Products You May Like
By the end of 2021, there will be 12 billion connected IoT devices, and by 2025, that number will rise to 27 billion.
All these devices will be connected to the internet and will send useful data that will make industries, medicine, and cars more intelligent and more efficient.
However, will all these devices be safe? It’s worth asking what you can do to prevent (or at least reduce) becoming a victim of a cybercrime such as data theft or other forms of cybercrime in the future?
Will IoT security ever improve?
In recent years, the number of security vulnerabilities related to the Internet of Things has increased significantly.
Let us start at the very beginning — most IoT devices come with default and publicly disclosed passwords. Moreover, the fact is that there are many cheap and low-capacity Internet of Things devices that lack even the most basic security.
And that’s not all — security experts are discovering new critical vulnerabilities every day. Numerous IoT devices undergoing security audits repeatedly exhibit the same issues over and over again: remote code execution vulnerabilities at the IP or even radio level, unauthenticated or broken access control mechanisms.
Weak hardware security is one of the issues that have been discovered most frequently. By this complex term, we refer to all the attack possibilities that hackers can exploit when they have an IoT device in their hands: extracting security credentials stored in clear in the device’s memory → Using this data to breach into the servers where the device’s data is sent → sharing or selling these credentials in the “dark web” to remotely attack other devices of the same type, etc.
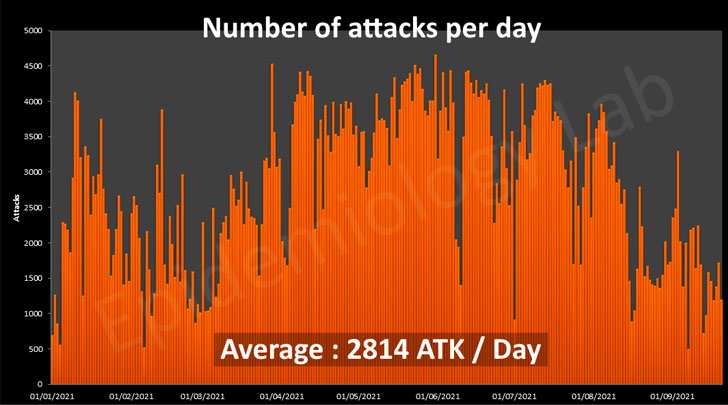
There is a real silent IoT battle going on, and tens of thousands of IoT devices have already been compromised. In order to give you an idea about the level of awareness that is on the rise, the Epidemiology Lab of Orange Cyberdefense provides us with some exciting and frightening figures: In 2019, for example, a vulnerable IoT device could be infected in less than 3 minutes, and in 2021, an IoT device is attacked on an average of 2814 times every single day by more than 100 different botnets trying to hijack it. Therefore, it is not surprising that five years after Mirai, a new IoT botnet called Meris has emerged and was used for massive DDoS attacks against Yandex, a very large Russian search engine website.
Light at the end of the tunnel
However, the situation may start to change in the near future. Recently, Orange, the largest player in the European telecommunications industry, launched an initiative called “IoT SAFE” in collaboration with Thales, a major manufacturer of electronic devices. It has been shown that collaboration between a network provider and an IoT device manufacturer significantly improves the security of IoT devices (and thus the security posture of their users).
IoT SAFE has been standardized by the GSMA as a result of a broad collaboration between device and chipset manufacturers, cloud providers, and mobile network operators.
The key idea is to use a SIM card (or an embedded SIM) as an applicative KeyStore where security keys are securely stored and dynamically managed. There is no longer a need to hand over secrets to an untrusted provider. There is also no need to add an expensive and dedicated Secure Element. In addition, there is no requirement for proprietary interfaces.
Thanks to IoT SAFE, a wide range of cryptographic services can be covered directly by the SIM card.
You may ask: Why do we stick with a SIM or an embedded SIM to secure an IoT device? It’s because SIM cards are very well protected against physical attacks. They are also standardized and can be considered reliable and well-developed chips. All IoT devices that are connected to the cellular network are usually equipped with SIM cards. With 5G for the industrial IoT just around the corner, they will surely retain their popularity. They are also inexpensive, as many mobile IoT devices are small and have cheap sensors, so a specialized chip is probably not needed.
How does it work? An example.
Moreover, this new standard also brings the benefit of overall simplicity to the table.
An example of this is “Zero Touch Provisioning.” In this use case, the network operator remotely installs and configures an instance of the IoT SAFE applet as soon as the IoT device is turned on by the user. Then, the network operator instructs the applet to create a new key pair consisting of a private key that is securely stored on the SIM card and a public key that is sent back to the server. The server generates a new client certificate and sends it back to the applet. Finally, the IoT SAFE compatible device uses this data to establish a secure connection to the cloud using a mutually authenticated TLS session.
If it is suspected that the device has been compromised, the credentials are deleted remotely over the mobile network.
There are also more complex use cases that can also be covered by IoT SAFE, such as storing critical user data on SIM or authenticating software before execution to prevent the execution of unauthorized code by IoT malware.
To a bright and secure IoT world
Orange released the first open source implementation of the standard in October 2020, based on plain C language. The implementation of this project was tested on two constrained devices using applets from two different vendors. It has been successfully integrated into two well-known public Clouds – Azure and AWS – and into Orange’s own private Live Objects Cloud. Thanks to the permissive license of this open source code, device manufacturers will be able to implement an IoT SAFE compatible device easily.
The IoT SAFE initiative has been presented at several conferences, including Java Card Forum, Global Platform, and Mobile IoT Summit. During the seminars, use cases for implementing IoT SAFE were demonstrated and discussed in detail with the IoT community. Thanks to these efforts, wolfSSL has added support for IoT SAFE to their well-known SSL/TLS library.
Of course, IoT SAFE developments and prototypes were also demonstrated at the Orange booth at this year’s Mobile World Congress. It was obvious that the IoT industry showed great interest after this demonstration. In addition to device manufacturers, chip makers and even an airplane manufacturer, many others were also excited about the potential of IoT SAFE.
One for all
It is undeniable that these connected devices do not provide adequate security protection. In the era of ever-increasing unsafe devices, there is no doubt that they pose a threat to us all. Moreover, security threats are seen as a major hindrance to the development of IoT markets. According to the Internet of Things World and Omdia, 85% of 170 industry leaders surveyed believe security concerns remain a major barrier to IoT adoption. Often, potential customers are hesitant to purchase IoT objects because they are concerned about them getting compromised.
Ultimately, only reliable and reasonably secure devices will succeed in the market and lead to reasonable IoT business growth. Therefore, the vendor community should actively contribute to IoT security to boost the IoT market and increase business opportunities.
If you want to learn more about what the hardworking Orange Cyberdefense researchers have been investigating this year, you can just hop over to the landing page of their recently published Security Navigator.