Products You May Like
REvil, the notorious ransomware gang behind a string of cyberattacks in recent years, appears to have gone off the radar once again, a little over a month after the cybercrime group staged a surprise return following a two-month-long hiatus.
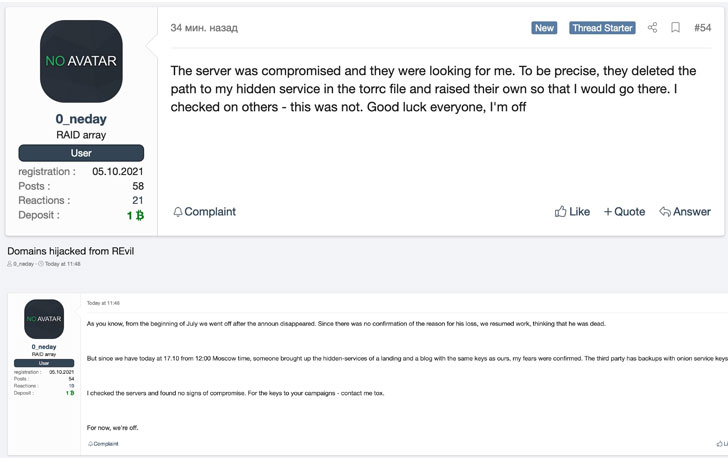
The development, first spotted by Recorded Future’s Dmitry Smilyanets, comes after a member affiliated with the REvil operation posted on the XSS hacking forum that unidentified actors had taken control of the gang’s Tor payment portal and data leak website.
“The server was compromised and they were looking for me. To be precise, they deleted the path to my hidden service in the torrc file and raised their own so that I would (sic) go there. I checked on others – this was not. Good luck everyone, I’m off,” user 0_neday said in the post.
As of writing, it isn’t clear exactly who was behind the compromise of REvil’s servers, although it wouldn’t be entirely surprising if law enforcement agencies played a role in bringing down the domains.
The Russia-linked ransomware group attracted major scrutiny following its attacks on JBS and Kaseya earlier this year, prompting it to take its darknet sites offline in July 2021. But on September 9, 2021, REvil made an unexpected return, resurfacing both its data leak site as well as payment and negotiation portals back online.
Last month, the Washington Post reported that the U.S. Federal Bureau of Investigation (FBI) held back from sharing the decryptor with the victims of Kaseya ransomware attack for nearly three weeks, which it obtained from accessing the group’s servers, as part of a plan to disrupt the gang’s malicious activities. “The planned takedown never occurred because in mid-July REvil’s platform went offline — without U.S. government intervention — and the hackers disappeared before the FBI had a chance to execute its plan,” the report added.
A universal decryptor was eventually shared by Romanian cybersecurity firm Bitdefender in late July after acquiring the digital key from a “law enforcement partner.”
While it’s not uncommon for ransomware groups to evolve, splinter, or reorganize under new names, the criminal field has increasingly come under the lens for striking critical infrastructure, even as more cybercriminals are recognizing the profitability of ransomware, in part bolstered by the unregulated cryptocurrency landscape, thus enabling threat actors to extort victims for digital payments with impunity.