Products You May Like
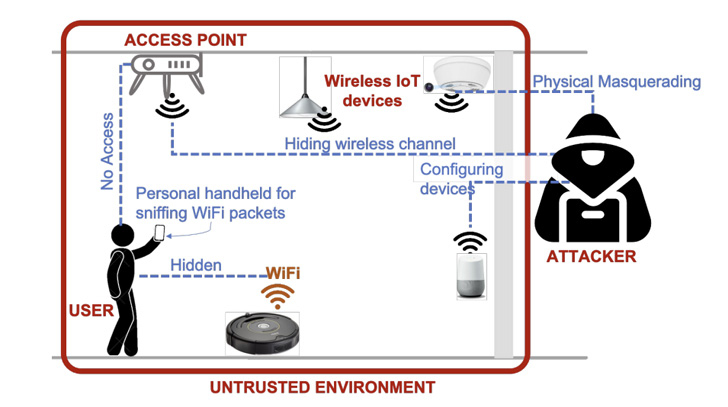
A group of academics has devised a system that can be used on a phone or a laptop to identify and locate Wi-Fi-connected hidden IoT devices in unfamiliar physical spaces.
With hidden cameras being increasingly used to snoop on individuals in hotel rooms and Airbnbs, the goal is to be able to pinpoint such rogue devices without much of a hassle.
The system, dubbed Lumos, is designed with this intent in mind and to “visualize their presence using an augmented reality interface,” said Rahul Anand Sharma, Elahe Soltanaghaei, Anthony Rowe, and Vyas Sekar of Carnegie Mellon University in a new paper.
At its core, the platform works by snuffing and collecting encrypted wireless packets over the air to detect and identify concealed devices. Subsequently, it estimates the location of each identified device with respect to the user as they walk around the perimeter of the space.
The localization module, for its part, combines signal strength measurements that are available in 802.11 packets (aka Received Signal Strength Indicator or RSSI) with relative user position determined by visual inertial odometry (VIO) information on mobile phones.
On Apple’s iOS devices, for instance, the positional tracking is achieved by means of ARKit, a developer API that makes it possible to build augmented reality experiences by taking advantage of the phone’s camera, CPU, GPU, and motion sensors.
“As the user walks closer to each device, the RSSI values corresponding to those data points increase and then reduce as she walks away from the device,” the researchers said. “Lumos leverages the spatial measurements of RSSI values and their variations to estimate the location of each device.”
What’s more, Lumos can localize IoT devices irrespective of the user’s walking speed. Also incorporated is a fingerprinting module that analyzes the captured 802.11 traffic patterns using a machine learning model to identify the devices based on the MAC addresses.
The research evaluated Lumos across 44 different IoT devices spanning various types, models, and brands across six different environments, finding that it can identify hidden devices with 95% accuracy and locate them with a median error of 1.5m within 30 minutes in a two-bedroom, 1000 sq.ft. apartment.
That said, an advanced attacker can leverage techniques like MAC address randomization to evade detection and sidestep localization by arbitrarily modifying the devices’ transmit power.
“Lumos can potentially generalize across different device brands and models, as long as it has seen at least one device with similar behavior in the training phase,” the researchers said, pointing to how the system can even identify unprofiled devices.