Products You May Like
The browser has become the main work interface in modern enterprises. It’s where employees create and interact with data, and how they access organizational and external SaaS and web apps. As a result, the browser is extensively targeted by adversaries. They seek to steal the data it stores and use it for malicious access to organizational SaaS apps or the hosting machine. Additionally, unintentional data leakage via the browser has become a critical concern for organizations as well.
However, traditional endpoint, network, and data protection solutions fail to protect this critical resource against advanced web-borne attacks that continuously rise in sophistication and volume. This gap leaves organizations exposed to phishing attacks, malicious browser extensions, data exposure, and data loss.
This is the challenge LayerX is attempting to solve. LayerX has developed a secure enterprise browser extension that can be mounted on any browser. The LayerX extension delivers comprehensive visibility, continuous monitoring, and granular policy enforcement on every event within the browsing session. Using proprietary Deep Session Analysis technology, LayerX can mitigate browser data loss risks, prevent credential theft by phishing sites, identify malicious extensions, and much more.
In this platform review, we’ll walk you through the entire LayerX user journey, from initial installation and configuration to visibility and protection. (to get a personalized demo of Layerx, visit their website here)
Initial Installation and Setup
LayerX is designed for easy installation on top of the organization’s existing browser infrastructure. The user can distribute it through a group policy, any enterprise device management platform, or the browser’s management workspace. For the last option, LayerX is not installed on the hosting device. Instead, it is delivered as part of the browser’s profile, making it a natural choice for the protection of unmanaged devices. The installation screen enabled the user to choose the browsers that are in use in their environment.
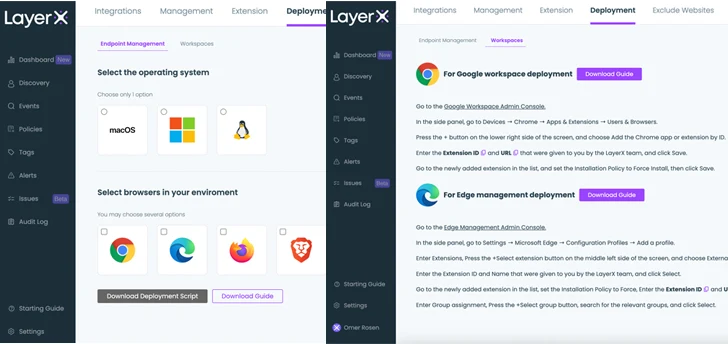 |
| Figure 1: The LayerX installation screen. Centralized distribution (left), browser management sign-in (right) |
The LayerX Dashboard
Once the installation is complete, the LayerX dashboard immediately becomes populated with pre-defined policies, information on the browsers, users, extensions, and web activity. When the user configures policies, the dashboard will show them as well, along with their status, detected risk alerts, and other data aggregations.
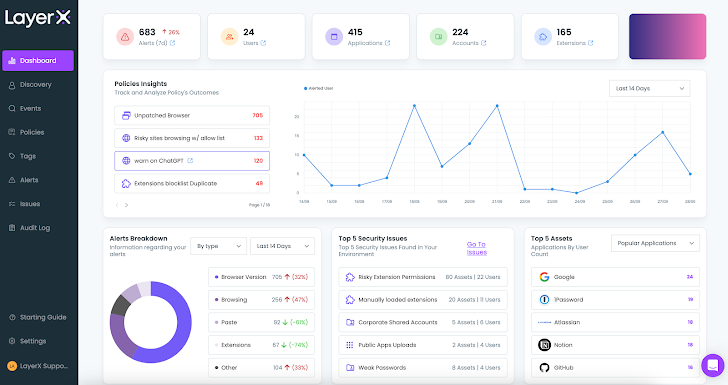 |
| Figure 2: LayerX dashboard |
The dashboard provides high-level insights into the security posture of the browser ecosystem. For drilling down into specific issues, let’s move on to the Discovery page.
