Products You May Like
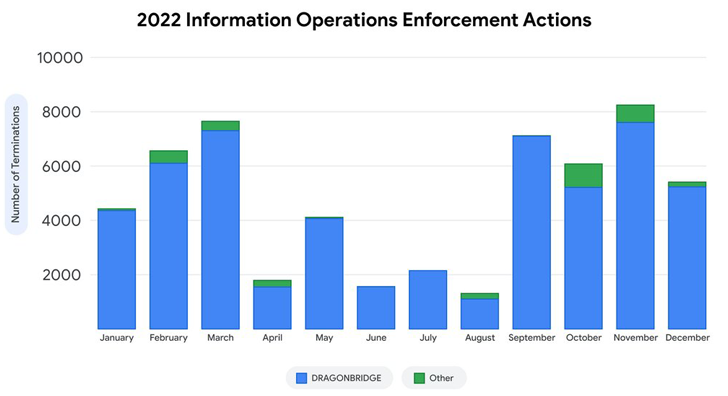
Google on Thursday disclosed it took steps to dismantle over 50,000 instances of activity orchestrated by a pro-Chinese influence operation known as DRAGONBRIDGE in 2022.
“Most DRAGONBRIDGE activity is low quality content without a political message, populated across many channels and blogs,” the company’s Threat Analysis Group (TAG) said in a report shared with The Hacker News. “However, a small fraction of DRAGONBRIDGE accounts also post about current events with messaging that pushes pro-China talking points.”
DRAGONBRIDGE was first exposed by Google-owned Mandiant in July 2022, calling out its unsuccessful efforts in targeting rare earth mining companies in Australia, Canada, and the U.S. with the goal of triggering environmental protests against the firms.
Also known by the name Spamouflage Dragon, the spammy influence network is known to have a presence across multiple platforms, including YouTube, Blogger, Facebook, and Twitter, primarily disseminating narratives critical of the U.S. and favorable of China.
Some of the narratives included claims that the U.S. was interfering in the domestic affairs of other countries, while also highlighting themes of political discord, racial inequality, and inflation in an attempt to show the nation in a negative light.
The criticism of the U.S. notwithstanding, DRAGONBRIDGE’s pro-China content featured narratives praising the country’s COVID-19 pandemic response, condemning pro-democracy protests, and intensifying support for the unification of Taiwan with China.
As part of its efforts to disrupt the threat actor’s activity, Google said it terminated 100,960 accounts across YouTube, Blogger, and AdSense. It further noted that despite the profuse content production, DRAGONBRIDGE failed to attract an organic audience.
That, however, hasn’t stopped the group from persistently tweaking its methods by creating animated political cartoons and producing higher quality content in order to lure real users, TAG researchers cautioned.
In all, 56,771 YouTube channels created by DRAGONBRIDGE were disabled in 2022, with 58% of them having zero subscribers and 42% of the videos posted in those channels having zero views. On top of that, roughly 95% of the Blogger blogs received 10 or lesser views.
“In the rare cases where DRAGONBRIDGE content did receive engagement, it was almost entirely inauthentic, coming from other DRAGONBRIDGE accounts and not from genuine users,” TAG said. “Comment activity was mostly from other DRAGONBRIDGE accounts.”
The tech behemoth also pointed out that the coordinated inauthentic behavior was facilitated by leveraging Google Accounts purchased in bulk from account sellers who create and sell such accounts for profit, in some cases even reusing dormant accounts that were previously used by other actors for mounting financially motivated campaigns.
“Despite their failure to gain traction with an authentic audience, DRAGONBRIDGE generates high volumes of content across multiple platforms, is persistent and continues to experiment in their tactics and techniques,” TAG said.
DRAGONBRIDGE is far from the only pro-China information operation to have emerged in recent years. In August 2022, Mandiant disclosed a campaign dubbed HaiEnergy that employed a network of inauthentic news sites and social media assets to “reshape the international image of Xinjiang.”