Products You May Like
Microsoft on Monday revealed that its Azure cloud platform mitigated a 2.4 Tbps distributed denial-of-service (DDoS) attack in the last week of August targeting an unnamed customer in Europe, surpassing a 2.3 Tbps attack stopped by Amazon Web Services in February 2020.
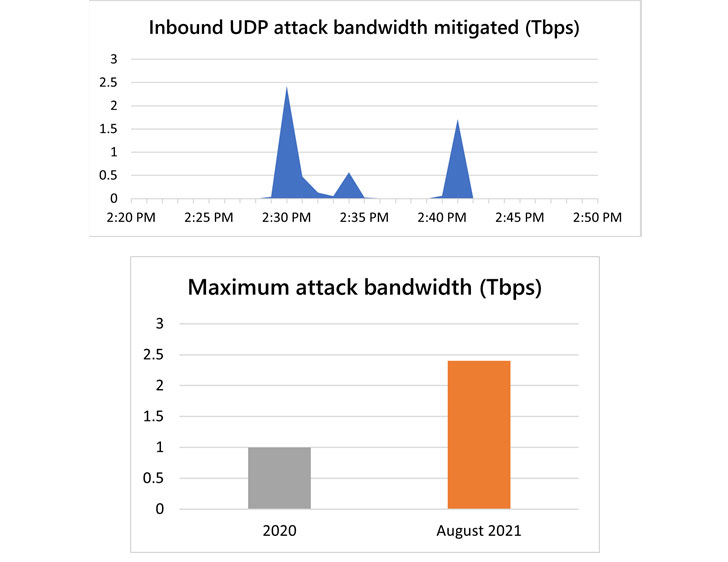
“This is 140 percent higher than 2020’s 1 Tbps attack and higher than any network volumetric event previously detected on Azure,” Amir Dahan, senior program manager for Azure Networking, said in a post, calling it a “UDP reflection” lasting for about 10 minutes.
Reflected amplification attacks are a type of denial of service attacks wherein a threat actor takes advantage of the connectionless nature of UDP protocol with spoofed requests so as to overwhelm a target server or network with a flood of packets, causing disruption or rendering the server and its surrounding infrastructure unavailable.
The attack is said to have originated from a botnet of approximately 70,000 compromised devices primarily located across the Asia-Pacific region, such as Malaysia, Vietnam, Taiwan, Japan, and China, as well as the U.S.
Microsoft said it observed three short-lived bursts, each ramping up in seconds to terabit volumes — the first at 2.4 Tbps, the second at 0.55 Tbps, and the third at 1.7 Tbps.
News of the DDoS attack comes a month after Russian internet giant Yandex became the target of a record-breaking distributed denial-of-service (DDoS) attack by a new botnet called Mēris, which battered the company’s web infrastructure with millions of HTTP requests, before hitting a peak of 21.8 million requests per second (RPS).
“Bad actors, now more than ever, continuously look for ways to take applications offline,” Dahan said. “Attacks of this size demonstrate the ability of bad actors to wreak havoc by flooding targets with gigantic traffic volumes trying to choke network capacity.”