Visibility and Discovery of Entities in Browsing Sessions
The Discovery page provides the user with a wealth of information about five types of entities:
- Users
- Apps
- Accounts
- Extensions
- Browsers
For example:
- The ‘Apps’ section shows users all the web and SaaS applications the organization’s employees are accessing through their browsers. This includes 100% of the apps in use, regardless of whether they are sanctioned or personal.
- The ‘Accounts’ section shows the strength of the account’s passwords or any usage of non-corporate identities. The user also can discover browsers that are running outdated versions, enforce updates, and gain visibility into all the different extensions that are installed on browsers in the ecosystem.
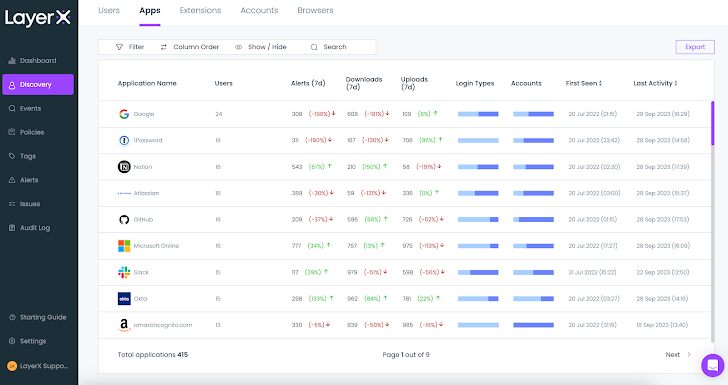 |
| Figure 3: The LayerX Discovery screen, Apps section |
Proactively Detecting and Resolving Browser Issues
The Discovery process informs the user about various issues, enabling the user to resolve them on the spot. For example, reviewing the different extensions might reveal an extension that has critical permissions that could expose it to compromise. In such a case, the extension can simply be added to a block list, eliminating the risk.
Moreover, LayerX provides a dedicated ‘Issues’ tab that aggregates all the findings that indicate a potential security weakness for each entity type. For accounts, it could be weak passwords or shared accounts. For applications, public app uploads or non-SSO corporate apps. Etc.
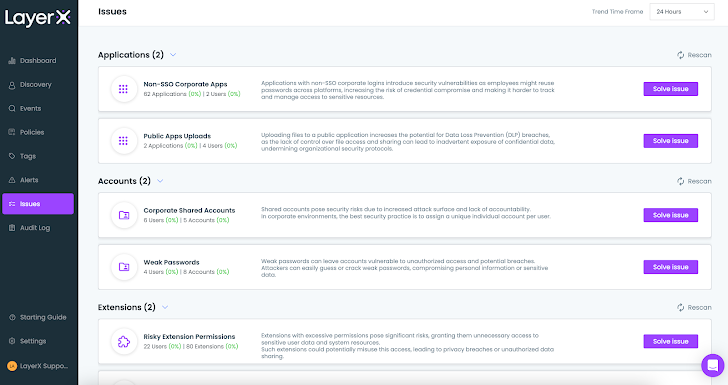 |
| Figure 4: The LayerX Issues screen displaying Account and Application issues |
It’s important to note that this is the first time that most of the data displayed in the Discovery page is available for monitoring and analysis. Existing IT and security products were not able to present it. As such, LayerX addresses a long recognized blind spot.
Detecting and Resolving Malicious Browser Extensions Risk
One of the most critical and unaddressed risks are malicious browser extensions. These extensions have the power to compromise browser data, route employees to malicious web pages, capture session data, and carry out many other malicious activities.
The ‘Extensions’ tab in the Discovery page pinpoints all the extensions that introduce a risk to the environment.
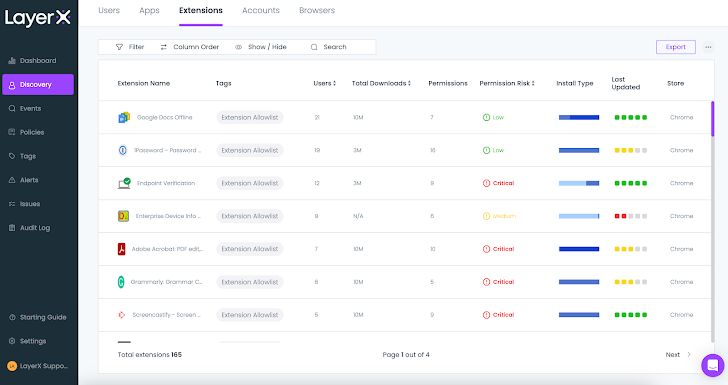 |
| Figure 5: The LayerX Discovery screen, Extensions tab |
The ‘Issues’ page aggregates the risky extensions and provides a recommendation on how to resolve it. This can be done manually or with LayerX’s ‘Automatic Resolve’ option.
