Products You May Like
Discover all the ways MITRE ATT&CK can help you defend your organization. Build your security strategy and policies by making the most of this important framework.
What is the MITRE ATT&CK Framework?
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a widely adopted framework and knowledge base that outlines and categorizes the tactics, techniques, and procedures (TTPs) used in cyberattacks. Created by the nonprofit organization MITRE, this framework provides security professionals with insights and context that can help them comprehend, identify, and mitigate cyber threats effectively.
The techniques and tactics in the framework are organized in a dynamic matrix. This makes navigation easy and also provides a holistic view of the entire spectrum of adversary behaviors. As a result, the framework is more actionable and usable than if it were a static list.
The MITRE ATT&CK Framework can be found here: https://attack.mitre.org/
Look Out: MITRE ATT&CK Framework Biases
According to Etay Maor, Senior Director of Security Strategy at Cato Networks, “The knowledge provided in the MITRE ATT&CK framework is derived from real-world evidence of attackers’ behaviors. This makes it susceptible to certain biases that security professionals should be aware of. It’s important to understand these limitations.”
- Novelty Bias – Techniques or actors that are new or interesting are reported, while techniques that are being used over and over are not.
- Visibility Bias – Intel report publishers have visibility biases that are based on how they gather data, resulting in visibility for some techniques and not others. Additionally, techniques are also viewed differently during incidents and afterward.
- Producer Bias – Reports published by some organizations may not reflect the broader industry or world as a whole.
- Victim Bias – Some victim organizations are more likely to report, or to be reported on, than others.
- Availability Bias – Report authors often include techniques that quickly come to mind in their reports.
MITRE ATT&CK Defender Use Cases
The MITRE ATT&CK framework helps security professionals research and analyze various attacks and procedures. This can help with threat intelligence, detection and analytics, simulations, and assessment and engineering. The MITRE ATT&CK Navigator is a tool that can help explore and visualize the matrix, enhancing the analysis for defensive coverage, security planning, technique frequency, and more.
Etay Maor adds, “The framework can go as deep as you want it to be or it can be as high level as you want it to be. It can be used as a tool to show the mapping and if we’re good or bad at certain areas, but it could go as deep as understanding the very specific procedure and even the line of code that was used in a specific attack.”
Here are a few examples of how the framework and the Navigator can be used:
Threat Actor Analysis
Security professionals can leverage MITRE ATT&CK to investigate specific threat actors. For example, they can drill down into the matrix and learn which techniques are used by different actors, how they are executed, which tools they use, etc. This information helps investigate certain attacks. It also expands the researchers’ knowledge and way of thinking by introducing them to additional modes of operation attackers take.
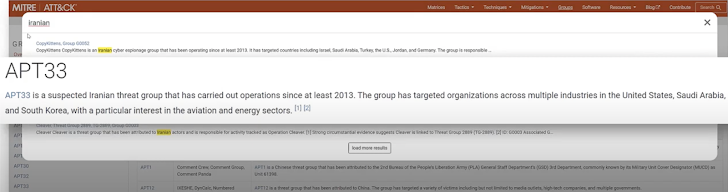
At a higher level, the framework can be used to answer C-level questions about breaches or threat actors. For example, if asked- “We think we might be a target for Iranian nation state threat actors.” The framework enables drilling down into Iranian threat actors like APT33, showing which techniques they use, attack IDs, and more.
Multiple Threat Actor Analysis
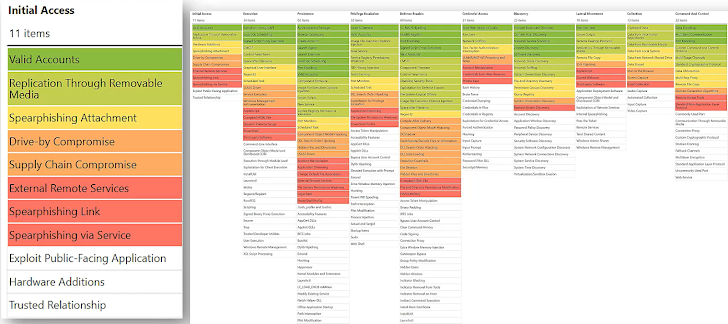
Apart from researching specific actors, the MITRE ATT&CK framework also allows analyzing multiple threat actors. For example, if a concern is raised that “Due to recent political and military events in Iran we believe there will be a retaliation in the form of a cyber attack. What are the common attack tactics of Iranian threat actors?”, the framework can be used to identify common tactics used by a number of nation-state actors.
Here’s what a visualized multiple threat actor analysis could look like, with red and yellow representing techniques used by different actors and green representing an overlap.
Gap Analysis
The MITRE ATT&CK framework also helps analyze existing gaps in defenses. This enables defenders to identify, visualize and sort which ones the organization does not have coverage for.
Here’s what it could look like, with colors used for prioritization.
Atomic Testing
Finally, the Atomic Red Team is an open source library of tests mapped to the MITRE ATT&CK framework. These tests can be used for testing your infrastructure and systems based on the framework, to help identify and mitigate coverage gaps.
The MITRE CTID (Center for Threat-Informed Defense)
The MITRE CTID (Center for Threat-Informed Defense) is an R&D center, funded by private entities, that collaborates with both private sector organizations and nonprofits. Their objective is to revolutionize the approach to adversaries through resource pooling and emphasizing proactive incident response rather than reactive measures. This mission is driven by the belief, inspired by John Lambert, that defenders must shift from thinking in lists to thinking in graphs if they want to overcome attackers’ advantages.
Etay Maor comments, “This is very important. We need to facilitate collaboration between the Defenders across different levels. We’re very passionate about this.”
A significant initiative within this context is the “Attack Flow” project. Attack Flow tackles the challenge faced by defenders, who often focus on individual, atomic attacker behaviors. Instead, Attack Flow uses a new language and tools to describe the flow of ATT&CK techniques. These techniques are then combined into patterns of behavior. This approach enables defenders and leaders to gain a deeper understanding of how adversaries operate, so they can refine their strategies accordingly.
You can see here what an Attack Flow looks like.
With these attack flows, defenders can answer questions like:
- What have adversaries been doing?
- How are adversaries changing?
The answers can help them capture, share and analyze patterns of attack.
Then, they will be able to answer the most important questions:
- What is the next most likely thing they will do?
- What have we missed?
CTID invites the community to participate in its activities and contribute to its knowledge base. You can contact them on LinkedIn.
To learn more about the MITRE ATT&CK framework, watch the entire masterclass here.