Products You May Like
The Black Basta ransomware-as-a-service (RaaS) syndicate has amassed nearly 50 victims in the U.S., Canada, the U.K., Australia, and New Zealand within two months of its emergence in the wild, making it a prominent threat in a short window.
“Black Basta has been observed targeting a range of industries, including manufacturing, construction, transportation, telcos, pharmaceuticals, cosmetics, plumbing and heating, automobile dealers, undergarments manufacturers, and more,” Cybereason said in a report.
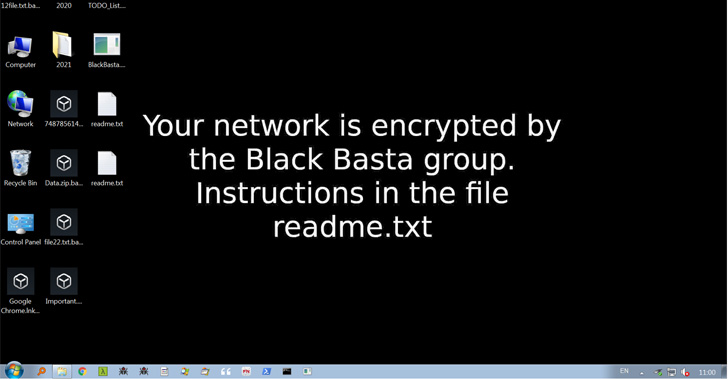
Similar to other ransomware operations, Black Basta is known to employ the tried-and-tested tactic of double extortion to plunder sensitive information from the targets and threaten to publish the stolen data unless a digital payment is made.
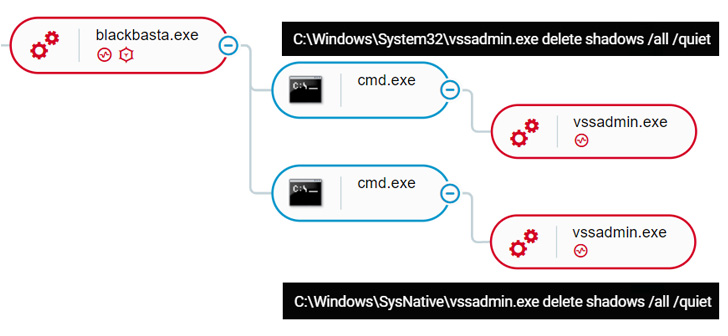
A new entrant in the already crowded ransomware landscape, intrusions involving the threat have leveraged QBot (aka Qakbot) as a conduit to maintain persistence on the compromised hosts and harvest credentials, before moving laterally across the network and deploying the file-encrypting malware.
Furthermore, the actors behind Black Basta have developed a Linux variant designed to strike VMware ESXi virtual machines (VMs) running on enterprise servers, putting it on par with other groups such as LockBit, Hive, and Cheerscrypt.
The findings come as the cybercriminal syndicate added Elbit Systems of America, a manufacturer of defense, aerospace, and security solutions, to the list of its victims over the weekend, according to security researcher Ido Cohen.
Black Basta is said to be comprised of members belonging to the Conti group after the latter shuttered its operations in response to increased law enforcement scrutiny and a major leak that saw its tools and tactics entering the public domain after siding with Russia in the country’s war against Ukraine.
“I cannot shoot anything, but I can fight with a keyboard and mouse,” the Ukrainian computer specialist behind the leak, who goes by the pseudonym Danylo and released the treasure trove of data as a form of digital retribution, told CNN in March 2022.
The Conti team has since refuted that it’s associated with Black Basta. Last week, it decommissioned the last of its remaining public-facing infrastructure, including two Tor servers used to leak data and negotiate with victims, marking an official end to the criminal enterprise.
In the interim, the group continued to maintain the facade of an active operation by targeting the Costa Rican government, while some members transitioned to other ransomware outfits and the brand underwent a organizational revamp that has seen it devolve into smaller subgroups with different motivations and business models ranging from data theft to working as independent affiliates.
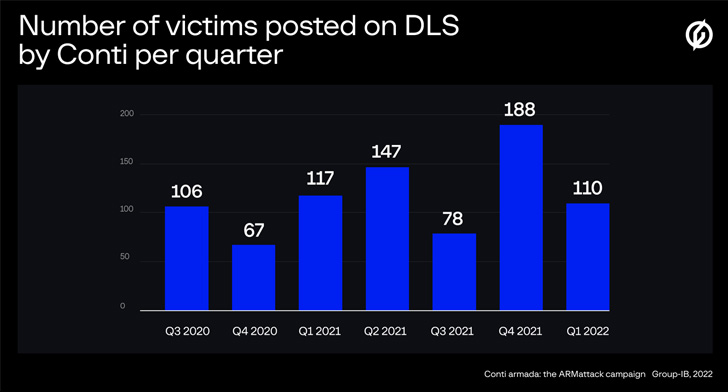
According to a comprehensive report from Group-IB detailing its activities, the Conti group is believed to have victimized more than 850 entities since it was first observed in February 2020, compromising over 40 organizations worldwide as part of a “lightning-fast” hacking spree that lasted from November 17 to December 20, 2021.
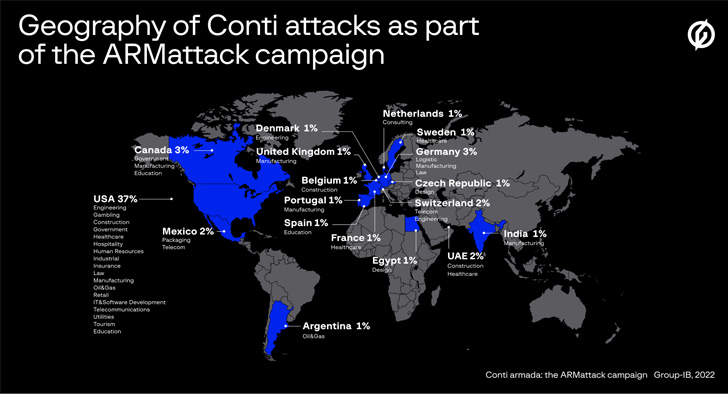
Dubbed “ARMattack” by the Singapore-headquartered company, the intrusions were primarily directed against U.S. organizations (37%), followed by Germany (3%), Switzerland (2%), the U.A.E. (2%), the Netherlands, Spain, France, the Czech Republic, Sweden, Denmark, and India (1% each).
The top five sectors historically targeted by Conti have been manufacturing (14%), real estate (11.1%), logistics (8.2%), professional services (7.1%), and trade (5.5%), with the operators specifically singling out companies in the U.S. (58.4%), Canada (7%), the U.K. (6.6%), Germany (5.8%), France (3.9%), and Italy (3.1%).
“Conti’s increased activity and the data leak suggest that ransomware is no longer a game between average malware developers, but an illicit RaaS industry that gives jobs to hundreds of cybercriminals worldwide with various specializations,” Group-IB’s Ivan Pisarev said.
“In this industry, Conti is a notorious player that has in fact created an ‘IT company’ whose goal is to extort large sums. It is clear […] that the group will continue its operations, either on its own or with the help of its ‘subsidiary’ projects.”