Products You May Like
A new targeted phishing campaign has zoomed in on a two-factor authentication solution called Kavach that’s used by Indian government officials.
Cybersecurity firm Securonix dubbed the activity STEPPY#KAVACH, attributing it to a threat actor known as SideCopy based on tactical overlaps with prior attacks.
“.LNK files are used to initiate code execution which eventually downloads and runs a malicious C# payload, which functions as a remote access trojan (RAT),” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a new report.
SideCopy, a hacking crew believed to be of Pakistani origin and active since at least 2019, is said to share ties with another actor called Transparent Tribe (aka APT36 or Mythic Leopard).
It’s also known to impersonate attack chains leveraged by SideWinder, a prolific nation-state group that disproportionately singles out Pakistan-based military entities, to deploy its own toolset.
That said, this is not the first time Kavach has emerged as a target for the actor. In July 2021, Cisco Talos detailed an espionage operation that was undertaken to steal credentials from Indian government employees.
Kavach-themed decoy apps have since been co-opted by Transparent Tribe in its attacks targeting India since the start of the year.
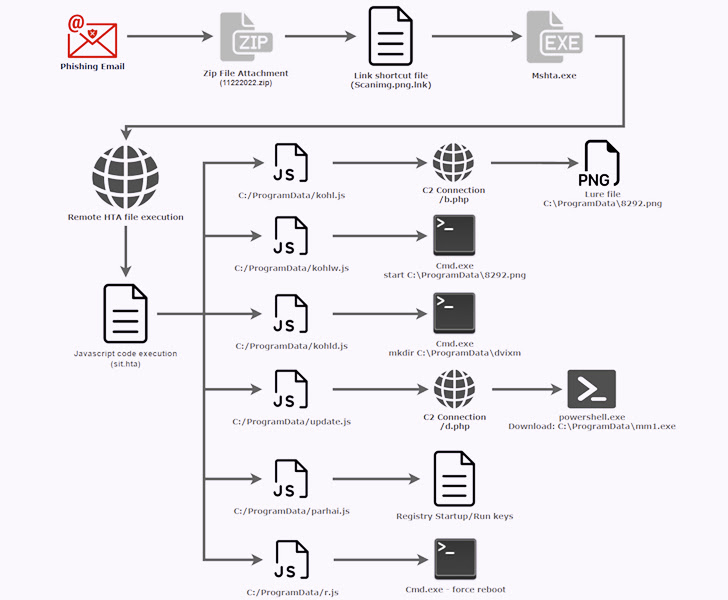
The latest attack sequence observed by Securonix over the past couple of weeks entails using phishing emails to lure potential victims into opening a shortcut file (.LNK) to execute a remote .HTA payload using the mshta.exe Windows utility.
The HTML application, the company said, “was discovered being hosted on a likely compromised website, nested inside an obscure ‘gallery’ directory designed to store some of the site’s images.”
The compromised website in question is incometaxdelhi[.]org, the official website for India’s Income Tax department pertaining to the Delhi region. The malicious file is no longer available on the portal.
In the next phase, running the .HTA file leads to the execution of obfuscated JavaScript code that’s designed to show a decoy image file that features an announcement from the Indian Ministry of Defence a year ago in December 2021.
The JavaScript code further downloads an executable from a remote server, establishes persistence via Windows Registry modifications, and reboots the machine to automatically launch the binary post startup.
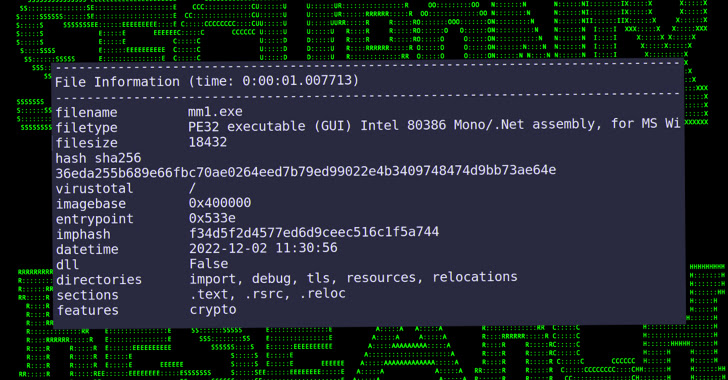
The binary file, for its part, functions as a backdoor that enables the threat actor to execute commands sent from an attacker-controlled domain, fetch and run additional payloads, take screenshots, and exfiltrate files.
The exfiltration component also includes an option to specifically search for a database file (“kavach.db”) created by the Kavach app on the system to store the credentials.
It’s worth noting that the aforementioned infection chain was disclosed by the MalwareHunterTeam in a series of tweets on December 8, 2022, describing the remote access trojan as MargulasRAT.
“Based on correlated data from the binary samples obtained of the RAT used by the threat actors, this campaign has been going on against Indian targets undetected for the last year,” the researchers said.