Products You May Like
It is a time when many are thinking of their families and loved ones, time off work, and gift-giving – the holidays. However, while many have their minds outside the realm of work during the holiday season, often, this is when attackers plan their most sinister attacks.
So how can you take precautions to protect your organization during these times?
Why holidays put your company at risk of cyberattack
Attackers today do not have a soft spot for businesses and give companies a break at any time of the year, especially not during holidays. On the contrary, any time of the year where companies may be less prepared to fend off a cyberattack is an opportunity for successful compromise. As a result, the holidays put your company at a higher risk of cyberattack.
Most end-users do not think about cybersecurity when surfing the web or receiving emails with holiday deals during the season. As a result, many let their guard down to a certain degree and become preoccupied and distracted more than usual. Increased distraction from the end-user perspective and less scrutiny of emails and websites where holiday discounts and offers may be displayed can provide the perfect opportunity for attackers using phishing scams or malicious advertisements.
Additionally, IT operations and SecOps teams may be short-staffed with staff out on vacation during the holidays. It creates a situation of increased risk to business-critical data with potentially fewer resources to help mitigate risks and breaches if they happen.
Earlier this year, the FBI and Cybersecurity & Infrastructure Security Agency released a general alert for increased vigilance for ransomware attacks during holidays. You can read the warning here: Ransomware Awareness for Holidays and Weekends | CISA. In part, it states:
“The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have observed an increase in highly impactful ransomware attacks occurring on holidays and weekends—when offices are normally closed—in the United States, as recently as the Fourth of July holiday in 2021.”
With upcoming holidays in the U.S. and worldwide, organizations must remain vigilant and on guard to protect against many forms of attack. Let’s look at the following common cybersecurity risks during this holiday season:
- Ransomware
- Phishing email
- Data breach
- Distributed Denial of Service (DDoS)
- Breached passwords
1 – Ransomware
Ransomware is by far one of the most sinister threats to organizations and their data today. With the increased threat of successful phishing attacks and visits to malicious websites, the chances of your business getting infected with ransomware drastically increase.
Threat actors may entice users to click on a malicious link in a phishing email or perform a drive-by attack using malicious web code on a hijacked website. Either way, it can be a gateway for ransomware infection. Note the following ransomware attacks over a holiday:
To protect against ransomware, organizations must put the appropriate security measures in place, including:
- Phishing email filtering
- Strong password policies and breached password protection
- Least privilege access
- Micro-segmentation
- Application whitelisting
- Other security measures
Is ransomware costly to businesses? According to the IBM Cost of a Data Breach 2021 report, ransomware is highly costly to your business:
Ransomware attacks cost an average of $4.62 million, more expensive than the average data breach ($4.24 million). These costs included escalation, notification, lost business, and response costs, but did not include the cost of the ransom. Malicious attacks that destroyed data in destructive wiper-style attacks cost an average of $4.69 million. The percentage of companies where ransomware was a factor in the breach was 7.8%.
2 – Phishing email
One of the easy ways that attackers can compromise environments is by using phishing emails. Phishing emails masquerade as communications from legitimate companies. Attackers have become proficient in making phishing emails appear legitimate, from the logos, wording, images, and other styling associated with the email.
Without appropriate security protections in place, an end-user simply must click on the malicious link, and the damage begins. For example, suppose there are no zero-trust or micro-segmentation boundaries in place. In that case, the ransomware can freely crawl across the network and infect anything on which the user has “write” or “modify” permissions.
During the holiday season, end-users are generally “click-happy” and may not scrutinize emails and other communications as closely. As a result, attackers may use the flood of email communications to infiltrate the organization’s perimeter with a phishing attack.
Again, cybersecurity basics come into play to protect against phishing emails, like the protections listed for ransomware:
- Phishing email filtering
- End-user cybersecurity training
- Disallowed attachments
3 – Data breach
Data breaches are a critical cybersecurity threat for organizations worldwide. The implications and financial fall-out from a data breach event can be tremendous. The IBM Cost of a Data Breach Report 2021 cites:
Data breach costs increased significantly year-over year from the 2020 report to the 2021 report, increasing from $3.86 million in 2020 to $4.24 million in 2021. The increase of $0.38 million ($380,000) represents a 9.8% increase. This compares to a decrease of 1.5% from the 2019 to 2020 report year. The cost of a data breach has increase by 11.9% since 2015.
Data breaches can occur intentionally, unintentionally, or due to malicious cyberattacks. For example, an employee may accidentally share data they shouldn’t share or do this intentionally. In the holiday season, employees are more distracted with holiday plans or other activities and, by extension, more apt to expose data. Additionally, with the increased ransomware threat, the list of modern ransomware variants threatening data leaks is growing.
