Products You May Like
Cybersecurity researchers have shared details about a now-patched security flaw in Windows MSHTML platform that could be abused to bypass integrity protections on targeted machines.
The vulnerability, tracked as CVE-2023-29324 (CVSS score: 6.5), has been described as a security feature bypass. It was addressed by Microsoft as part of its Patch Tuesday updates for May 2023.
Akamai security researcher Ben Barnea, who discovered and reported the bug, noted that all Windows versions are affected, but pointed out Microsoft, Exchange
servers with the March update omit the vulnerable feature.
“An unauthenticated attacker on the internet could use the vulnerability to coerce an Outlook client to connect to an attacker-controlled server,” Barnea said in a report shared with The Hacker News.
“This results in NTLM credentials theft. It is a zero-click vulnerability, meaning it can be triggered with no user interaction.”
It’s also worth noting that CVE-2023-29324 is a bypass for a fix Microsoft put in place in March 2023 to resolve CVE-2023-23397, a critical privilege escalation flaw in Outlook that the company said has been exploited by Russian threat actors in attacks aimed at European entities since April 2022.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
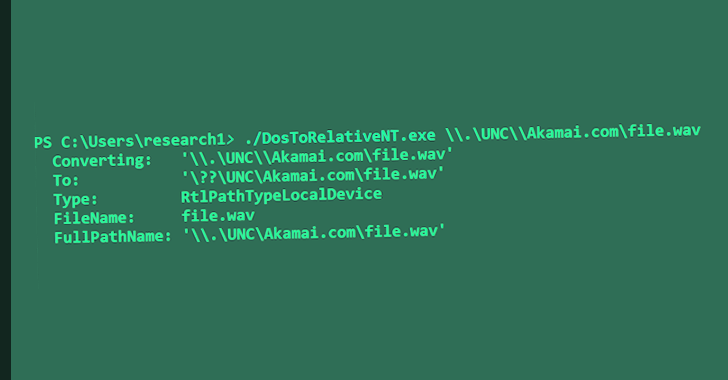
Akamai said the issue stems from complex handling of paths in Windows, thereby allowing a threat actor to craft a malicious URL that can sidestep internet security zone checks.
“This vulnerability is yet another example of patch scrutinizing leading to new vulnerabilities and bypasses,” Barnea said. “It is a zero-click media parsing attack surface that could potentially contain critical memory corruption vulnerabilities.”
In order to stay fully protected, Microsoft is further recommending users to install Internet Explorer Cumulative updates to address vulnerabilities in the MSHTML platform and scripting engine.