Products You May Like
The U.S. Federal Bureau of Investigation (FBI) on Saturday confirmed unidentified threat actors have breached one of its email servers to blast hoax messages about a fake “sophisticated chain attack.”
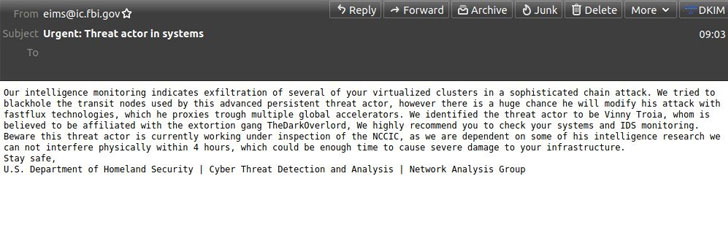
The incident, which was first publicly disclosed by threat intelligence non-profit SpamHaus, involved sending rogue warning emails with the subject line “Urgent: Threat actor in systems” originating from a legitimate FBI email address “eims@ic.fbi[.]gov” that framed the attack on Vinny Troia, a security researcher and founder of dark web intelligence firms Night Lion Security and Shadowbyte, while also claiming him to be affiliated with a hacking outfit named TheDarkOverlord.
SpamHaus cited its own telemetry data to point out that the email blasts happened over two “spam” waves, one shortly before 5:00 a.m. UTC and another one shortly after 7:00 a.m. UTC.
However, according to Kryptos Logic researcher Marcus Hutchins, the goal appears to be to discredit Troia. “Vinny Troia wrote a book revealing information about hacking group TheDarkOverlord. Shortly after, someone began erasing ElasticSearch clusters leaving behind his name. Later his Twitter was hacked, then his website. Now a hacked FBI email server is sending this,” Hutchins tweeted.
Brian Krebs of Krebs on Security, who also received an independent missive from the perpetrator, detailed in an independent report that the “spam messages were sent by abusing insecure code in an FBI online portal designed to share information with state and local law enforcement authorities.”
Pompompurin, as the hacker entity goes by online, told Krebs that the breach was carried out by taking advantage of a flaw in the FBI’s Law Enforcement Enterprise Portal (LEEP) that not only allowed any individual to apply for an account, but also leaked the one-time password that’s sent to the applicant to confirm their registration, effectively enabling them to intercept and tamper the HTTP requests with their own phony message to thousands of email addresses.
“The FBI is aware of a software misconfiguration that temporarily allowed an actor to leverage the Law Enforcement Enterprise Portal (LEEP) to send fake emails,” the agency said in a statement. “While the illegitimate email originated from an FBI operated server, that server was dedicated to pushing notifications for LEEP and was not part of the FBI’s corporate email service. No actor was able to access or compromise any data or PII on the FBI’s network.”
“Should I be flattered that the kids who hacked the FBI email servers decided to do it in my name?,” Troia later tweeted, while also hinting at Pompompurin being the mastermind of the smear campaign. Earlier in the day, those in charge of the Twitter account said: “I am not involved in any illegal activities. Please note that this account is also operated by [Vinny Troia].”