Products You May Like
A new politically-motivated hacker group named “Moses Staff” has been linked to a wave of targeted attacks targeting Israeli organizations since September 2021 with the goal of plundering and leaking sensitive information prior to encrypting their networks, with no option to regain access or negotiate a ransom.
“The group openly states that their motivation in attacking Israeli companies is to cause damage by leaking the stolen sensitive data and encrypting the victim’s networks, with no ransom demand,” Check Point Research said in a report published Monday. “In the language of the attackers, their purpose is to ‘Fight against the resistance and expose the crimes of the Zionists in the occupied territories.'”
At least 16 victims have had their data leaked to date, according to stats released by the collective.
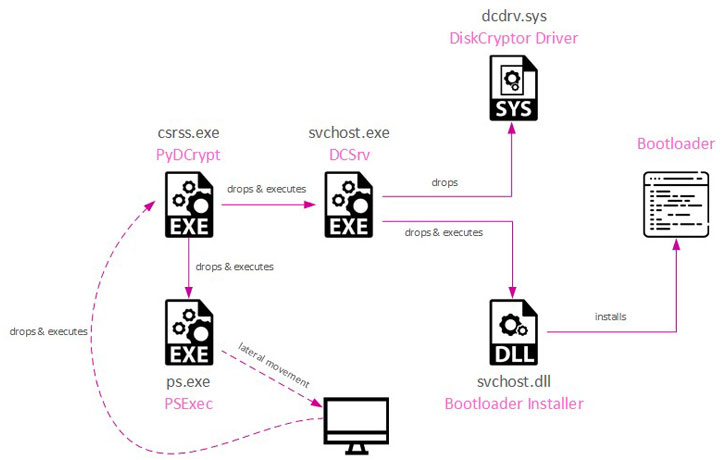
The threat actor is said to leverage publicly known vulnerabilities as a means to breach enterprise servers and gain initial access, following it up with the deployment of a custom web shell that’s used to drop additional malware. Once inside, the intruders take advantage of living-off-the-land (LotL) techniques to laterally move across the network and deploy malware to lock the machines behind encryption barriers via a specially-crafted PyDCrypt malware.
The attacks specifically rely on the open-source library DiskCryptor to perform volume encryption, in addition to infecting the systems with a bootloader that prevents them from starting without the correct encryption key. The goal, the researchers said, is to disrupt operations and inflict “irreversible damage” to the victims.
That said, the encrypted files can be recovered under certain scenarios since the group uses a symmetric key mechanism to generate the encryption keys. Check Point did not attribute the adversary to any specific country, citing lack of definitive evidence, but noted that some artifacts of the group’s toolset had been submitted to VirusTotal from Palestine months prior to the first attack.
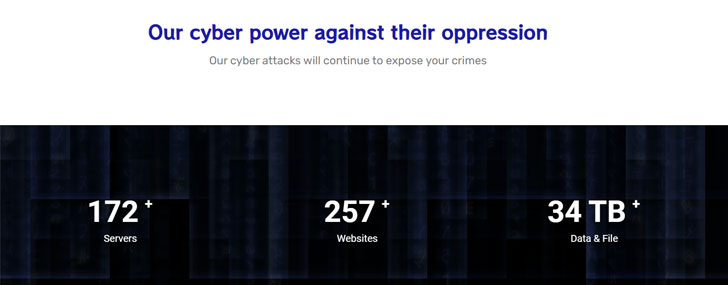
Moses Staff also operates Twitter and Telegram to publicize their attacks, with malicious activity reported as recently as November 14. The group’s own website claims it has targeted over 257 websites as well as stolen data and documents amounting to 34 terabytes. What’s more, the online portal urges outside parties to join hands with them in “exposing the crimes of the Zionists in occupied Palestine.”
“Moses Staff are still active, pushing provocative messages and videos in their social network accounts,” the researchers said. “The vulnerabilities exploited in the group’s attacks are not zero days, and therefore all potential victims can protect themselves by immediately patching all publicly-facing systems.”