Products You May Like
A malicious campaign has been found leveraging a technique called domain fronting to hide command-and-control traffic by leveraging a legitimate domain owned by the Myanmar government to route communications to an attacker-controlled server with the goal of evading detection.
The threat, which was observed in September 2021, deployed Cobalt Strike payloads as a stepping stone for launching further attacks, with the adversary using a domain associated with the Myanmar Digital News network, a state-owned digital newspaper, as a front for their Beacons.
“When the Beacon is launched, it will submit a DNS request for a legitimate high-reputation domain hosted behind Cloudflare infrastructure and modify the subsequent HTTPs requests header to instruct the CDN to direct the traffic to an attacker-controlled host,” Cisco Talos researchers Chetan Raghuprasad, Vanja Svajcer, and Asheer Malhotra said in a technical analysis published Tuesday.
Originally released in 2012 to address perceived shortcomings in the popular Metasploit penetration-testing and hacking framework, Cobalt Strike is a popular red team software that’s used by penetration testers to emulate threat actor activity in a network.
But as the utility simulates attacks by actually carrying out these attacks, the software has increasingly emerged as a formidable weapon in the hands of malware operators, who use it as an initial access payload that enables the attackers to carry out a diverse array of post-exploitation activities, including lateral movement and deploy a wide range of malware.
 |
| Cobalt Strike beacon traffic |
Although threat actors can obtain Cobalt Strike by purchasing the tool directly from the vendor’s website for $3,500 per user for a one-year license, it can also be bought on the dark web via underground hacking forums, or, alternatively, get their hands on cracked, illegitimate versions of the software.
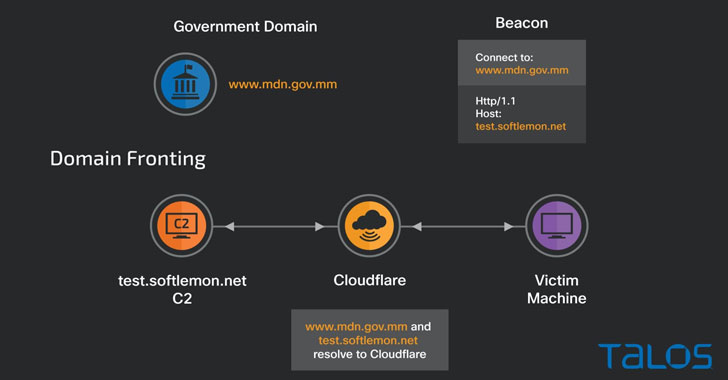
In the latest campaign observed by Talos, the execution of the Beacon results in the victim machine sending the initial DNS request to the government-owned host, while the actual command-and-control (C2) traffic is stealthily redirected to an attacker-controlled server, effectively mimicking legitimate traffic patterns in an attempt to escape detection by security solutions.
“While the default C2 domain was specified as www[.]mdn[.]gov[.]mm, the beacon’s traffic was redirected to the de-facto C2 test[.]softlemon[.]net via HTTP Get and POST metadata specified in the beacon’s configuration,” the researchers said. “The DNS request for the initial host resolves to a Cloudflare-owned IP address that allows the attacker to employ domain fronting and send the traffic to the actual C2 host test[.]softlemon[.]net, also proxied by Cloudflare.”
The C2 server, however, is no longer active, according to the researchers, who noted that it’s a Windows server running Internet Information Services (IIS).
“Domain fronting can be achieved with a redirect between the malicious server and the target. Malicious actors may misuse various content delivery networks (CDNs) to set up redirects of serving content to the content served by attacker-controlled C2 hosts,” the researchers said. “Defenders should monitor their network traffic even to high reputation domains in order to identify the potential domain fronting attacks with Cobalt Strike and other offensive tools.”