Products You May Like
Google has rolled out the first round of updates to its Chrome web browser for 2022 to fix 37 security issues, one of which is rated Critical in severity and could be exploited to pass arbitrary code and gain control over a victim’s system.
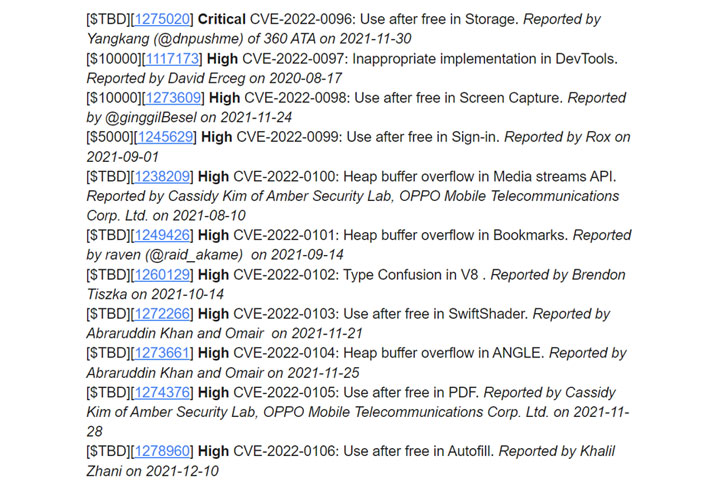
Tracked as CVE-2022-0096, the flaw relates to a use-after-free bug in the Storage component, which could have devastating effects ranging from corruption of valid data to the execution of malicious code on a compromised machine.
Security researcher Yangkang (@dnpushme) of Qihoo 360 ATA, who has previously disclosed zero-day vulnerabilities in Apple’s WebKit, has been credited with discovering and reporting the flaw on November 30, 2021.
It’s also worth pointing out that 24 of the 37 uncovered flaws came from external researchers, including its Google Project Zero initiative, while the others were flagged as part of its ongoing internal security work. Of the 24 bugs, 10 are rated High, another 10 are rated Medium, and three are rated as Low in severity.
The updates arrive after a busy 2021, which saw the search giant remediating as many as 17 zero-day bugs in the Chrome browser that were observed to be actively exploited in the wild.
Chrome users are recommended to update to the latest version (97.0.4692.71) for Windows, Mac, and Linux by heading to Settings > Help > ‘About Google Chrome’ to mitigate any potential risk of active exploitation.