It includes:
- AKO
- AVADDON
- BABUK LOCKER
- CLOP
- CONTI
- CUBA
- DARKSIDE
- DOPPELPAYMER
- EGREGOR
- EVEREST
- LOCKBIT
- MAZE
- MESPINOZA
- MOUNT LOCKER
- NEFILIM
- NEMTY
- REVIL
4 – Distributed Denial of Service (DDoS) attacks
Another threat for businesses around the holidays is Distributed Denial of Service (DDoS) attacks. According to the statistics, the volume of Distributed Denial of Service (DDoS) attacks increases around the holidays.
In addition, since the beginning of the global pandemic in 2020, online shopping and retail have increased dramatically as more individuals prefer online shopping.
Attackers know the damage caused by DDoS attacks now is more costly to businesses, especially around the lucrative holiday season.
According to current forecasts, DDoS attacks will reach a record 11 million by the end of 2021. Knowing this, organizations must design their network mitigations and server technologies with the ability to withstand more significant DDoS attacks.
5 – Breached passwords
One of the most common ways attackers attempt to compromise environments is using compromised credentials. Obtaining compromised credentials is an easy, minimal effort attack vector that can lead to tremendous damage to business-critical data.
As mentioned, employees are more distracted and prove to be easier targets around the holidays. Phishing emails, aside from launching a ransomware attack, can be used to harvest legitimate credentials. A growing business on the dark web is Initial Access Brokers. The Initial Access Broker provides criminals with legitimate and verified user accounts for a price. It allows attackers to purchase credentials on the dark web, so the hard work of getting access to the environment is already complete.
According to the IBM Cost of a Data Breach Report 2021, compromised credentials were the most common initial attack vector, accounting for 20% of breaches. In addition, compromised credentials are among the costliest and lead to a longer data breach lifecycle than other types of data breaches as they are more challenging to detect. To combat this threat, organizations must bolster their password policies and implement adequate breached password protection.
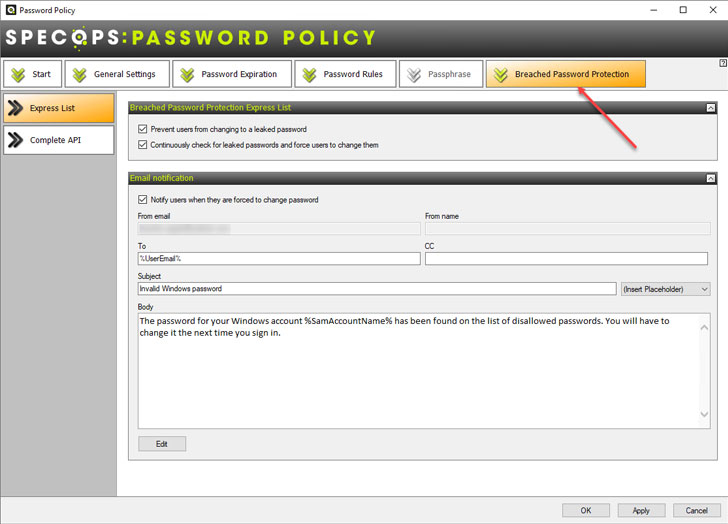
Bolster password policy and stop breached accounts
Increasing the security of Active Directory passwords and implementing breached password protection are critical to bolstering cybersecurity posture during the holidays. Unfortunately, native Active Directory password policies lack modern features to protect user accounts from weak passwords, incremental passwords, and significantly breached passwords.
Specops Password Policy helps to overcome these challenges. Note the following features.
- It protects against the use of weak Active Directory passwords
- It protects against the use of incremental passwords
- It can implement length-based aging
- It provides continuous breached password protection
- Specops monitor brute force attempts on dangerous ports, such as RDP, for the LIVE password’s attackers are using
- It helps to defend your organization against credential-based ransomware attacks by alerting businesses to passwords in use found in breached password lists
 |
| Specops Breached Password Protection |
In addition, Specops Password Policy provides the following benefits:
- Easy implementation of multiple password dictionary lists
- Over 2 billion breached passwords and growing
- LIVE breached password account data
- Find and remove breached passwords in your Active Directory environment
- Informative client messaging
- Real-time, dynamic feedback to end-users at password change
- Customize password expiration based on password length
- Block common information from use in passwords, including usernames, display names, specific words, consecutive characters, incremental passwords, and reusing a part of the current password
- Granular, GPO-driven targeting for any GPO level, computer, user, or group population
- Passphrase support
- Supports over 25 languages
- Use Regular Expressions to customize password filtering further
Learn more about the password protection provided by Specops Password Policy and start a free trial.
