Products You May Like
A high-severity vulnerability has been disclosed in the SQLite database library, which was introduced as part of a code change dating all the way back to October 2000 and could enable attackers to crash or control programs.
Tracked as CVE-2022-35737 (CVSS score: 7.5), the 22-year-old issue affects SQLite versions 1.0.12 through 3.39.1, and has been addressed in version 3.39.2 released on July 21, 2022.
“CVE-2022-35737 is exploitable on 64-bit systems, and exploitability depends on how the program is compiled,” Trail of Bits researcher Andreas Kellas said in a technical write-up published today.
“Arbitrary code execution is confirmed when the library is compiled without stack canaries, but unconfirmed when stack canaries are present, and denial-of-service is confirmed in all cases.”
Programmed in C, SQLite is the most widely used database engine, included by default in Android, iOS, Windows, and macOS, as well as popular web browsers such as Google Chrome, Mozilla Firefox, and Apple Safari.
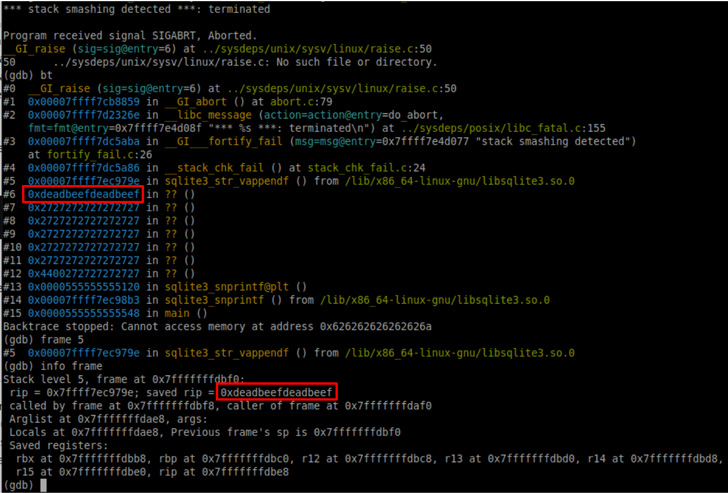
The vulnerability discovered by Trail of Bits concerns an integer overflow bug that occurs when extremely large string inputs are passed as parameters to the SQLite implementations of the printf functions, which, in turn, make use of another function to handle the string formatting (“sqlite3_str_vappendf“).
However, a successful weaponization of the flaw banks on the prerequisite that the string contains the %Q, %q, or %w format substitution types, potentially leading to a program crash when user-controlled data is written beyond the bounds of a stack-allocated buffer.
“If the format string contains the ‘!’ special character to enable unicode character scanning, then it is possible to achieve arbitrary code execution in the worst case, or to cause the program to hang and loop (nearly) indefinitely,” Kellas explained.
The vulnerability is also an example of a scenario that was once deemed impractical decades ago — allocating 1GB strings as input — rendered feasible with the advent of 64-bit computing systems.
“It’s a bug that may not have seemed like an error at the time that it was written (dating back to 2000 in the SQLite source code) when systems were primarily 32-bit architectures,” Kellas said.