Products You May Like
Major financial and insurance companies located in French-speaking nations in Africa have been targeted over the past two years as part of a persistent malicious campaign codenamed DangerousSavanna.
Countries targeted include Ivory Coast, Morocco, Cameroon, Senegal, and Togo, with the spear-phishing attacks heavily focusing on Ivory Coast in recent months, Israeli cybersecurity firm Check Point said in a Tuesday report.
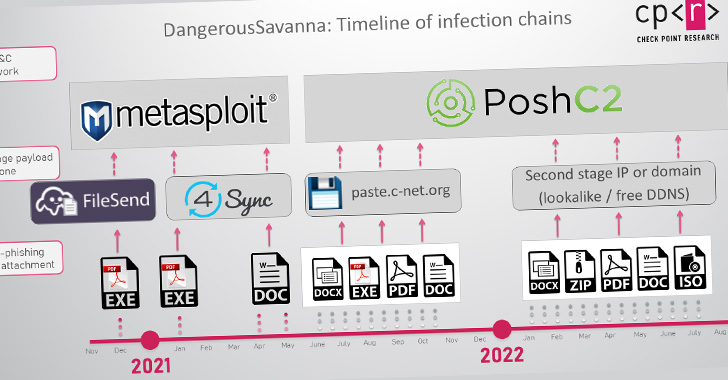
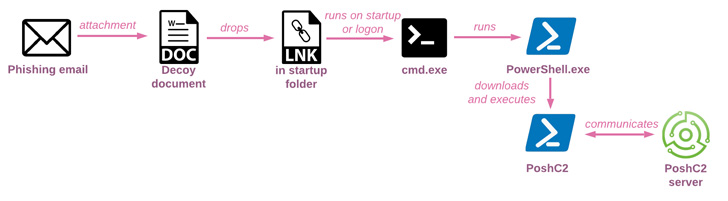
Infection chains entail targeting employees of financial institutions with social engineering messages containing malicious attachments as a means of initial access, ultimately leading to the deployment of off-the-shelf malware such as Metasploit, PoshC2, DWservice, and AsyncRAT.
“The threat actors’ creativity is on display in the initial infection stage, as they persistently pursue the employees of the targeted companies, constantly changing infection chains that utilize a wide range of malicious file types, from self-written executable loaders and malicious documents, to ISO, LNK, JAR and VBE files in various combinations,” the company said.
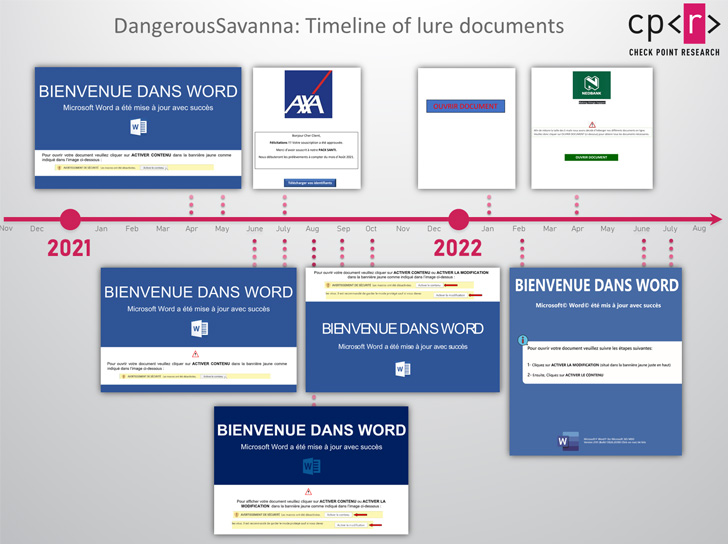
The phishing emails are written in French and sent using Gmail and Hotmail services, even as the messages also impersonate other financial institutions in Africa to boost their credibility.
While attacks in 2021 leveraged macro-laced Microsoft Word documents as lures, the company’s decision to block macros in files downloaded from the internet by default earlier this year has led the DangerousSavanna actors to pivot to PDF and ISO files.
Furthermore, the first wave of attacks from the end of 2020 to the beginning of 2021 involved the use of bespoke .NET-based tools, which came disguised as PDF files attached to phishing emails, to retrieve next-stage droppers and loaders from remote servers.
Regardless of the method used, post-exploitation activities carried out after obtaining an initial foothold include establishing persistence, performing reconnaissance, and delivering additional payloads to remotely control the host, kill anti-malware processes, and log keystrokes.
The exact provenance of the threat actor remains unclear, but the frequent shift in its tools and methods demonstrates their knowledge of open-source software and their ability to fine-tune their tactics for maximizing financial gain.
“If one infection chain didn’t work out, they changed the attachment and the lure and tried targeting the same company again and again trying to find an entry point,” Check Point said. “With social engineering via spear-phishing, all it takes is one incautious click by an unsuspecting user.”