Products You May Like
As we are nearing the end of 2022, looking at the most concerning threats of this turbulent year in terms of testing numbers offers a threat-based perspective on what triggers cybersecurity teams to check how vulnerable they are to specific threats. These are the threats that were most tested to validate resilience with the Cymulate security posture management platform between January 1st and December 1st, 2022.
Manjusaka
Date published: August 2022
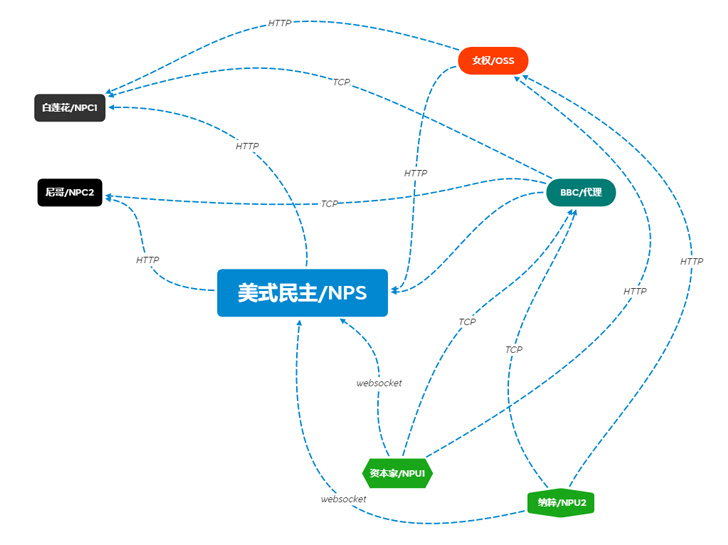
Reminiscent of Cobalt Strike and Sliver framework (both commercially produced and designed for red teams but misappropriated and misused by threat actors), this emerging attack framework holds the potential to be widely used by malicious actors. Written in Rust and Golang with a User Interface in Simple Chinese (see the workflow diagram below), this software is of Chinese origin.
Manjasuka carries Windows and Linux implants in Rust and makes a ready-made C2 server freely available, with the possibility of creating custom implants.
Geopolitical context
Manjasuka was designed for criminal use from the get-go, and 2023 could be defined by increased criminal usage of it as it is freely distributed and would reduce criminal reliance on the misuse of commercially available simulation and emulation frameworks such as Cobalt Strike, Sliver, Ninja, Bruce Ratel C4, etc.
At the time of writing, there was no indication that the creators of Manjasuka are state-sponsored but, as clearly indicated below, China has not been resting this year.
PowerLess Backdoor
Date published: February 2022
Powerless Backdoor is the most popular of this year Iran-related threats, designed to avoid PowerShell detection. Its capabilities include downloading a browser info stealer and a keylogger, encrypting and decrypting data, executing arbitrary commands, and activating a kill process.
Geopolitical context
The number of immediate threats attributed to Iran has jumped from 8 to 17, more than double of the similar 2021 period. However, it has slowed considerably since the September 14th U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctions against Iranian cyber actors, trickling down to a single attack imputed to Iran since then.
The current political tensions within Iran will no doubt impact the frequency of attacks in 2023, but at this stage, it is difficult to evaluate whether those will increase or decrease.
APT 41 targeting U.S. State Governments
Date published: March 2022
Already flagged as very active in 2021, APT41 is a Chinese state-sponsored attacker group activity that showed no sign of slowing down in 2022, and investigations into APT41 activity uncovered evidence of a deliberate campaign targeting U.S. state governments.
APT 41 uses reconnaissance tools, such as Acunetix, Nmap, SQLmap, OneForAll, subdomain3, subDomainsBrute, and Sublist3r. It also launches a large array of attack types, such as phishing, watering hole, and supply-chain attacks, and exploits various vulnerabilities to initially compromise their victims. More recently, they have been seen using the publicly available tool SQLmap as the initial attack vector to perform SQL injections on websites.
This November, a new subgroup, Earth Longhi, joined the already long list of monikers associated with APT 41 (ARIUM, Winnti, LEAD, WICKED SPIDER, WICKED PANDA, Blackfly, Suckfly, Winnti Umbrella, Double Dragon). Earth Longhi was spotted targeting multiple sectors across Taiwan, China, Thailand, Malaysia, Indonesia, Pakistan, and Ukraine.
Geopolitical context
According to Microsoft digital Defense Report 2022, “Many of the attacks coming from China are powered by its ability to find and compile “zero-day vulnerabilities” – unique unpatched holes in software not previously known to the security community. China’s collection of these vulnerabilities appears to have increased on the heels of a new law requiring entities in China to report vulnerabilities they discover to the government before sharing them with others.”
LoLzarus Phishing Attack on DoD Industry
Date published: February 2022
Dubbed LolZarus, a phishing campaign attempted to lure U.S. defense sector job applicants. This campaign was initially identified by Qualys Threat Research, which attributed it to the North-Korean threat actor Lazarus (AKA Dark Seoul, Labyrinth Chollima, Stardust Chollima, BlueNoroff, and APT 38). Affiliated with North Korea’s Reconnaissance General Bureau, this group is both politically and financially motivated and were best known for the high profile attack on Sondy in 2016 and WannaCry ransomware attack in 2017.
The LolZarus phishing campaign relied on at least two malicious documents, Lockheed_Martin_JobOpportunities.docx and salary_Lockheed_Martin_job_opportunities_confidential.doc, that abused macros with aliases to rename the API used and relied on ActiveX Frame1_Layout to automated the attack execution. The macro then loaded the WMVCORE.DLL Windows Media dll file to help deliver the second stage shellcode payload aimed at hijacking control and connecting with the Command & Control server.
Geopolitical context
Another two North Korean notorious attacks flagged by CISA this year include the use of Maui ransomware and activity in cryptocurrency theft. Lazarus subgroup BlueNoroff seems to have branched out of cryptocurrency specialization this year to also target cryptocurrency-connected SWIFT servers and banks. Cymulate associated seven immediate threats with Lazarus since January 1st, 2022.
Industroyer2
Date published: April 2022
Ukraine’s high-alert state, due to the conflict with Russia, demonstrated its efficacy by thwarting an attempted cyber-physical attack targeting high-voltage electric substations. That attack was dubbed Industroyer2 in memory of the 2016’s Industroyer cyber-attack, apparently targeting Ukraine power stations and minimally successful, cutting the power in part of Kyiv for about one hour.
The level of Industroyer2 customized targeting included statically specified executable file sets of unique parameters for specific substations.
Geopolitical context
Ukraine’s cyber-resilience in protecting its critical facilities is unfortunately powerless against kinetic attacks, and Russia appears to have now opted for more traditional military means to destroy power stations and other civilian facilities. According to ENISA, a side-effect of the Ukraine-Russia conflict is a recrudescence of cyber threats against governments, companies, and essential sectors such as energy, transport, banking, and digital infrastructure, in general.
In conclusion, as of the five most concerning threats this year, four have been directly linked with state-sponsored threat actors and the threat actors behind the fifth one are unknown, it appears that geopolitical tensions are at the root of the most burning threat concerns for cybersecurity teams.
As state-sponsored attackers typically have access to cyber resources unattainable by most companies, pre-emptive defense against complex attacks should concentrate on security validation and continuous processes focused on identifying and closing in-context security gaps.
Note: This article was written and contributed by David Klein, Cyber Evangelist at Cymulate.