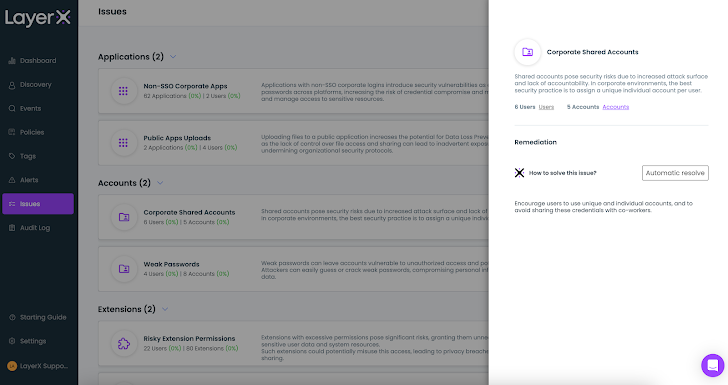 |
| Figure 6: The LayerX Issues screen displaying manual and automated resolving options |
Following the discovery and resolution of existing risky extensions, the user can proactively mitigate this risk going forward with a dedicated policy. Before showing how, let’s provide insight into LayerX’s policy configuration feature.
LayerX Policies – How to Solve Various Browser Security Use Cases
LayerX policies enable users to proactively protect against a wide range of web-borne risks. Policies are classified into different types (DLP, safe browsing, etc.) based on the risk type they address.
The heart of the policy is the ‘Conditions’ section, in which the user determines the conditions that trigger a protective action. These conditions can range from simple rules to extremely granular combinations, enabling laser focus enforcement, lower false positives and accuracy that cannot be achieved by other product
Respectively, the ‘Action’ part is also extremely granular, including both straightforward ‘block access’ or ‘prevent upload’ actions, as well as the ability to surgically disable risky components within the web page or pop-up warnings to the browsing employee.
LayerX is shipped with a set of default policies. Users can use them as is, modify their conditions and actions, or create new ones from scratch.
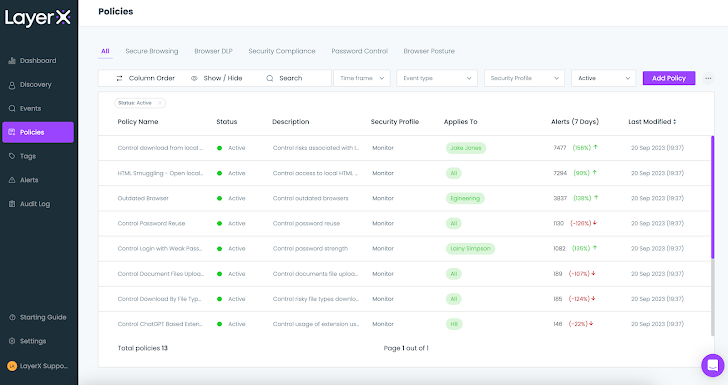 |
| Figure 7: The LayerX Policies screen |
Let’s examine a few policies to illustrate this capability.
A Policy for Preventing Risky Extension Installation
LayerX enables the user to create a list of permitted extensions. This list can then be used as a condition parameter to continuously monitor and govern this former blind spot.
LayerX provides its users with a wide range of mitigations against malicious extensions. Users can define a blockallow lists to proactively control which extensions can be installed. In addition LayerX’s granular visibility into all of the extensions’ components enables users to configure policies that can block extensions based on their requested permissions, name, install type, web store and many others. this is a unique capability that cannot be found in any endpoint protection or IT management tool.
