Products You May Like
The threat actors behind the Vidar malware have made changes to their backend infrastructure, indicating attempts to retool and conceal their online trail in response to public disclosures about their modus operandi.
“Vidar threat actors continue to rotate their backend IP infrastructure, favoring providers in Moldova and Russia,” cybersecurity company Team Cymru said in a new analysis shared with The Hacker News.
Vidar is a commercial information stealer that’s known to be active since late 2018. It’s also a fork of another stealer malware called Arkei and is offered for sale between $130 and $750 depending on the subscription tier.
Typically delivered through phishing campaigns and sites advertising cracked software, the malware comes with a wide range of capabilities to harvest sensitive information from infected hosts. Vidar has also been observed to be distributed via rogue Google Ads and a malware loader dubbed Bumblebee.
Team Cymru, in a report published earlier January, noted that “Vidar operators have split their infrastructure into two parts; one dedicated to their regular customers and the other for the management team, and also potentially premium / important users.”
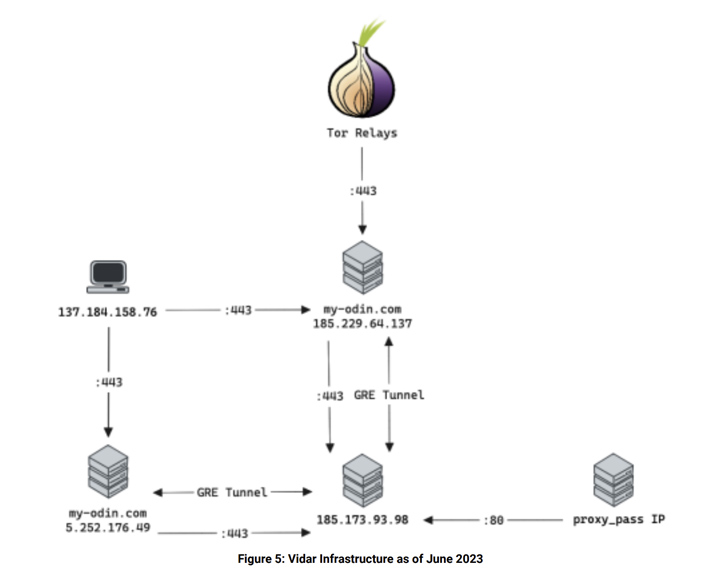
A key domain used by the Vidar actors is my-odin[.]com, which serves as the one-stop destination to manage the panel, authenticate affiliates, and share files.
While previously it was possible to download files from the site without any authentication, performing the same action now redirects the user to a login page. Another change involves updates to the IP address hosting the domain itself.
This includes moving from 186.2.166[.]15 to 5.252.179[.]201 to 5.252.176[.]49 by the end of March 2023, with the threat actors accessing the latter using VPN servers around the same time.
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
“By using VPN infrastructure, which in at least part was also utilized by numerous other benign users, it is apparent that the Vidar threat actors may be taking steps to anonymize their management activities by hiding in general Internet noise,” Team Cymru noted.
The cybersecurity company said it also detected outbound connections from 5.252.176[.]49 to a legitimate website called blonk[.]co as well as a host located in Russia (185.173.93[.]98:443).
The Vidar infrastructure has been found to receive yet another facelift effective May 3, 2023, with the introduction of a new IP address 185.229.64[.]137 hosting the my-odin[.]com domain along with the use of TOR relays by the operators to access their accounts and malware repositories.
The findings “provides further insight into the ‘behind-the-scenes’ operation of Vidar, demonstrating the evolution of its management infrastructure as well as evidence of steps taken by the threat actors to potentially cover their tracks,” the company said.