Products You May Like
Operators associated with the Lazarus sub-group BlueNoroff have been linked to a series of cyberattacks targeting small and medium-sized companies worldwide with an aim to drain their cryptocurrency funds, in what’s yet another financially motivated operation mounted by the prolific North Korean state-sponsored actor.
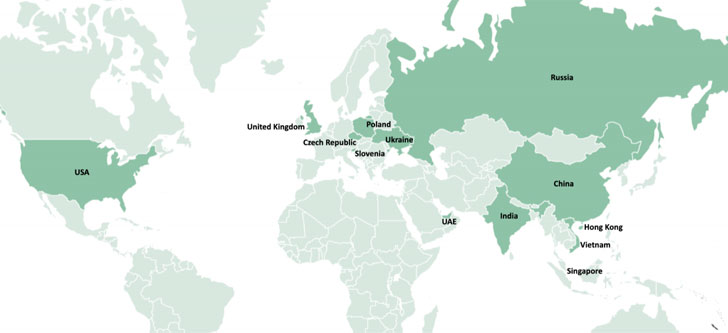
Russian cybersecurity company Kaspersky, which is tracking the intrusions under the name “SnatchCrypto,” noted that the campaign has been running since at 2017, adding the attacks are aimed at startups in the FinTech sector located in China, Hong Kong, India, Poland, Russia, Singapore, Slovenia, the Czech Republic, the U.A.E., the U.S., Ukraine, and Vietnam.
“The attackers have been subtly abusing the trust of the employees working at targeted companies by sending them a full-featured Windows backdoor with surveillance functions, disguised as a contract or another business file,” the researchers said. “In order to eventually empty the victim’s crypto wallet, the actor has developed extensive and dangerous resources: complex infrastructure, exploits and malware implants.”
BlueNoroff, and the larger Lazarus umbrella, are known for deploying a diverse arsenal of malware for a multi-pronged assault on businesses to illicitly procure funds, including relying on a mix of advanced phishing tactics and sophisticated malware, for the sanctions-hit North Korean regime and generate revenue for its nuclear weapons and ballistic missile programs.
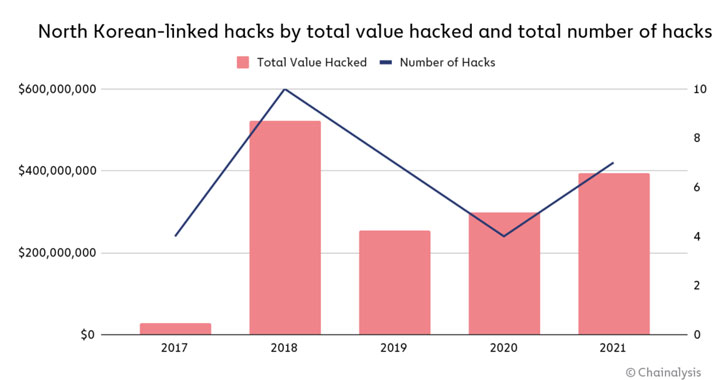
If anything, these cyber offensives are paying off big time. According to a new report published by blockchain analytics firm Chainalysis, the Lazarus Group has been linked to seven attacks on cryptocurrency platforms that extracted almost $400 million worth of digital assets in 2021 alone, up from $300 million in 2020.
“These attacks targeted primarily investment firms and centralized exchanges […] to siphon funds out of these organizations’ internet-connected ‘hot’ wallets into DPRK-controlled addresses,” the researchers said. “Once North Korea gained custody of the funds, they began a careful laundering process to cover up and cash out” through mixers to obscure the trail.
Documented malicious activity involving the nation-state actor have take the form of cyber-enabled heists against foreign financial institutions, notably the SWIFT banking network hacks in 2015-2016, with recent campaigns resulting in the deployment of a backdoor called AppleJeus that poses as a cryptocurrency trading platform to plunder and transfer money to their accounts.
The SnatchCrypto attacks are no different in that they concoct elaborate social engineering schemes to build trust with their targets by posing as legitimate venture capitalist firms, only to use bait the victims into opening malware-laced documents that retrieve a payload designed to run a malicious executable received over an encrypted channel from a remote server.
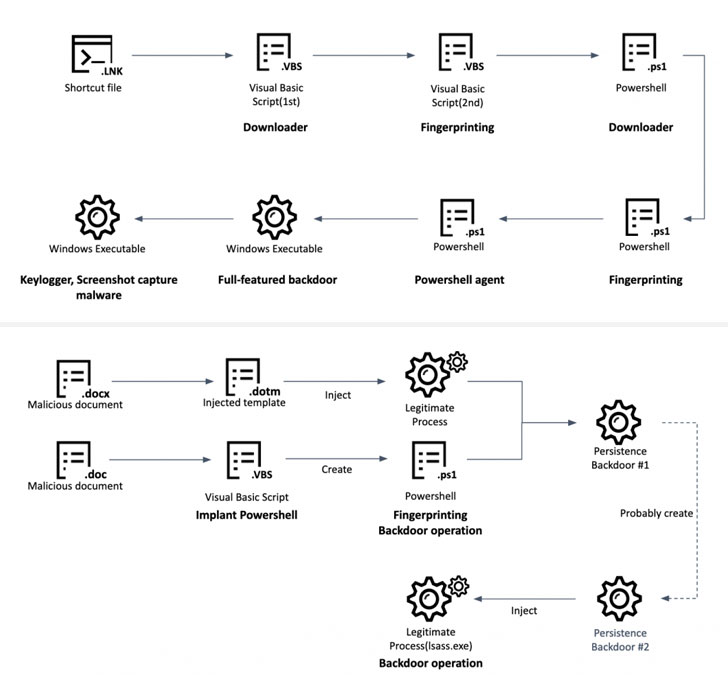
An alternative method used to trigger the infection chain is the use of Windows shortcut files (“.LNK”) to fetch the next-stage malware, a Visual Basic Script, that then acts a jump off point to execute a series of intermediary payloads, before installing a full-featured backdoor that comes with “enriched” capabilities to capture screenshots, record keystrokes, steal data from Chrome browser, and execute arbitrary commands.
The ultimate goal of the attacks, however, is to monitor financial transactions of the compromised users and steal cryptocurrency. Should a potential target use a Chrome extension like Metamask to manage crypto wallets, the adversary stealthily moves to locally replace the main component of the extension with a fake version that alerts the operators every time a large transfer is kicked off to another account.
To siphon the funds, malicious code injection is performed to intercept and modify the transaction details on demand. “The attackers modify not only the recipient [wallet] address, but also push the amount of currency to the limit, essentially draining the account in one move,” the researchers explained.
“Cryptocurrency is a heavily targeted sector when it comes to cybercrime due to the decentralized nature of the currencies and the fact that, unlike with credit card or bank transfers, the transaction happens quickly and is impossible to reverse,” Erich Kron, security awareness advocate at KnowBe4, said in a statement.
“Nation-states, especially those under strict tariffs or other financial restrictions, can benefit greatly by stealing and manipulating cryptocurrency. Many times, a cryptocurrency wallet can contain multiple types of cryptocurrency, making them a very appealing target,” Kron added.