Products You May Like
Industrial and government organizations, including enterprises in the military-industrial complex and research laboratories, are the targets of a new malware botnet dubbed PseudoManyscrypt that has infected roughly 35,000 Windows computers this year alone.
The name comes from its similarities to the Manuscrypt malware, which is part of the Lazarus APT group’s attack toolset, Kaspersky researchers said, characterizing the operation as a “mass-scale spyware attack campaign.” The Russian cybersecurity company said it first detected the series of intrusions in June 2021.
At least 7.2% of all computers attacked by the malware are part of industrial control systems (ICS) used by organizations in engineering, building automation, energy, manufacturing, construction, utilities, and water management sectors that are located mainly in India, Vietnam, and Russia. Approximately a third (29.4%) of non-ICS computers are situated in Russia (10.1%), India (10%), and Brazil (9.3%).
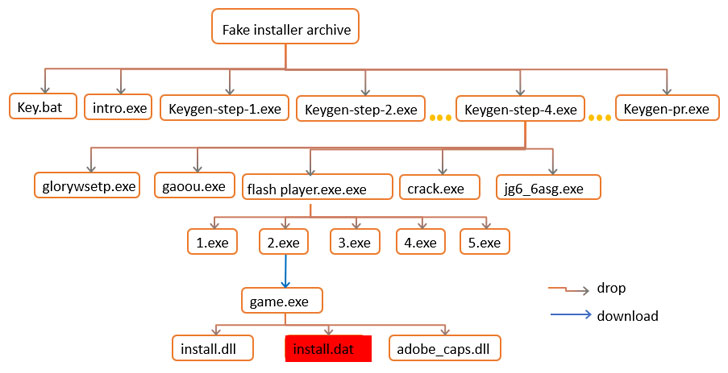
“The PseudoManuscrypt loader makes its way onto user systems via a MaaS platform that distributes malware in pirated software installer archives,” the Kaspersky ICS CERT team said. “One specific case of the PseudoManuscrypt downloader’s distribution is its installation via the Glupteba botnet.”
Coincidentally, Glupteba’s operations have also taken a significant hit when Google earlier this month disclosed that it acted to dismantle the botnet’s infrastructure and pursued litigation against two Russian nationals, who are alleged to have managed the malware along with 15 other unnamed individuals.
Among the cracked installers that are used to fuel the botnet constitute Windows 10, Microsoft Office, Adobe Acrobat, Garmin, Call of Duty, SolarWinds Engineer’s Toolset, and even Kaspersky’s own antivirus solution. The pirated software installations are driven by a method called search poisoning in which the attackers create malicious websites and use search engine optimization (SEO) tactics to make them show up prominently in search results.
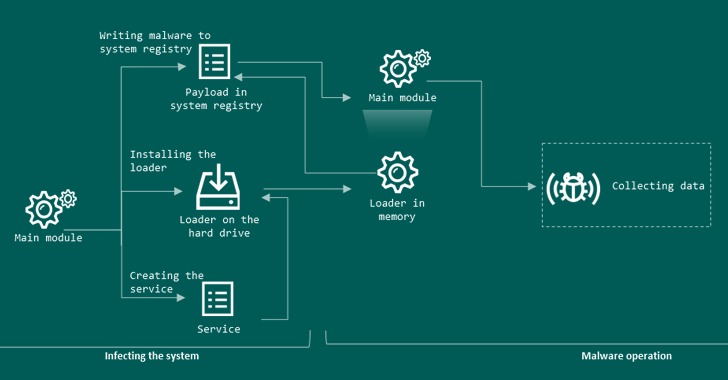
Once installed, PseudoManuscrypt comes with an array of intrusive capabilities that allows the attackers to full control of the infected system. This consists of disabling antivirus solutions, stealing VPN connection data, logging keystrokes, recording audio, capturing screenshots and videos of the screen, and intercepting data stored in the clipboard.
Kaspersky noted it has identified 100 different versions of the PseudoManuscrypt loader, with the earliest test variants dating back to March 27, 2021. Components of the trojan have been borrowed from commodity malware like Fabookie and a KCP protocol library employed by the China-based APT41 group.
The malware samples analyzed by the ICS CERT also featured comments written in Chinese and were found specifying Chinese as the preferred language, but these clues alone have been inconclusive to make an assessment about the malware’s operators or their origins. Also unclear are the ultimate goals of the campaign, raising questions as to whether the attacks are financially motivated or state-backed.
“The large number of engineering computers attacked, including systems used for 3D and physical modeling, the development and use of digital twins raises the issue of industrial espionage as one of the possible objectives of the campaign,” the researchers said.