Products You May Like
Apple recently fixed a security vulnerability in the macOS operating system that could be potentially exploited by a threat actor to “trivially and reliably” bypass a “myriad of foundational macOS security mechanisms” and run arbitrary code.
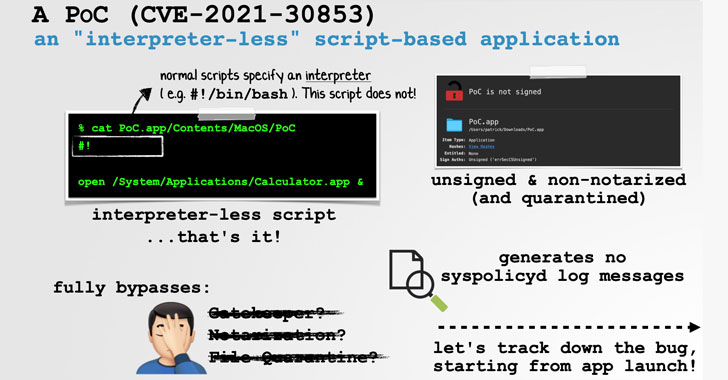
Security researcher Patrick Wardle detailed the discovery in a series of tweets on Thursday. Tracked as CVE-2021-30853 (CVSS score: 5.5), the issue relates to a scenario where a rogue macOS app may circumvent Gatekeeper checks, which ensure that only trusted apps can be run and that they have passed an automated process called “app notarization.”
The iPhone maker, crediting Gordon Long of Box with reporting the flaw, said it addressed the weakness with improved checks as part of macOS 11.6 updates officially released on September 20, 2021.
“Such bugs are often particularly impactful to everyday macOS users as they provide a means for adware and malware authors to sidestep macOS security mechanisms, …mechanisms that otherwise would thwart infection attempts,” Wardle said in a technical write-up of the flaw.
Specifically, the bug not only gets around Gatekeeper, but also File Quarantine and macOS’s notarization requirements, effectively allowing a seemingly innocuous PDF file to compromise the entire system simply by opening it. According to Wardle, the issue is rooted in the fact that an unsigned, non-notarized script-based application can not explicitly specify an interpreter, resulting in a complete bypass.
It’s worth noting that a shebang interpreter directive — e.g. #!/bin/sh or #!/bin/bash — is typically used to parse and interpret a shell program. But in this edge-case attack, an adversary can craft an application such that the shebang line is incorporated without providing an interpreter (i.e., #!) and still get the underlying operating system to launch the script without raising any alert.
This is so because “macOS will (re)attempt to execute the failed [‘interpreter-less’ script-based app] via the shell (‘/bin/sh’)” after the initial lack of success, Wardle explained.
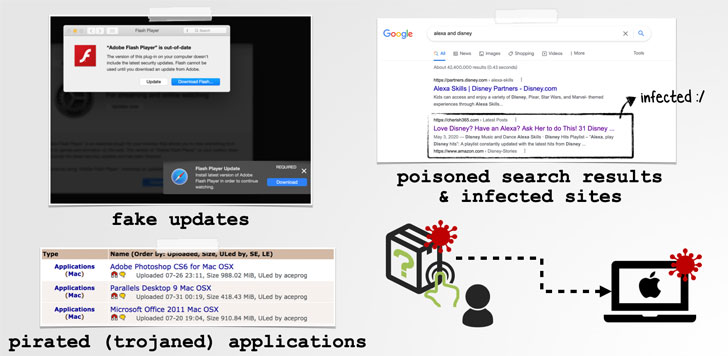
In other words, threat actors can exploit this flaw by tricking their targets into opening a rogue app that can be camouflaged as Adobe Flash Player updates or trojanized versions of legitimate apps like Microsoft Office, which, in turn, can be delivered through a method called search poisoning where attackers artificially increase the search engine ranking of websites hosting their malware to lure potential victims.
This is not the first time flaws have been discovered in the Gatekeeper process. Earlier this April, Apple moved to quickly patch a then actively exploited zero-day flaw (CVE-2021-30657) that could circumvent all security protections, thus permitting unapproved software to be run on Macs.
Then in October, Microsoft disclosed a vulnerability dubbed “Shrootless” (CVE-2021-30892), which could be leveraged to perform arbitrary operations, elevate privileges to root, and install rootkits on compromised devices. Apple said it remediated the problem with additional restrictions as part of security updates pushed on October 26, 2021.