Products You May Like
The Chinese nation-state group dubbed Alloy Taurus is using a Linux variant of a backdoor called PingPull as well as a new undocumented tool codenamed Sword2033.
That’s according to findings from Palo Alto Networks Unit 42, which discovered recent malicious cyber activity carried out by the group targeting South Africa and Nepal.
Alloy Taurus is the constellation-themed moniker assigned to a threat actor that’s known for its attacks targeting telecom companies since at least 2012. It’s also tracked by Microsoft as Granite Typhoon (previously Gallium).
Last month, the adversary was attributed to a campaign called Tainted Love targeting telecommunication providers in the Middle East as part of a broader operation referred to as Soft Cell.
Recent cyber espionage attacks mounted by Alloy Taurus have also broadened their victimology footprint to include financial institutions and government entities.
PingPull, first documented by Unit 42 in June 2022, is a remote access trojan that employs the Internet Control Message Protocol (ICMP) for command-and-control (C2) communications.
The Linux flavor of the malware boasts of similar functionalities as its Windows counterpart, allowing it to carry out file operations and run arbitrary commands by transmitting from the C2 server a single upper case character between A and K, and M.
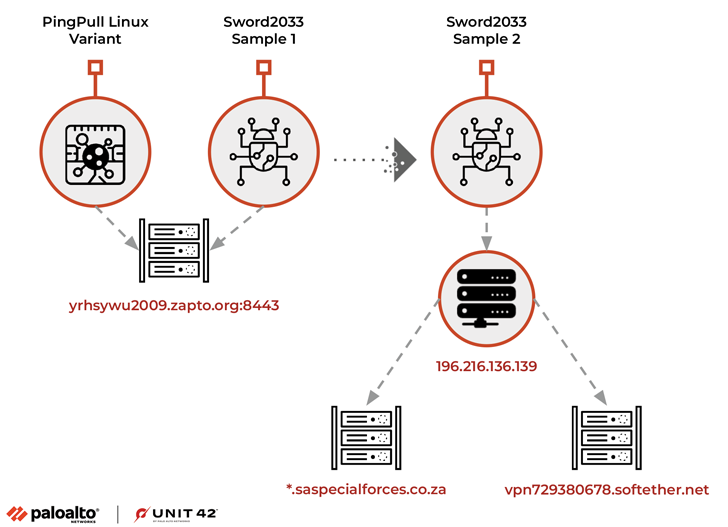
“Upon execution, this sample is configured to communicate with the domain yrhsywu2009.zapto[.]org over port 8443 for C2,” Unit 42 said. “It uses a statically linked OpenSSL (OpenSSL 0.9.8e) library to interact with the domain over HTTPS.”
Interestingly, PingPull’s parsing of the C2 instructions mirrors that of the China Chopper, a web shell widely used by Chinese threat actors, suggesting that the threat actor is repurposing existing source code to devise custom tools.
A closer examination of the aforementioned domain has also revealed the existence of another ELF artifact (i.e., Sword2033) that supports three basic functions, including uploading and exfiltrating files and executing commands.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
The malware’s links to Alloy Taurus stems from the fact that the domain resolved to an IP address that was previously identified as an active indicator of compromise (IoC) associated with a prior campaign targeting companies operating in Southeast Asia, Europe, and Africa.
The targeting of South Africa, per the cybersecurity company, comes against the backdrop of the country holding a joint 10-day naval drill with Russia and China earlier this year.
“Alloy Taurus remains an active threat to telecommunications, finance and government organizations across Southeast Asia, Europe and Africa,” Unit 42 said.
“The identification of a Linux variant of PingPull malware, as well as recent use of the Sword2033 backdoor, suggests that the group continues to evolve their operations in support of their espionage activities.”