Products You May Like
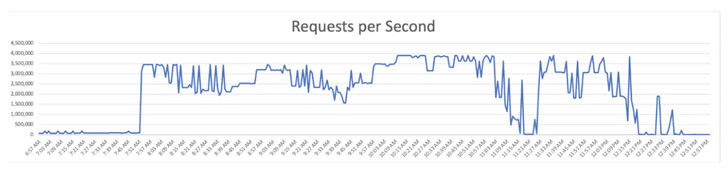
Cybersecurity company Imperva has disclosed that it mitigated a distributed denial-of-service (DDoS) attack with a total of over 25.3 billion requests on June 27, 2022.
The “strong attack,” which targeted an unnamed Chinese telecommunications company, is said to have lasted for four hours and peaked at 3.9 million requests per second (RPS).
“Attackers used HTTP/2 multiplexing, or combining multiple packets into one, to send multiple requests at once over individual connections,” Imperva said in a report published on September 19.
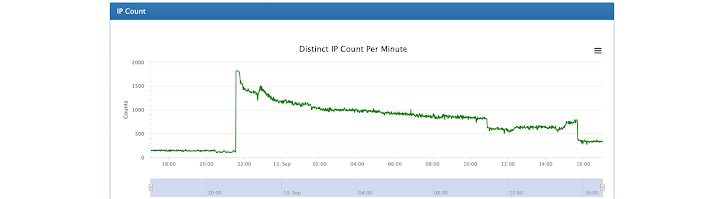
The attack was launched from a botnet that comprised nearly 170,000 different IP addresses spanning routers, security cameras, and compromised servers located in more than 180 countries, primarily the U.S., Indonesia, and Brazil.
The disclosure also comes as web infrastructure provider Akamai said it fielded a new DDoS assault aimed at a customer based in Eastern Europe on September 12, with attack traffic spiking at 704.8 million packets per second (pps).
The same victim was previously targeted on July 21, 2022, in a similar fashion in which the attack volume ramped up to 853.7 gigabits per second (Gbps) and 659.6 million pps over a period of 14 hours.
Akamai’s Craig Sparling said the company has been “bombarded relentlessly with sophisticated distributed denial-of-service (DDoS) attacks,” indicating that the offensives could be politically motivated in the face of Russia’s ongoing war against Ukraine.
Both the disruptive attempts were UDP flood attacks where the attacker targets and overwhelms arbitrary ports on the target host with User Datagram Protocol (UDP) packets.
UDP, being both connectionless and session-less, makes it an ideal networking protocol for handling VoIP traffic. But these same traits can also render it more susceptible to exploitation.
“Without an initial handshake to ensure a legitimate connection, UDP channels can be used to send a large volume of traffic to any host,” NETSCOUT says.
“There are no internal protections that can limit the rate of a UDP flood. As a result, UDP flood DoS attacks are exceptionally dangerous because they can be executed with a limited amount of resources.”