Products You May Like
An unofficial security patch has been made available for a new Windows zero-day vulnerability in the Microsoft Support Diagnostic Tool (MSDT), even as the Follina flaw continues to be exploited in the wild.
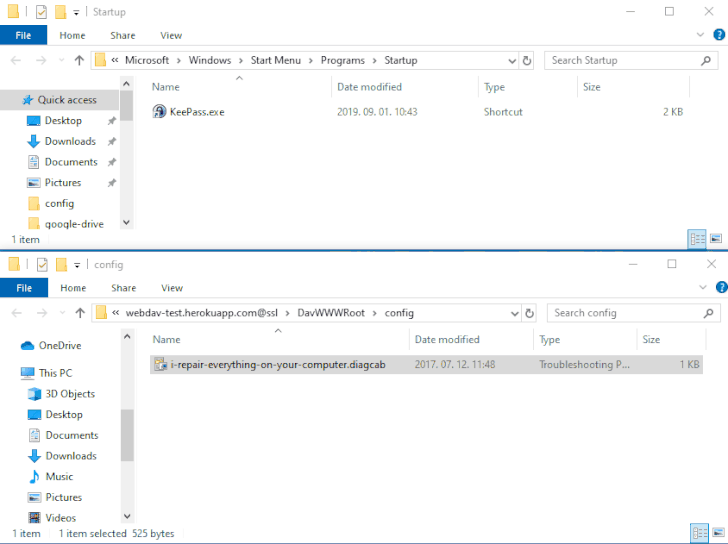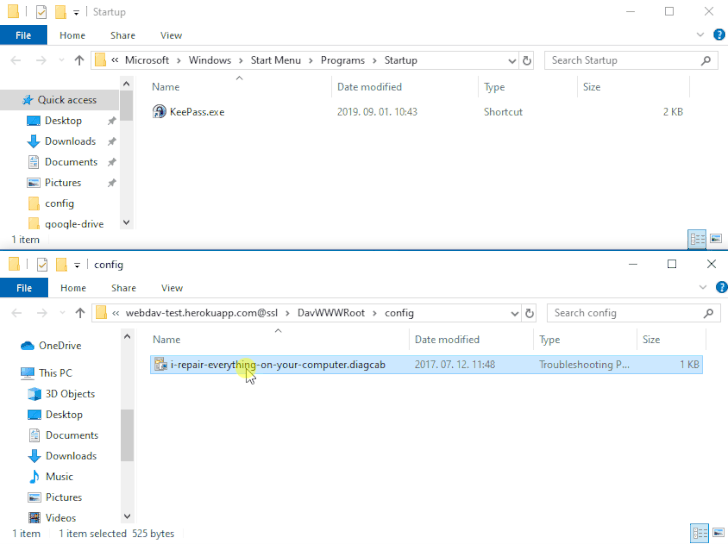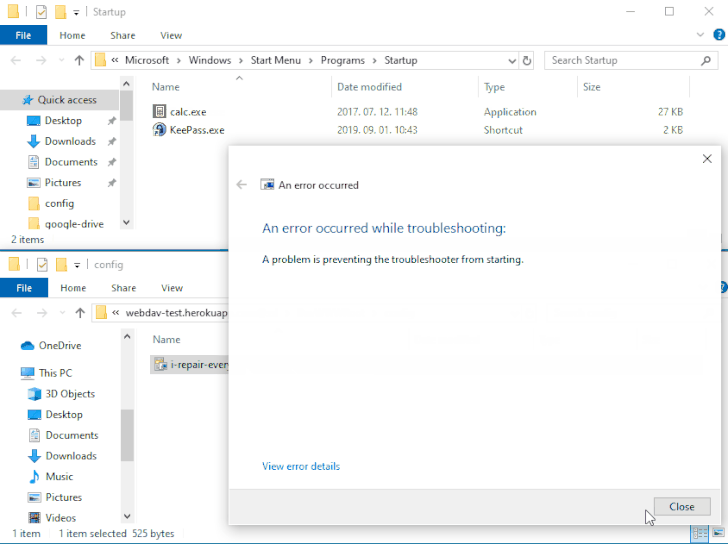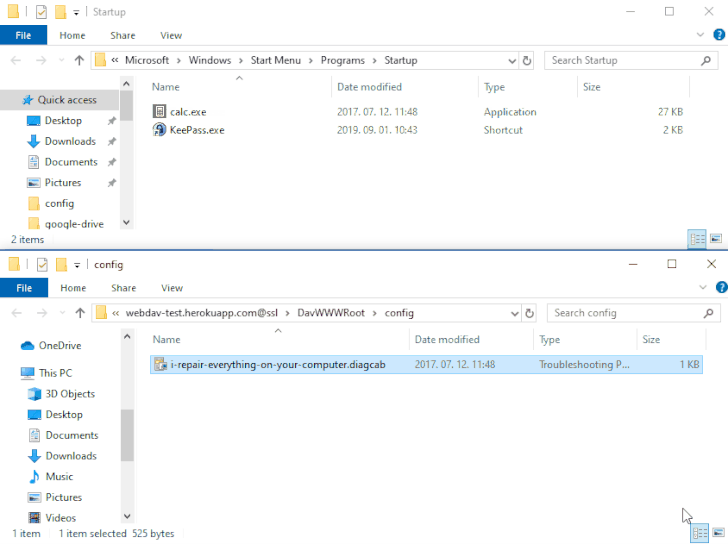
The issue — referenced as DogWalk — relates to a path traversal flaw that can be exploited to stash a malicious executable file to the Windows Startup folder when a potential target opens a specially crafted “.diagcab” archive file that contains a diagnostics configuration file.
The idea is that the payload would get executed the next time the victim logs in to the system after a restart. The vulnerability affects all Windows versions, starting from Windows 7 and Server Server 2008 to the latest releases.
DogWalk was originally disclosed by security researcher Imre Rad in January 2020 after Microsoft, having acknowledged the problem, deemed it as not a security issue.
“There are a number of file types that can execute code in such a way but aren’t technically ‘executables,'” the tech giant said at the time. “And a number of these are considered unsafe for users to download/receive in email, even ‘.diagcab’ is blocked by default in Outlook on the web and other places.”
While all files downloaded and received via email include a Mark-of-the-Web (MOTW) tag that’s used to determine their origin and trigger an appropriate security response, 0patch’s Mitja Kolsek noted that the MSDT application is not designed to check this flag and hence allows the .diagcab file to be opened without warning.