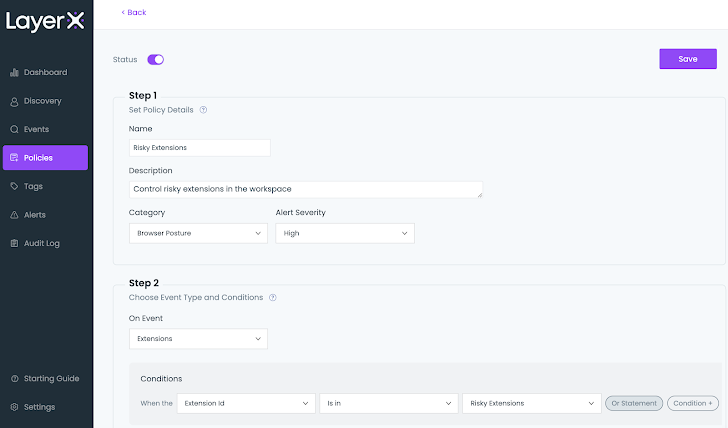 |
| Figure 8: The LayerX Policies screen, risky extension policy configuration |
Once activated, any attempt to download an extension that’s not included in the list will trigger a protective action. The employee will receive a pop-up informing them that the extension violates the organization’s policy. Based on the action configured in the policy, LayerX will either ask the employee to disable the extension or take action to automatically deactivate it.
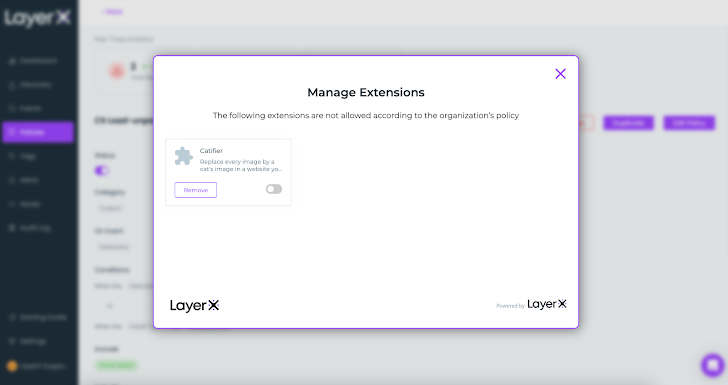 |
| Figure 9: LayerX policy action, pop up upon risky extension installation |
A Policy for Preventing Data Leakage via ChatGPT
While ChatGPT is an amazing productivity booster, it is imperative to ensure that employees use it in a secure manner and without exposing sensitive data.
The policy below shows how this risk can be mitigated. In the ‘Conditions’ section, the user defines the target site and which type of text triggers a protective action. These initial conditions can be refined by adding conditions that relate to the device state (managedunmanaged), the browser type, user identity, and more.
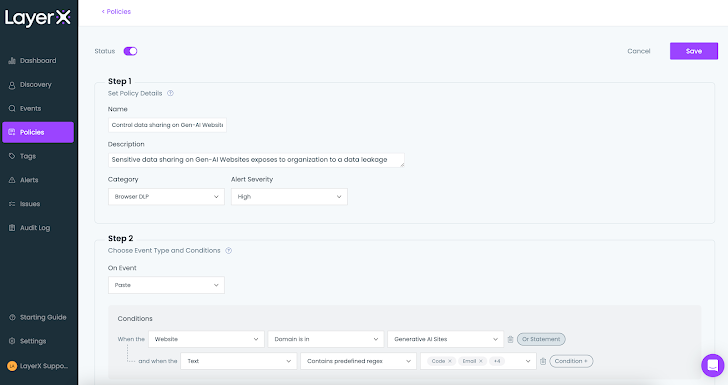 |
| Figure 10: The LayerX policy screen, setting a condition during policy configuration |
A policy can trigger various actions based on the user’s needs. The screenshot below shows the different options: monitoring, popping up an employee warning message, ‘prevent with bypass’ that enables employees to complete their ChatGPT query pending they can justify it, and the final option of full prevention.
