Products You May Like
A new information stealer malware called MetaStealer has set its sights on Apple macOS, making the latest in a growing list of stealer families focused on the operating system after Stealer, Pureland, Atomic Stealer, and Realst.
“Threat actors are proactively targeting macOS businesses by posing as fake clients in order to socially engineer victims into launching malicious payloads,” SentinelOne security researcher Phil Stokes said in a Monday analysis.
In these attacks, MetaStealer is distributed in the form of rogue application bundles in the disk image format (DMG), with targets approached through threat actors posing as prospective design clients in order to share a password-protected ZIP archive containing the DMG file.

Other instances have involved the malware masquerading as Adobe files or installers for Adobe Photoshop. Evidence gathered so far shows that MetaStealer artifacts began appearing in the wild in March 2023. The most recent sample was uploaded to VirusTotal on August 27, 2023.
“This specific targeting of business users is somewhat unusual for macOS malware, which is more commonly found being distributed via torrent sites or suspicious third-party software distributors as cracked versions of business, productivity or other popular software,” Stokes said.
The main component of the payload is an obfuscated Go-based executable that comes with features to harvest data from iCloud Keychain, saved passwords, and files from the compromised host.
Select versions of the malware have been observed containing functions that likely target Telegram and Meta services.
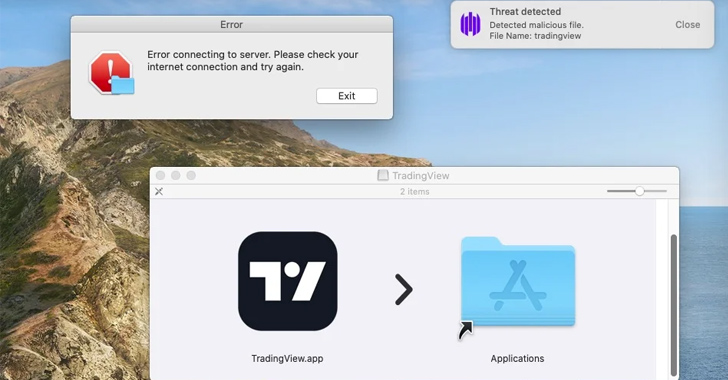
SentinelOne said it observed some MetaStealer variants impersonating TradingView, the same tactic that has been adopted by Atomic Stealer in recent weeks.
Way Too Vulnerable: Uncovering the State of the Identity Attack Surface
Achieved MFA? PAM? Service account protection? Find out how well-equipped your organization truly is against identity threats
This raises two possibilities: Either the same malware authors could be behind both the stealer families and have been adopted by different threat actors due to differences in the delivery mechanism, or they are the handiwork of disparate sets of actors.
“The appearance of yet another macOS infostealer this year shows the trend towards targeting Mac users for their data continues to rise in popularity among threat actors,” Stokes said.
“What makes MetaStealer notable among this crop of recent malware is the clear targeting of business users and the objective of exfiltrating valuable keychain and other information from these targets. Such high-value data can be used to pursue further cybercriminal activity or gain a foothold in a larger business network.”