Products You May Like
A crypter (alternatively spelled cryptor) malware dubbed AceCryptor has been used to pack numerous strains of malware since 2016.
Slovak cybersecurity firm ESET said it identified over 240,000 detections of the crypter in its telemetry in 2021 and 2022. This amounts to more than 10,000 hits per month.
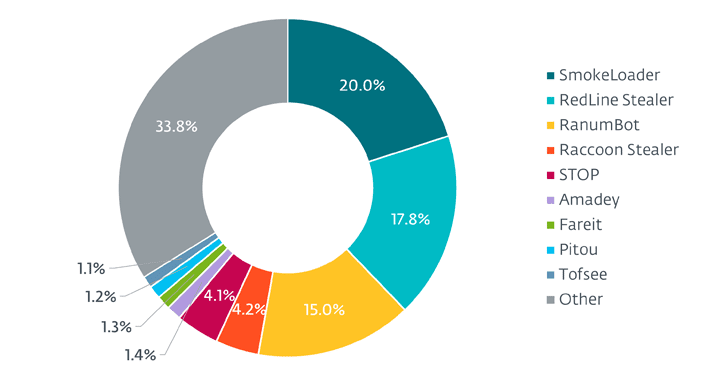
Some of the prominent malware families contained within AceCryptor are SmokeLoader, RedLine Stealer, RanumBot, Raccoon Stealer, Stop ransomware, and Amadey, among others.
The countries with the most detections include Peru, Egypt, Thailand, Indonesia, Turkey, Brazil, Mexico, South Africa, Poland, and India.
AceCryptor was first highlighted by Avast in August 2022, detailing the use of the malware to distribute Stop ransomware and RedLine Stealer on Discord in the form of 7-Zip files.
Crypters are similar to packers, but instead of using compression, they are known to obfuscate the malware code with encryption to make detection and reverse engineering a lot more challenging.
They are also indicative of a trend where malware authors advertise such capabilities for other threat actors, less technically sophisticated or otherwise, who are looking to armor their creations.
“Even though threat actors can create and maintain their own custom cryptors, for crimeware threat actors it often may be a time-consuming or technically difficult task to maintain their cryptor in a so-called FUD (fully undetectable) state,” ESET researcher Jakub Kaloč said.
“Demand for such protection has created multiple crypter-as–a-service (CaaS) options that pack malware.”
AceCryptor-packed malware is delivered via trojanized installers of pirated software, spam emails bearing malicious attachments, or other malware that has already compromised a host.
It’s also suspected to be sold as a CaaS, owing to the fact that it’s used by multiple threat actors to propagate a diverse range of malware families.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
The crypter is heavily obfuscated, incorporating a three-layer architecture to progressively decrypt and unpack each stage and ultimately launch the payload, while also featuring anti-VM, anti-debugging, and anti-analysis techniques to fly under the radar.
The second layer, according to ESET, is said to have been introduced in 2019 as an extra protection mechanism.
The findings come as another crypter service codenamed ScrubCrypt has been leveraged by cryptojacking groups like the 8220 Gang to illicitly mine cryptocurrency on infected hosts.
Earlier this January, Check Point also unearthed a packer known as TrickGate that’s used to deploy a wide range of malware such as TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil for over six years.