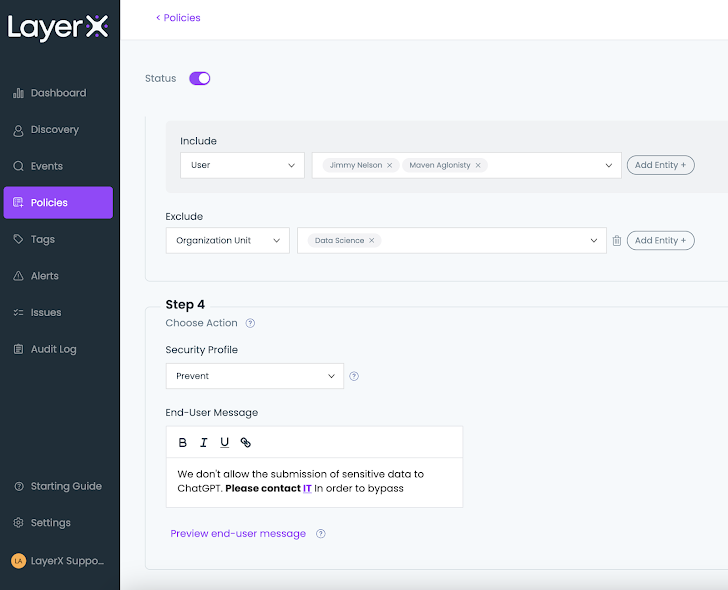 |
| Figure 11: The LayerX policy screen, setting an action during policy configuration |
Once the policy is configured and enabled, users can still use ChatGPT freely, unless sensitive data is subject to leakage risk. Any violation of the conditions defined in the policy will trigger the configured protection, as well an alert that notifies the admin of the violation and its details:
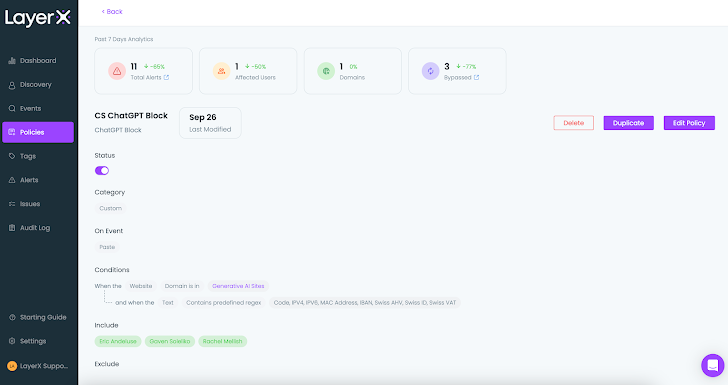 |
| Figure 12: LayerX policy screen, a single policy page |
Another critical issue LayerX policies enable resolving is Shadow Identity. This risk surfaces mainly within sanctioned apps. Suppose the user’s organization is using Google Suite, with employees accessing it with a corporate identity. However, they also have a personal Google account that introduces a data leakage risk if an employee accidentally uploads files with sensitive data to their personal drive or email rather than to the corporate one.
To solve this challenge, LayerX enables users to configure policies that are sensitive to the employee’s identity and add the identity as a condition, together with file content, labeling, and other traditional DLP attributes. Once enabled, the policy prevents uploading of corporate data to Google, unless it’s accessed by the user’s corporate account.
