Products You May Like
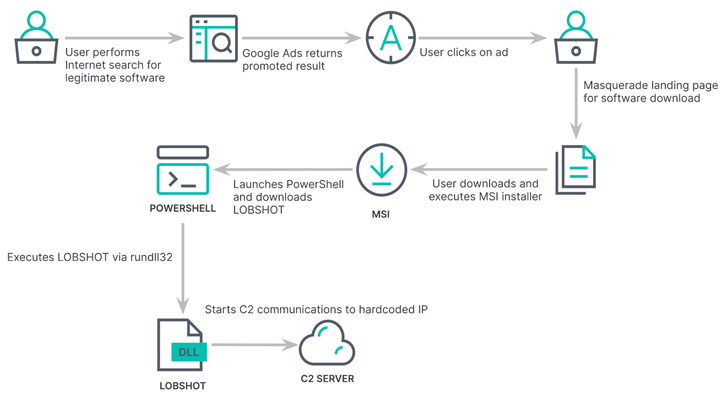
In yet another instance of how threat actors are abusing Google Ads to serve malware, a threat actor has been observed leveraging the technique to deliver a new Windows-based financial trojan and information stealer called LOBSHOT.
“LOBSHOT continues to collect victims while staying under the radar,” Elastic Security Labs researcher Daniel Stepanic said in an analysis published last week.
“One of LOBSHOT’s core capabilities is around its hVNC (Hidden Virtual Network Computing) component. These kinds of modules allow for direct and unobserved access to the machine.”
The American-Dutch company attributed the malware strain to a threat actor known as TA505 based on infrastructure historically connected to the group. TA505 is a financially motivated e-crime syndicate that overlaps with activity clusters tracked under the names Evil Corp, FIN11, and Indrik Spider.
The latest development is significant because it’s a sign that TA505, which is associated with the Dridex banking trojan, is once again expanding its malware arsenal to perpetrate data theft and financial fraud.
LOBSHOT, with early samples dating back to July 2022, is distributed by means of rogue Google ads for legitimate tools like AnyDesk that are hosted on a network of lookalike landing pages maintained by the operators.
The malware incorporates dynamic import resolution (i.e., resolving the names of necessary Windows APIs at runtime), anti-emulation checks, and string obfuscation to evade detection by security software.
Once installed, it makes Windows Registry changes to set up persistence and siphons data from over 50 cryptocurrency wallet extensions present in web browsers like Google Chrome, Microsoft Edge, and Mozilla Firefox.
LOBSHOT’s other notable features revolve around its ability to remotely access the compromised host via an hVNC module and stealthily perform actions on it without attracting the victim’s attention.
“Threat groups are continuing to leverage malvertising techniques to masquerade legitimate software with backdoors like LOBSHOT,” Stepanic said.
“These kinds of malware seem small, but end up packing significant functionality which helps threat actors move quickly during the initial access stages with fully interactive remote control capabilities.”
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
The findings also underscore how an increasing number of adversaries are adopting malvertising and search engine optimization (SEO) poisoning as a technique to redirect users to fake websites and download trojanized installers of popular software.
According to data from eSentire, the threat actors behind GootLoader have been linked to a string of attacks targeting law firms and corporate legal departments in the U.S., Canada, the U.K., and Australia.
GootLoader, active since 2018 and which functions as an initial access-as-a-service operation for ransomware attacks, employ SEO poisoning to entice victims searching for agreements and contracts to infected WordPress blogs that point to links containing the malware.
Besides implementing geofencing to target victims in select regions, the attack chain is designed such that the malware can only be downloaded once per day from the hijacked sites in order to elude discovery by incident responders.
GootLoader’s use of the IP address method to screen already hacked victims, eSentire found, could be used against it to preemptively block the end users’ IP addresses and prevent organizations from potential infections.