Products You May Like
Cybersecurity researchers have uncovered a new set of malicious packages published to the NuGet package manager using a lesser-known method for malware deployment.
Software supply chain security firm ReversingLabs described the campaign as coordinated and ongoing since August 1, 2023, while linking it to a host of rogue NuGet packages that were observed delivering a remote access trojan called SeroXen RAT.
“The threat actors behind it are tenacious in their desire to plant malware into the NuGet repository, and to continuously publish new malicious packages,” Karlo Zanki, reverse engineer at ReversingLabs, said in a report shared with The Hacker News.
The names of some of the packages are below –
- Pathoschild.Stardew.Mod.Build.Config
- KucoinExchange.Net
- Kraken.Exchange
- DiscordsRpc
- SolanaWallet
- Monero
- Modern.Winform.UI
- MinecraftPocket.Server
- IAmRoot
- ZendeskApi.Client.V2
- Betalgo.Open.AI
- Forge.Open.AI
- Pathoschild.Stardew.Mod.BuildConfig
- CData.NetSuite.Net.Framework
- CData.Salesforce.Net.Framework
- CData.Snowflake.API
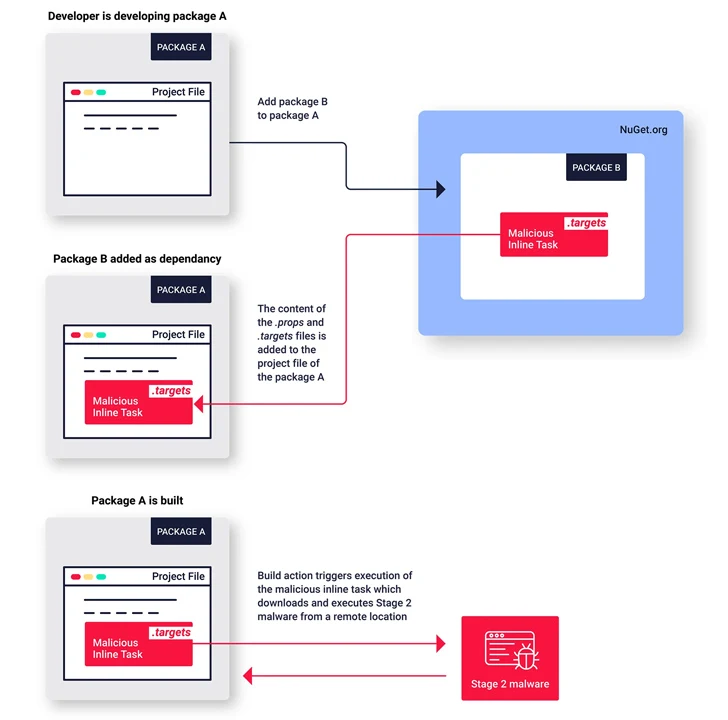
These packages, which span several versions, imitate popular packages and exploit NuGet’s MSBuild integrations feature in order to implant malicious code on their victims, a feature called inline tasks to achieve code execution.
“This is the first known example of malware published to the NuGet repository exploiting this inline tasks feature to execute malware,” Zanki said.
The now-removed packages exhibit similar characteristics in that the threat actors behind the operation attempted to conceal the malicious code by making use of spaces and tabs to move it out of view of the default screen width.
As previously disclosed by Phylum, the packages also have artificially inflated downloaded counts to make them appear more legitimate. The ultimate goal of the decoy packages is to act as a conduit for retrieving a second-stage .NET payload hosted on a throwaway GitHub repository.
“The threat actor behind this campaign is being careful and paying attention to details, and is determined to keep this malicious campaign alive and active,” Zanki said.