Products You May Like
The U.S. government on Monday charged a Ukrainian suspect, arrested in Poland last month, with deploying REvil ransomware to target multiple businesses and government entities in the country, including perpetrating the attack against software company Kaseya, marking the latest action to crack down on the cybercrime group and curb further attacks.
According to unsealed court documents, 22-year-old Yaroslav Vasinskyi is alleged to have been part of the ransomware operation at least since March 2019 and deployed about 2,500 attacks against businesses worldwide. Vasinskyi (aka Profcomserv, Rabotnik, Rabotnik_New, Yarik45, Yaraslav2468, and Affiliate 22) was apprehended at the Polish border on October 8 after an international arrest warrant was issued at the behest of U.S. authorities.
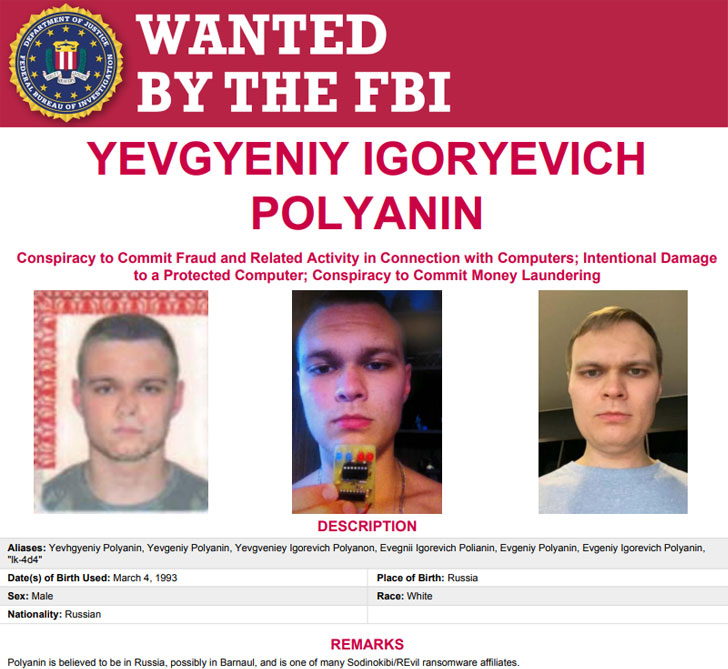
In another major development, the Justice Department disclosed the seizure of $6.1 million in alleged ransomware payments received by Russian national Yevgeniy Polyanin, who is currently at large and has been accused of conducting REvil ransomware attacks against multiple businesses and government entities in Texas dating back to August 16, 2019.
Vasinskyi and Polyanin have been charged with conspiracy to commit fraud and related activity in connection with computers, substantive counts of damage to protected computers, and conspiracy to commit money laundering. If convicted of all counts, both the defendants face a maximum penalty of 115 and 145 years in prison, respectively.
“Ransomware can cripple a business in a matter of minutes. These two defendants deployed some of the internet’s most virulent code, authored by REvil, to hijack victim computers,” said Acting U.S. Attorney Chad E. Meacham for the Northern District of Texas in a statement. “The Department will delve into the darkest corners of the internet and the furthest reaches of the globe to track down cyber criminals.”
The latest development comes amid a flurry of law enforcement activity orchestrated by Europol under Operation GoldDust, which resulted in the arrests of six other REvil ransomware affiliates besides Vasinskyi across Romania, Kuwait, and South Korea. The REvil ransomware gang is believed to have netted more than $200 million since it started operations and globally encrypted at least 175,000 computers.
Coinciding with the arrests, the U.S. government also announced it’s offering a reward of up to $10 million for information leading to the identification or location of key leaders behind the REvil ransomware, in addition to paying out up to $5 million for information leading to the arrest or conviction of individuals, located in any country, participating in REvil ransomware attacks.
Furthermore, the U.S. Treasury Department imposed sanctions against Chatex, a virtual currency exchange, for “facilitating financial transactions for ransomware actors,” following a similar designation against Russian cryptocurrency exchange SUEX in September 2021.
“Analysis of Chatex’s known transactions indicate that over half are directly traced to illicit or high-risk activities such as darknet markets, high-risk exchanges, and ransomware,” the department said. “Chatex has direct ties with SUEX OTC, S.R.O. (Suex), using Suex’s function as a nested exchange to conduct transactions.”
The arrests and the sanctions are part of a larger push to fight against ransomware attacks, which have accelerated in frequency and scale this year, putting critical infrastructure at risk and causing millions in damages, prompting international authorities to effectively respond to such attacks, while also countering the abuse of cryptocurrency channels to launder ransom payments.