Products You May Like
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans (RATs), and ransomware payloads.
Microsoft 365 Defender Threat Intelligence Team, in a new report published Thursday, disclosed that it identified infiltrations distributing the Mekotio banking Trojan, backdoors such as AsyncRAT and NjRAT, and the infamous TrickBot malware. The multi-staged attacks — dubbed ISOMorph — were also publicly documented by Menlo Security in July 2021.
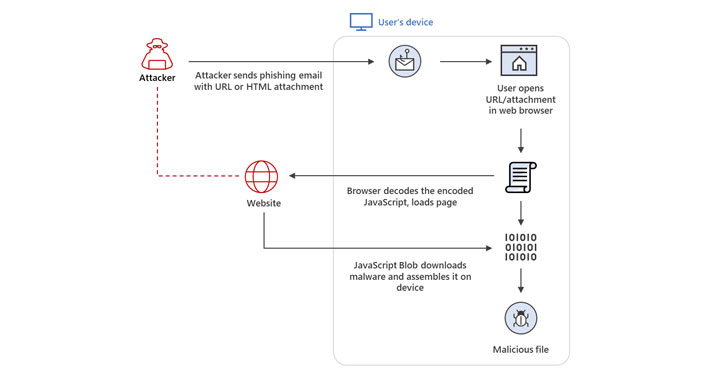
HTML smuggling is an approach that allows an attacker to “smuggle” first-stage droppers, often encoded malicious scripts embedded within specially-crafted HTML attachment or web pages, on a victim machine by taking advantage of basic features in HTML5 and JavaScript rather than exploiting a vulnerability or a design flaw in modern web browsers.
By doing so, it enables the threat actor to construct the payloads programmatically on the HTML page using JavaScript, instead of having to make an HTTP request to fetch a resource on a web server, while also simultaneously evading perimeter security solutions. The HTML droppers are then used to fetch the primary malware to be executed on the compromised endpoints.
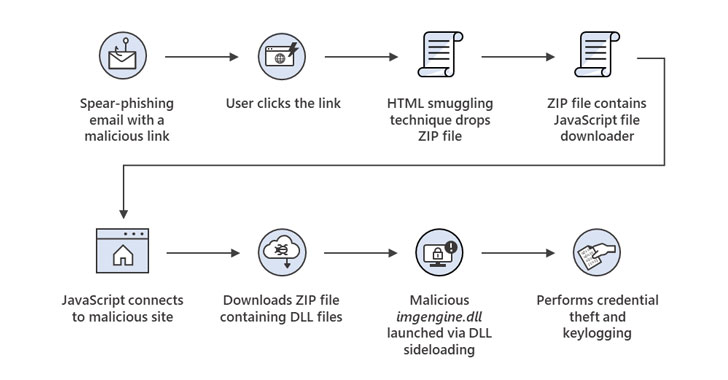 |
| Threat behavior observed in the Mekotio campaign |
“When a target user opens the HTML in their web browser, the browser decodes the malicious script, which, in turn, assembles the payload on the host device,” the researchers said. “Thus, instead of having a malicious executable pass directly through a network, the attacker builds the malware locally behind a firewall.”
HTTP Smuggling’s ability to bypass web proxies and email gateways have made it a lucrative method among state-sponsored actors and cybercriminal groups to deliver malware in real-world attacks, Microsoft noted.
Nobelium, the threat group behind the SolarWinds supply chain hack, was found leveraging this very tactic to deliver a Cobalt Strike Beacon as part of a sophisticated email-based attack aimed at government agencies, think tanks, consultants, and non-governmental organizations located across 24 countries, including the U.S., earlier this May.
Beyond espionage operations, HTML smuggling has also been embraced for banking malware attacks involving the Mekotio trojan, what with the adversaries sending spam emails containing a malicious link that, when clicked, triggers the download of a ZIP file, which, in turn, contains a JavaScript file downloader to retrieve binaries capable of credential theft and keylogging.
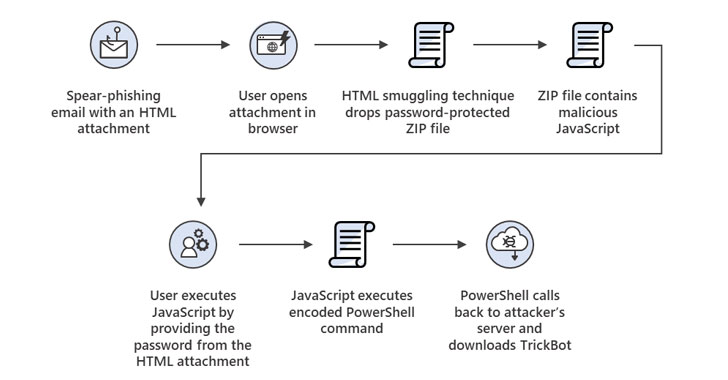 |
| HTML smuggling attack chain in the Trickbot spear-phishing campaign |
But in a sign that other actors are taking notice and incorporating HTML smuggling in their arsenal, a September email campaign undertaken by DEV-0193 was uncovered, abusing the same method to deliver TrickBot. The attacks entail a malicious HTML attachment, which, when opened on a web browser, creates a password-protected JavaScript file on the recipient’s system, prompting the victim to supply the password from the original HTML attachment.
Doing so initiates the execution of the JavaScript code, which subsequently launches a Base64-encoded PowerShell command to contact an attacker-controlled server to download the TrickBot malware, ultimately paving the way for follow-on ransomware attacks.
“The surge in the use of HTML smuggling in email campaigns is another example of how attackers keep refining specific components of their attacks by integrating highly evasive techniques,” Microsoft noted. “Such adoption shows how tactics, techniques, and procedures (TTPs) trickle down from cybercrime gangs to malicious threat actors and vice versa. It also reinforces the current state of the underground economy, where such TTPs get commoditized when deemed effective.”