Products You May Like
A short-lived phishing campaign has been observed taking advantage of a novel exploit that bypassed a patch put in place by Microsoft to fix a remote code execution vulnerability affecting the MSHTML component with the goal of delivering Formbook malware.
“The attachments represent an escalation of the attacker’s abuse of the CVE-2021-40444 bug and demonstrate that even a patch can’t always mitigate the actions of a motivated and sufficiently skilled attacker,” SophosLabs researchers Andrew Brandt and Stephen Ormandy said in a new report published Tuesday.
CVE-2021-40444 (CVSS score: 8.8) relates to a remote code execution flaw in MSHTML that could be exploited using specially crafted Microsoft Office documents. Although Microsoft addressed the security weakness as part of its September 2021 Patch Tuesday updates, it has been put to use in multiple attacks ever since details pertaining to the flaw became public.
That same month, the technology giant uncovered a targeted phishing campaign that leveraged the vulnerability to deploy Cobalt Strike Beacons on compromised Windows systems. Then in November, SafeBreach Labs reported details of an Iranian threat actor operation that targeted Farsi-speaking victims with a new PowerShell-based information stealer designed to gather sensitive information.
The new campaign discovered by Sophos aims to get around the patch’s protection by morphing a publicly available proof-of-concept Office exploit and weaponizing it to distribute Formbook malware. The cybersecurity firm said the success of the attack can, in part, be attributed to a “too-narrowly focused patch.”
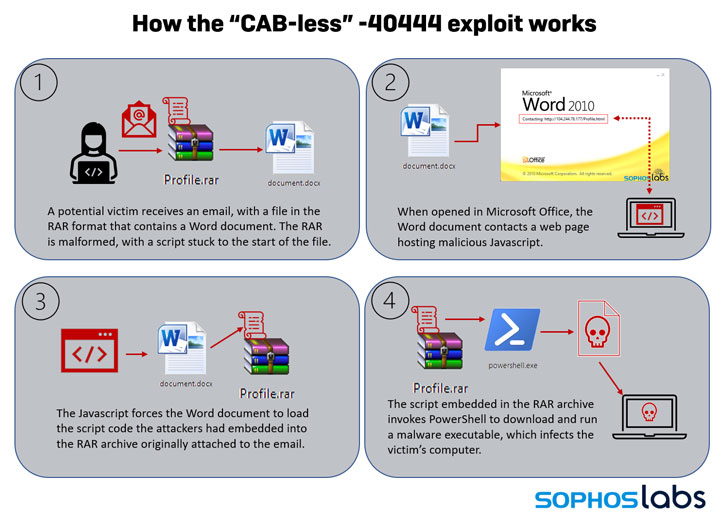
“In the initial versions of CVE-2021-40444 exploits, [the] malicious Office document retrieved a malware payload packaged into a Microsoft Cabinet (or .CAB) file,” the researchers explained. “When Microsoft’s patch closed that loophole, attackers discovered they could use a different attack chain altogether by enclosing the maldoc in a specially crafted RAR archive.”
CAB-less 40444, as the modified exploit is called, lasted for 36 hours between October 24 and 25, during which spam emails containing a malformed RAR archive file were sent to potential victims. The RAR file, in turn, included a script written in Windows Script Host (WSH) and a Word Document that, upon opening, contacted a remote server hosting malicious JavaScript.
Consequently, the JavaScript code utilized the Word Document as a conduit to launch the WSH script and execute an embedded PowerShell command in the RAR file to retrieve the Formbook malware payload from an attacker-controlled website.
As for why the exploit disappeared a little over a day in use, clues lie in the fact that the modified RAR archive files wouldn’t work with older versions of the WinRAR utility. “So, unexpectedly, in this case, users of the much older, outdated version of WinRAR would have been better protected than users of the latest release,” the researchers said.
“This research is a reminder that patching alone cannot protect against all vulnerabilities in all cases,” SophosLabs Principal Researcher Andrew Brandt said. “Setting restrictions that prevent a user from accidentally triggering a malicious document helps, but people can still be lured into clicking the ‘enable content’ button.”
“It is therefore vitally important to educate employees and remind them to be suspicious of emailed documents, especially when they arrive in unusual or unfamiliar compressed file formats from people or companies they don’t know,” Brandt added.