Products You May Like
Microsoft on Monday disclosed details of a recently patched security vulnerability in Apple’s macOS operating system that could be weaponized by a threat actor to expose users’ personal information.
Tracked as CVE-2021-30970, the flaw concerns a logic issue in the Transparency, Consent and Control (TCC) security framework, which enables users to configure the privacy settings of their apps and provide access to protected files and app data. The Security & Privacy pane in the macOS System Preferences app serves as the front end of TCC.
Microsoft 365 Defender Research Team, which reported the flaw to Apple on July 15, 2021, dubbed the flaw “powerdir.” Apple addressed the issue as part of macOS 11.6 and 12.1 updates released in December 2021 with improved state management.
While Apple does enforce a policy that limits access to TCC to only apps with full disk access, it’s possible to orchestrate an attack wherein a malicious application could work around its privacy preferences to retrieve sensitive information from the machine, potentially allowing an adversary to access microphone to record private conversations or capture screenshots of sensitive information displayed on the user’s screen.
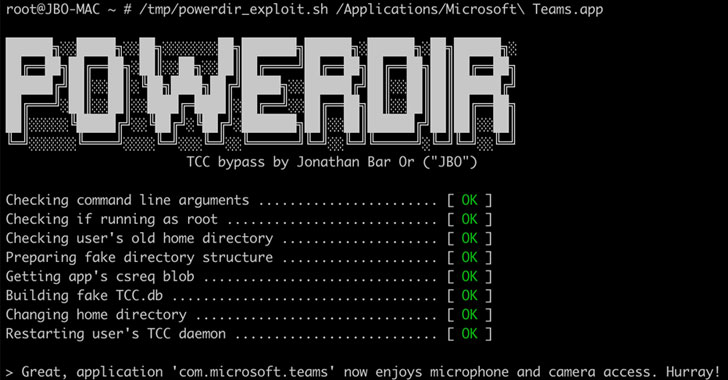
“We discovered that it is possible to programmatically change a target user’s home directory and plant a fake TCC database, which stores the consent history of app requests,” Jonathan Bar Or of Microsoft 365 Defender Research Team said. “If exploited on unpatched systems, this vulnerability could allow a malicious actor to potentially orchestrate an attack based on the user’s protected personal data.”
In other words, if a bad actor gains full disk access to the TCC databases, the intruder could edit it to grant arbitrary permissions to any app of their choice, including their own, effectively permitting the app run with configurations previously not consented to.
CVE-2021-30970 is also the third TCC-related bypass vulnerability to be discovered after CVE-2020-9934 and CVE-2020-27937, both of which have since been remediated by Apple. Then in May 2021, the company also patched a then zero-day flaw in the same component (CVE-2021-30713) that could allow an attacker to gain full disk access, screen recording, or other permissions without users’ explicit consent.
“This shows that even as macOS or other operating systems and applications become more hardened with each release, software vendors like Apple, security researchers, and the larger security community, need to continuously work together to identify and fix vulnerabilities before attackers can take advantage of them,” Bar Or said.