Hardening Protection Against Account Takeover with LayerX as an Additional authentication Factor
LayerX can be integrated with the environment’s cloud Identity Provider (IdP). In that manner, access to the SaaS apps the IDP manages is possible only from a browser on which the extension is installed. For example, when accessing a SaaS app via Okta without LayerX on the browser, an alert message is triggered:
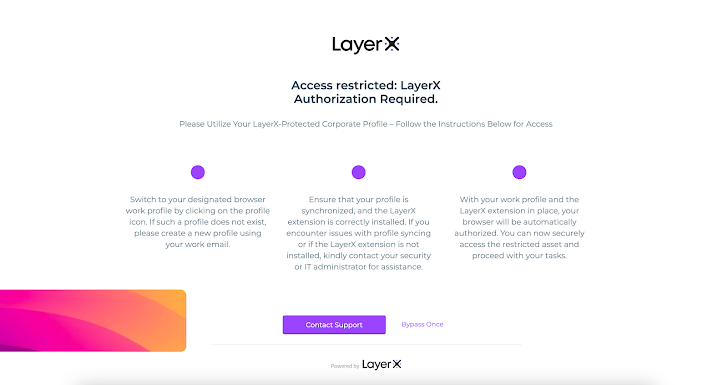 |
| Figure 13: The LayerX access restriction pop-up |
LayerX serves here as an MFA, but without the intrusive user experience of the push notification to the employee’s phone. This serves as extremely effective mitigation against malicious access that exploits compromised credentials, since adversaries will never get access to SaaS and web resources based on credentials alone.
Monitoring the Web-borne Threats Landscape from the Alerts Screen
The final LayerX screen in this overview is the Alerts screen. Every triggered policy registers an alert. The Alerts screen classifies and aggregates the alert by severity (low, medium, high, critical) and type (paste, safe browsing, etc.), and shows the top triggered policies.
The user can use the various filters to view only alerts within a certain timeframe, type, action type, or risk level.
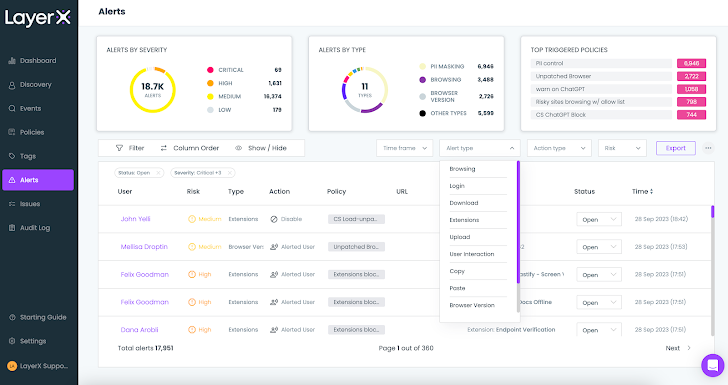 |
| Figure 14: The LayerX access Alerts screen with the Alert Type dropdown |
For example, filtering for the ‘Upload’ type will show all the policies that were triggered by employees who uploaded files in an insecure manner. Clicking on ‘Investigate’ reveals the employees’ browsing trail and the exact point within the session that violated the policy.
For example, the following event journey for a data upload policy shows that the employee uploaded a file to their personal Gmail and then switched back to their work account. Detecting and blocking such an event is a unique capability that can’t be performed by any CASB or other application-oriented security tool, since they lack the capability to differentiate between accounts for the same app.
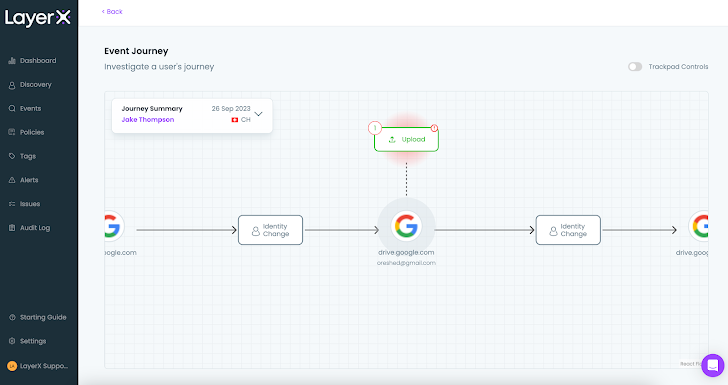 |
| Figure 15: The event journey for a triggered DLP policy |
Conclusion
The LayerX secure browser extension consolidates protection measures for the full range of web-borne risks. Some of these risks are partially addressed by existing solutions, while most were a complete blind spot, until now.
For organizations that acknowledge the centrality of the browser in their operations, LayerX is an invaluable solution, providing a single pane of glass for all the functionalities that mitigate both browser-based attacks and web-related data loss.
Visit the LayerX website here.