“Outlook is not the only delivery vehicle: such file is cheerfully downloaded by all major browsers including Microsoft Edge by simply visiting(!) a website, and it only takes a single click (or mis-click) in the browser’s downloads list to have it opened,” Kolsek said.
“No warning is shown in the process, in contrast to downloading and opening any other known file capable of executing [the] attacker’s code.”
The patches and the renewed interest in the zero-day bug follow active exploitation of the “Follina” remote code execution vulnerability by leveraging malware-laced Word documents that abuse the “ms-msdt:” protocol URI scheme.
According to enterprise security firm Proofpoint, the flaw (CVE-2022-30190, CVSS score: 7.8) is being weaponized by a threat actor tracked as TA570 to deliver the QBot (aka Qakbot) information-stealing trojan.
“Actor uses thread hijacked messages with HTML attachments which, if opened, drop a ZIP archive,” the company said in a series of tweets detailing the phishing attacks.
“Archive contains an IMG with a Word doc, shortcut file, and DLL. The LNK will execute the DLL to start QBot. The doc will load and execute a HTML file containing PowerShell abusing CVE-2022-30190 used to download and execute Qbot.”
QBot has also been employed by initial access brokers to gain initial access to target networks, enabling ransomware affiliates to abuse the foothold to deploy file-encrypting malware.
The DFIR Report, earlier this year, also documented how QBot infections move at a rapid pace, enabling the malware to harvest browser data and Outlook emails a mere 30 minutes after initial access and propagate the payload to an adjacent workstation around the 50-minute mark.