When I want to know the most recently published best practices in cyber security, I visit The National Institute of Standards and Technology (NIST). From the latest password requirements (NIST 800-63) to IoT security for manufacturers (NISTIR 8259), NIST is always the starting point. NIST plays a key role as a US standard-setter, due to the organization’s professionalism and the external experts who help to create NIST documents.
The NIST Cybersecurity Framework (CSF) was initially released in 2014 and last updated in 2018. The framework enables organizations to improve the security and resilience of critical infrastructure with a well-planned and easy-to-use framework.
The continuing growth in SaaS, and the major changes to the work environment due to COVID-19 bring new security challenges. Although the CSF was written and updated while SaaS was on the rise, it is still geared towards the classic legacy critical infrastructure security challenges. However, organizations can better respond to new risks by adapting the CSF to modern, SaaS-based work environments.
I personally love this Framework, but truth be told, when one reads the Framework in-depth, its complexity is apparent, and following it can be difficult. This article will review the CSF’s key elements, point out its key merits, and suggest implementations for SaaS security.
Learn how to automate your organization’s NIST compliance
Overview of NIST CSF
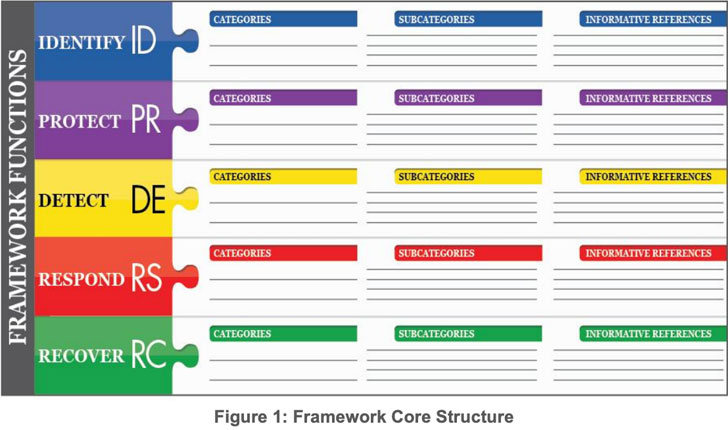
The NIST CSF lays out five functions of security, then splits them into categories and subcategories. The subcategories contain the actual controls. For each subcategory, the CSF includes a list of cross-references to well-known standards and frameworks such as ISO 27001, COBIT, NIST SP 800-53, and ANSI/ISA-62443.
These cross-references help organizations implement the CSF and map it to other frameworks. For example, security managers or other team members can use the references to justify their decisions no matter what security standard the company needs to comply with.
In a single document, the Framework combines a host of approaches to dealing with cyber security threats. This includes:
- setting up procedures
- training
- defining roles
- auditing
- monitoring
The framework has a five-stage core structure: Identify, Protect, Detect, Respond and Recover. I’m going to break them down into bullets for you.
Identify
NIST defines this function as follows:
“Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.”
Within this function, NIST includes the following control categories:
- Asset Management
- Business Environment
- Governance
- Risk Assessment
- Risk Management Strategy
- Supply Chain Risk Management.
Protect
NIST defines this function as follows:
“Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.”
Within this function, NIST includes the following control categories:
- Access Control
- Awareness and Training
- Data Security
- Information Protection Processes and Procedures
- Maintenance
- Protective Technology
Detect
NIST defines this function as follows:
“Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event”.
Within this function, NIST includes the following control categories:
- Anomalies and Events
- Security Continuous Monitoring
- Detection Processes
Respond
NIST defines this function as follows:
“Develop and implement the appropriate activities to take action regarding a detected cybersecurity event”.
Within this function, NIST includes the following control categories:
- Response Planning
- Communications
- Analysis
- Mitigation
- Improvements
Recover
NIST defines this function as follows:
“Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event”.
Within this function, NIST includes the following control categories:
- Recovery Planning
- Improvements
- Communications
Applying the CSF to SaaS Security
While definitely a model in best practices, the Framework is a challenge to implement.
Data-in-transit is protected (PR.DS-2)
A company using SaaS services may wonder how this is relevant for them. They may think that compliance is the SaaS provider’s responsibility. However, a deeper look into it shows that many SaaS providers have security measures in place, and the user is responsible for using them.
For example, admins should not allow any connections via HTTP to a SaaS service. They should only allow secure HTTPS connections.
Protections against data leaks are implemented (PR.DS-5)
This may seem like a small subcategory, but underneath there is a behemoth. Data leaks are extremely difficult to prevent. SaaS application adoption makes this harder because people can share and access them from anywhere in the world.
An admin or member of the CISO office should take special care of this threat. DLP in SaaS can include security measures such as:
- sharing links to files rather than the actual file
- setting an expiration date for the link
- disabling the download option if not needed
- blocking the ability to export data in data analysis SaaS
- user authentication hardening
- prevention of locale recording in communication SaaS
- well-defined user roles with a limited number of super users and admins
Identities and credentials are issued, managed, verified, revoked, and audited for authorized devices, users and processes (PR.AC-1)
As an enterprise scales its workforce and SaaS adoption, this subcategory becomes more challenging. Managing 50,000 users over just five SaaS means that the security team needs to manage 250,000 identities. This problem is real and complicated.
Even more challenging, each SaaS has a different way to define identities, view them, and secure identities. Adding to the risk, SaaS applications don’t always integrate with each other, which means users can find themselves with different privileges across different systems. This then leads to unnecessary privileges that can create a potential security risk.
How Adaptive Shield Can Help Meet NIST CSF Requirements
The NIST CSF is an industry-standard for cybersecurity today, yet to implement it with typical manual practices and processes is an uphill battle. So why not automate?
Adaptive Shield is a SaaS Security Posture Management (SSPM) solution that can automate the compliance and configuration checks across the SaaS estate. Adaptive Shield enables security teams to easily see and fix configuration weaknesses quickly, ensuring compliance with company and industry standards, from NIST CSF, as well as other compliance mandates such as SOC 2 and the CSA Cloud Controls Matrix.