Products You May Like
A previously undocumented initial access broker has been unmasked as providing entry points to three different threat actors for mounting intrusions that range from financially motivated ransomware attacks to phishing campaigns.
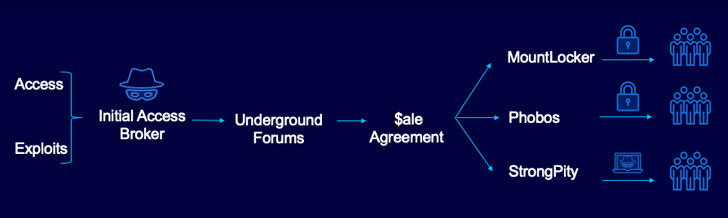
BlackBerry’s research and intelligence team dubbed the entity “Zebra2104,” with the group responsible for offering a means of a digital approach to ransomware syndicates such as MountLocker and Phobos, as well as the advanced persistent threat (APT) tracked under the moniker StrongPity (aka Promethium).
The threat landscape as we know it has been increasingly dominated by a category of players known as the initial access brokers (IABs), who are known to provide other cyber-criminal groups, including ransomware affiliates, with a foothold to an infinite pool of potential organizations belonging to diverse geographies and sectors via persistent backdoors into the victim networks, effectively building a pricing model for remote access.
“IABs typically first gain entry into a victim’s network, then sell that access to the highest bidder on underground forums located in the dark web,” BlackBerry researchers noted in a technical report published last week. “Later, the winning bidder will often deploy ransomware and/or other financially motivated malware within the victim’s organization, depending on the objectives of their campaign.”
An August 2021 analysis of more than 1,000 access listings advertised for sale by IABs in underground forums on the dark web found that the average cost of network access was $5,400 for the period July 2020 to June 2021, with the most valuable offers including domain admin privileges to enterprise systems.
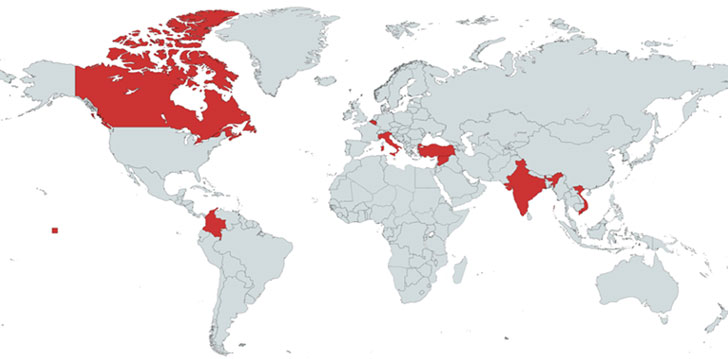
The Canadian cybersecurity company’s investigation began with a domain named “trashborting[.]com” that was found delivering Cobalt Strike Beacons, using it to link the broader infrastructure to a number of malspam campaigns that resulted in the delivery of ransomware payloads, some of which targeted Australian real estate companies and state government departments in September 2020.
On top of that, “supercombinating[.]com,” another sister domain registered alongside trashborting[.]com, was discovered connected to malicious MountLocker and Phobos activity, even as the domain resolved to an IP address “91.92.109[.]174,” which, in turn, was also used to host a third domain “mentiononecommon[.]com” between April and November 2020 and put to use as a command-and-control server in a June 2020 campaign associated with StrongPity.
The IAB’s overlaps and wide targeting has also led the researchers to believe that the operator “either has a lot of manpower or they’ve set up some large ‘hidden in plain sight’ traps across the internet,” enabling MountLocker, Phobos and StrongPity to source their access to targeted networks.
“The interlinking web of malicious infrastructure seen throughout this research has shown that, in a manner that mirrors the legitimate business world, cybercrime groups are in some cases run not unlike multinational organizations,” the researchers said. “They create partnerships and alliances to help advance their goals. If anything, it is safe to assume that these threat group ‘business partnerships’ are going to become even more prevalent in future.”