Products You May Like
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across its services that were found to leverage OpenAI’s ChatGPT as a lure to propagate about 10 malware families since March 2023.
The development comes against the backdrop of fake ChatGPT web browser extensions being increasingly used to steal users’ Facebook account credentials with an aim to run unauthorized ads from hijacked business accounts.
“Threat actors create malicious browser extensions available in official web stores that claim to offer ChatGPT-based tools,” Meta said. “They would then promote these malicious extensions on social media and through sponsored search results to trick people into downloading malware.”
The social media giant said it has blocked several iterations of a multi-pronged malware campaign dubbed Ducktail over the years, adding it issued a cease and desist letter to individuals behind the operation who are located in Vietnam.
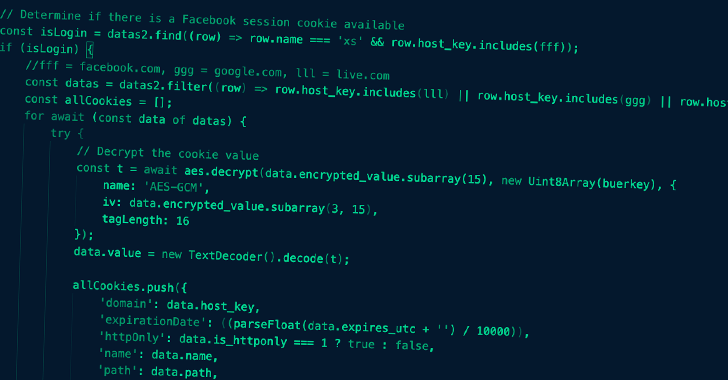
Trend Micro, in a series of tweets last week, detailed an information stealer that’s disguised as a Windows desktop client for ChatGPT to extract passwords, session cookies, and history from Chromium-powered browsers. The company said the malware shares similarities with Ducktail.
Besides ChatGPT, threat actors have also been observed shifting to other “hot-button issues and popular topics” like Google Bard, TikTok marketing tools, pirated software and movies, and Windows utilities to dupe people into clicking on bogus links.
“These changes are likely an attempt by threat actors to ensure that any one service has only limited visibility into the entire operation,” Guy Rosen, chief information security officer at Meta, said.
The attack chains are primarily engineered to target the personal accounts of users who manage or are connected to business pages and advertising accounts on Facebook.
Besides using social media for propagating the ChatGPT-themed malicious URLs, the malware is hosted on a variety of legitimate services such as Buy Me a Coffee, Discord, Dropbox, Google Drive, iCloud, MediaFire, Mega, Microsoft OneDrive, and Trello.
Ducktail isn’t the only stealer malware detected in the wild, for Meta disclosed that it uncovered another novel strain dubbed NodeStealer that’s capable of plundering cookies and passwords from web browsers to ultimately compromise Facebook, Gmail, and Outlook accounts.
The malware is assessed to be of Vietnamese origin, with Meta noting that it “took action to disrupt it and help people who may have been targeted to recover their accounts” within two weeks of it being deployed in late January 2023.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Samples analyzed by the company show that NodeStealer binary is distributed via Windows executables disguised as PDF and XLSX files with filenames relating to marketing and monthly budgets. The files, when opened, deliver JavaScript code that’s designed to exfiltrate sensitive data from Chromium-based browsers.
NodeStealer gets its name from the use of the Node.js cross-platform JavaScript runtime environment, which is bundled along with the main payload, to set up persistence and execute the malware. No new artifacts have been identified as of February 27, 2023.
“After retrieving the Facebook credentials from the target’s browser data, the malware uses it to make several unauthorized requests to Facebook URLs to enumerate account information related to advertising,” Meta said. “The stolen information then enables the threat actor to assess and then use users’ advertising accounts to run unauthorized ads.”
In an attempt to slip under the radar of the company’s anti-abuse systems, the rogue requests are made from the targeted user’s device to the Facebook APIs, lending a veneer of legitimacy to the activity.
To counter such threats, Meta said it’s launching a new support tool that guides users to identify and remove malware, enable businesses to verify connected Business Manager accounts, and require additional authentication when accessing a credit line or changing business administrators.