Products You May Like
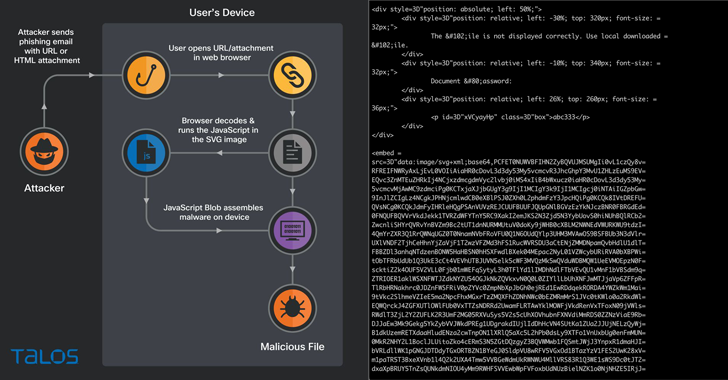
Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG) images embedded in HTML email attachments.
The new distribution method was spotted by Cisco Talos, which said it identified fraudulent email messages featuring HTML attachments with encoded SVG images that incorporate HTML script tags.
HTML smuggling is a technique that relies on using legitimate features of HTML and JavaScript to run encoded malicious code contained within the lure attachment and assemble the payload on a victim’s machine as opposed to making an HTTP request to fetch the malware from a remote server.
In other words, the idea is to evade email gateways by storing a binary in the form of a JavaScript code that’s decoded and downloaded when opened via a web browser.
The attack chain spotted by the cybersecurity company concerns a JavaScript that’s smuggled inside of the SVG image and executed when the unsuspecting email recipient launches the HTML attachment.
“When the victim opens the HTML attachment from the email, the smuggled JavaScript code inside the SVG image springs into action, creating a malicious ZIP archive and then presenting the user with a dialog box to save the file,” researchers Adam Katz and Jaeson Schultz said.
The ZIP archive is also password-protected, requiring users to enter a password that’s displayed in the HTML attachment, following which an ISO image is extracted to run the Qakbot trojan.
The finding comes as recent research from Trustwave SpiderLabs shows that HTML smuggling attacks are a common occurrence, with .HTML (11.39%) and .HTM (2.7%) files accounting for the second most spammed file attachment type after .JPG images (25.29%) in September 2022.
“Having robust endpoint protection can prevent execution of potentially obfuscated scripts, and prevent scripts from launching downloaded executable content,” the researchers said.
“HTML smuggling’s ability to bypass content scanning filters means that this technique will probably be adopted by more threat actors and used with increasing frequency.”